There’s a common denominator between the surges of phishing email that continue to plague consumers, businesses and government agencies around the globe and the social media-fueled propaganda campaigns Russia has leveraged to undermine democratic elections in Europe and the United States. Neither would be doable without botnets as they exist today. For most people, the power and […]
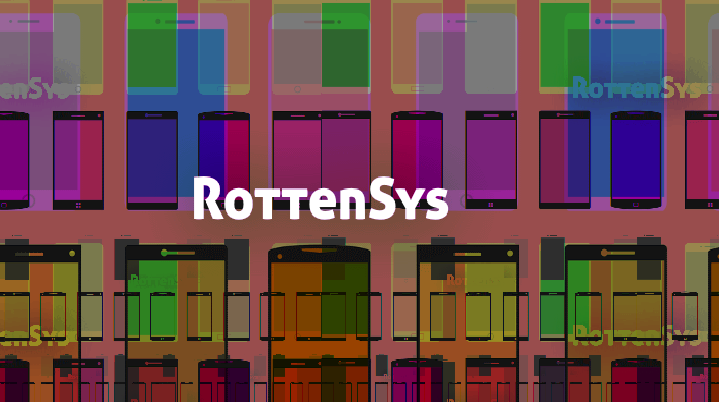
Pre-Installed Malware Found On 5 Million Popular Android Phones
Security researchers have discovered a massive continuously growing malware campaign that has already infected nearly 5 million mobile devices worldwide. Dubbed RottenSys, the malware that disguised as a ‘System Wi-Fi service’ app came pre-installed on millions of brand new smartphones manufactured by Honor, Huawei, Xiaomi, OPPO, Vivo, Samsung and GIONEE—added somewhere […]
GANDCRAB RANSOMWARE CROOKS TAKE AGILE DEVELOPMENT APPROACH
Earlier this month, command-and-control servers tied to the fast-growing GandCrab ransomware campaigns were seized by Romanian Police and Europol. But, criminals behind GandCrab don’t appear phased by the setback and have already tweaked the malware to keep ransomware payment coming in. According to new research by Check Point, the group […]
Hacking SAP CRM by chaining 2 vulnerabilities in SAP NetWeaver AS Java
Security experts at ERPScan explained that chaining 2 flaws recently patched it is possible to hack SAP CRM systems and access sensitive data. Security experts at ERPScan discovered that chaining the exploits for two security vulnerabilities in SAP NetWeaver Application Server Java patched last month, an attacker can hack customer […]
Hackers can steal data from Air-Gapped PCs with microphones & speakers
A research team from Israel’s Ben-Gurion University of the Negev ‘s cybersecurity research center has discovered a new way of data extraction from air-gapped computers via using passive devices like earbuds, earphones, headphones, and speakers. Now, the same research center has claimed to be able to use computer speakers and […]
Chinese Crooks Assembling Massive Botnet of Nearly 5 Million Android Devices
A Chinese malware operation is currently building a massive botnet of nearly 5 million Android smartphones using a strain of malware named RottenSys. In its current form, RottenSys is being used to aggressively display ads on users’ devices, but researchers from security firm Check Point have found evidence that crooks […]
Hacking group threatens researchers’ lives after they discover attack servers
A hacking group commonly linked to the Iranian government threatened to kill security researchers who came across their cyber espionage operation, according to a new report. Researchers with multinational cybersecurity company Trend Micro were probing a server that appeared connected to a possible data breach in the Middle East when they received a […]
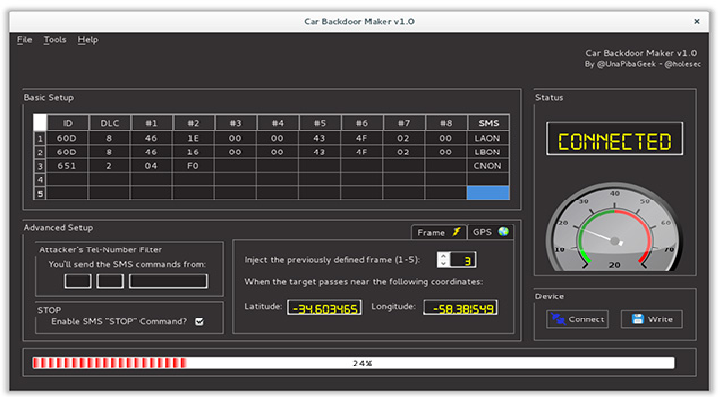
Hardware Backdoor for Remote Control over Cars
A modern car’s resistance to hacking has been once again tested by security researchers, who have built a device to spy on internal communications and deliver commands to the vehicle. The piece of hardware has GSM support, allowing an attacker to activate available payloads by sending an SMS from anywhere […]
Let’s Encrypts Now Offers Free Wildcard SSL Certificates Using ACMEv2
Let’s Encrypt announced yesterday that their ACMEv2 API is now live and with it comes the ability for users to get free wildcard certificates. This has been a long awaited feature as wildcard domain certificates are much more expensive then regular single host certificates and it also makes managing SSL certs […]
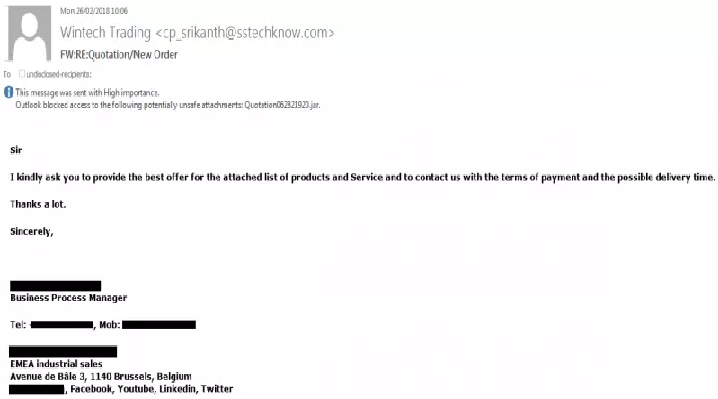
Qrypter RAT hits 243 organizations worldwide in February
Qrypter RAT hits 243 organizations worldwide in February 2018, its popularity in the cybercrime ecosystem continues to increase. A new strain of remote access Trojan dubbed Qrypter RAT (aka Qarallax, Quaverse, QRAT, and Qontroller) hit hundreds of organizations worldwide. The malware was spotted by security firm Forcepoint, it has been around […]