Two months after the release of the security updates for the drupalgeddon2 flaw, experts continue to see vulnerable websites running on flawed versions of Drupal that hasn’t installed security patches.
In March, the Drupal developers Jasper Mattsson discovered a “highly critical” vulnerability, tracked as CVE-2018-7600, aka drupalgeddon2, affecting Drupal 7 and 8 versions.
Both Drupal 8.3.x and 8.4.x are not supported, but due to the severity of the flaw, the Drupal Security Team decided to address it with specific security updates that were issued a few days later.
The vulnerability that could be exploited by an attacker to run arbitrary code on the CMS core component and take over a website just by accessing an URL.
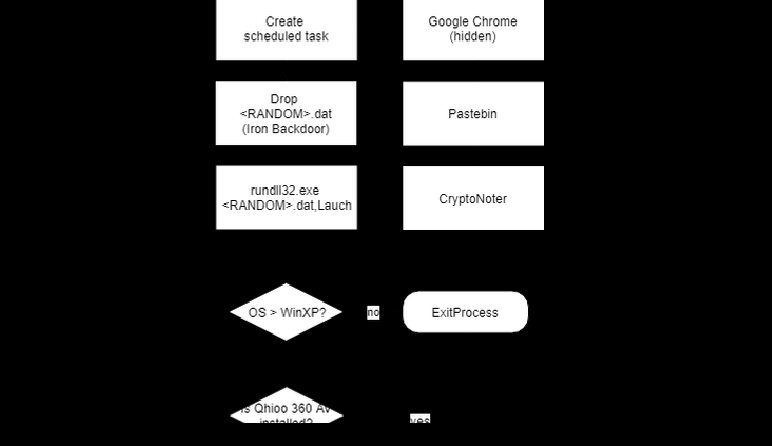
After the publication of a working Proof-Of-Concept for Drupalgeddon2 on GitHub experts started observing attackers using it to deliver backdoors and crypto miners.
Two months after the release of the security updates, experts continue to see vulnerable websites running on flawed versions of Drupal that hasn’t installed security patches.
According to the security researcher Troy Mursch, there are over 115,000 Drupal sites that have installed security patched for drupalgeddon2 vulnerability.
The experts scanning the Internet for websites running Drupal 7.x CMS version found over 500,000 sites, 115,070 of them running outdated versions of the popular CMS that were vulnerable to the Drupalgeddon 2 flaw. The scan didn’t search for 6.x and 8.x sites.
“How many Drupal sites are vulnerable?To find the answer, I began by looking for sites using Drupal 7. This is the most widely used version, per Drupal’s core statistics. Using the source code search engine PublicWWW, I was able to locate nearly 500,000 websites using Drupal 7.” states a report published by Mursch.
“Upon completion of the scan I was able to determine:
115,070 sites were outdated and vulnerable.
134,447 sites were not vulnerable.
225,056 sites I could not ascertain the version used.”
Drupalgeddon2
The researcher found numerous vulnerable sites in the Alexa Top 1 Million, the list includes major US educational institutions, government organizations around the world, a large television network, a multinational mass media and entertainment conglomerate, and two major computer hardware manufacturers.
The expert shared the list of vulnerable websites with US-CERT and other CERT teams worldwide.
Mursch confirmed that cryptojacking campaigns are continuing even after his first report,
“While scanning for vulnerable sites, I discovered a new cryptojacking campaign targeting Drupal sites. One of the affected sites was a police department’s website in Belgium. This campaign uses the domain name upgraderservices[.]cf to inject Coinhive.” added the expert.
The expert published a Google Docs spreadsheet to track the original cryptocurrency mining campaign, the document includes now data on several different campaigns he discovered.
To read the original article:
https://securityaffairs.co/wordpress/73219/hacking/drupalgeddon2-vulnerable-sites.html