Security researchers from AlienVault have discovered a new malware strain named GZipDe that appears to be part of a targeted attack —most likely a cyber-espionage campaign.
Researchers discovered this new malware earlier this week after a user from Afghanistan uploaded a boobytrapped Word document on VirusTotal.
The document contained text taken from an article published last month about the Shanghai Cooperation Organization Summit, a political conference on Eurasian political, economic, and security topics.
Malware most likely used for cyber-espionage
Because VirusTotal hides precise information about the source of the upload, the target of this attack is unknown.
« We’ve only seen one sample of the malware, » Chris Doman, a security researcher with AlienVault told Bleeping Computer.
« It seems very targeted, » Doman added. « Given the decoy document is in English and uploaded from Afghanistan, it may have been targeting someone in an embassy or similar there. »
A GZipDe infection is a multi-step process
This Word file was just the first step in a multi-step infection process, which Doman detailed in a report published yesterday.
The document lured users into enabling macros, which then executed a Visual Basic script, which ran some PowerShell code, which downloaded a PE32 executable, which later dropped the actual malware —GZipDe.
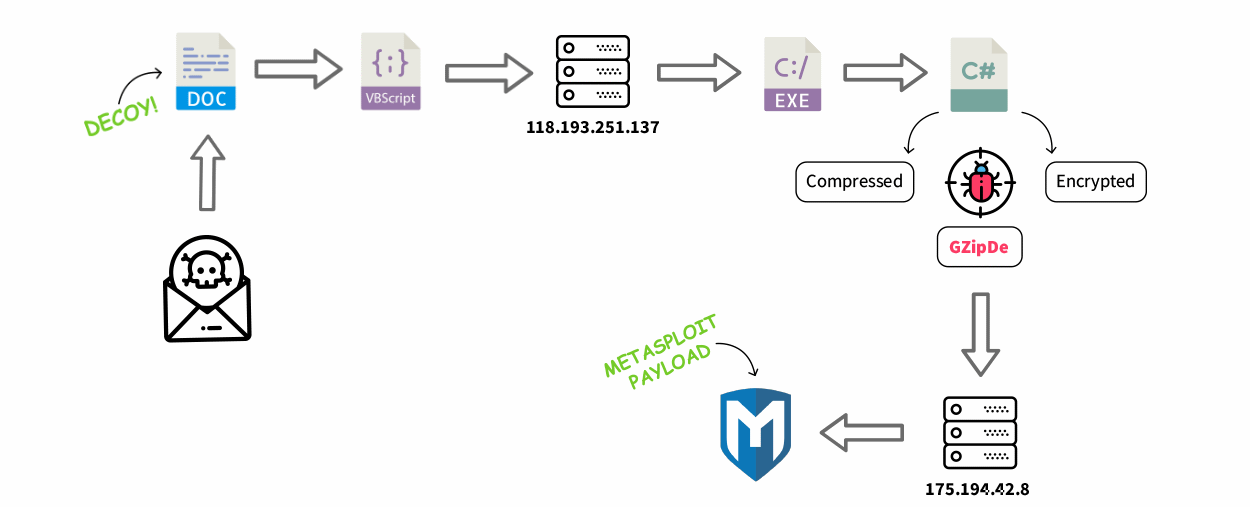
According to Doman, GZipDe is coded in .NET, and uses « a custom encryption method to obfuscate process memory and evade antivirus detection. »
GZipDe is a « downloader, » meaning its role is to fetch another more potent threat from a remote server.
This second server was down when researcher found the malware, and under normal, the investigation would have been over at this phase. Fortunately, the AlienVault team got lucky because IoT search engine Shodan had indexed the server and « recorded it serving a Metasploit payload. »
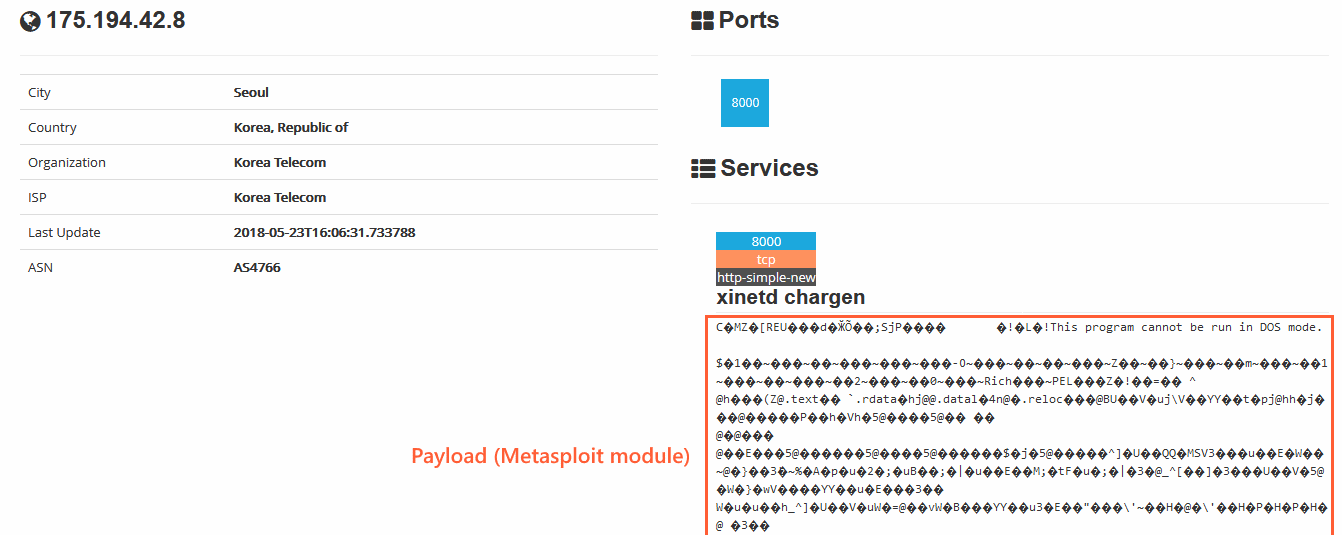
GZipDe drops Metasploit-based backdoor
Analyzing the logged shellcode, the AlienVault team determined this was a Metasploit module. Metasploit is a framework used by security researchers for penetration tests, and this particular module was developed to work as a backdoor.
« For example, it can gather information from the system and contact the command and control server to receive further commands, » the AlienVault team says.
« This shellcode loads the entire DLL into memory, so it’s able to operate while writing no information into the disk. […] From this point, the attacker can transmit any other payload in order to acquire elevated privileges and move within the local network. »
The use of Metasploit instead of a custom malware strain isn’t a new tactic. In the past few years, crooks have been slowly migrating from developing custom malware to using ready-made tools, such as Metasploit or Cobalt Strike
« Essentially it makes attribution more difficult and they will use the minimum required effort to achieve their objectives, » Doman told Bleeping Computer.
To read the original article:https://www.bleepingcomputer.com/news/security/new-gzipde-malware-drops-metasploit-backdoor/