An attack called Mongo Lock is targeting remotely accessible and unprotected MongoDB databases, wiping them, and then demanding a ransom in order to get the contents back.
While this new campaign is using a name to identify itself, these types of attacks are not new and MongoDB databases have been targeted for a while now. These hijacks work by attackers scanning the Internet or using services such as Shodan.io to search for unprotected MongoDB servers. Once connected, the attackers may export the databases, delete them, and then create a ransom note explaining how to get the databases back.
According to security researcher Bob Diachenko who discovered the new Mongo Lock campaign, the attackers will connect to an unprotected database and delete it. In its place, the attackers will leave a new database called « Warning » with a collection inside it named « Readme ».
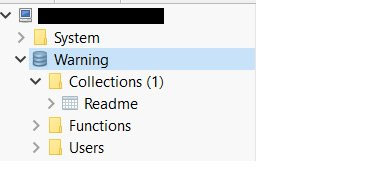
The Readme collection will contain a ransom note that explains that the database has been encrypted and that the victims need to pay them a ransom to get it back. In the Mongo Lock campaign, as shown below, the attackers do not leave a bitcoin address, but rather direct the victim’s to contact them via email.
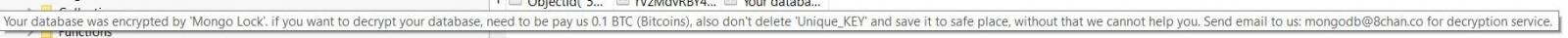 ote (Click to enlarge)
ote (Click to enlarge)The ransom note for the Mongo Lock attack reads:
Your database was encrypted by 'Mongo Lock'. if you want to decrypt your database, need to be pay us 0.1 BTC (Bitcoins), also don't delete 'Unique_KEY' and save it to safe place, without that we cannot help you. Send email to us: mongodb@8chan.co for decryption service.Other attacks will display the bitcoin address that should be used for payment before contacting the attackers via the included email
{
"BitCoin" : "3FAVraz3ovC1pz4frGRH6XXCuqPSWeh3UH",
"eMail" : "dbbackups@protonmail.com",
"Exchange" : "https://www.coincola.com/",
"Solution" : "Your Database is downloaded and backed up on our secured servers. To recover your lost data: Send 0.6 BTC to our BitCoin Address and Contact us by eMail with your server IP Address and a Proof of Payment. Any eMail without your server IP Address and a Proof of Payment together will be ignored. We will drop the backup after 24 hours. You are welcome!"
}
While the ransom note claims that the attackers are exporting the database first before deleting it, it is not known if they are doing that in ever case.
Victims are paying ransoms
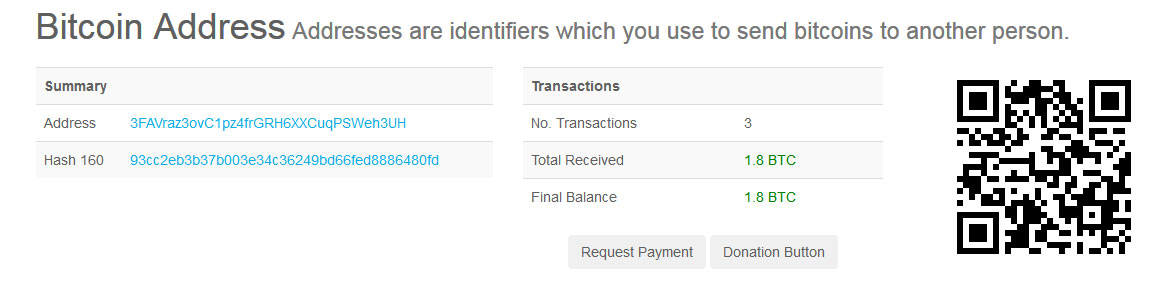
When looking up some of the bitcoin addresses used in recent MongoDB attacks, victims have been paying the ransoms.
For example, the bitcoin address 3FAVraz3ovC1pz4frGRH6XXCuqPSWeh3UH, which has been used often, has had 3 ransom payments for a total of 1.8 bitcoins. This is equivalent to a little over $11,000 USD at the current value of bitcoins.
Scripts do not always work
According to Diachenko, it appears that the attackers are using a script that automates the process of accessing a MongoDB database, possibly exporting it, deleting the database, and then creating the ransom note.
Diachenko has noticed, though, that this script sometimes fails and the data is still available to the user even though a ransom note is created.
« What is also notable – seems like they have automated this process and sometimes script fails and data is still there, but with a note as well » Diachenko told BleepingComputer.
Properly securing a MongoDB database.
These attacks are able to occur because the MongoDB database is remotely accessible and not properly secured. This means that these attacks are easily prevented by following fairly simple steps in securing the database instance.
MongoDB has a good article on how to properly secure a database and even offers a security checklist for administrators to follow. The two most important steps that will prevent these types of attacks are to enable authentication and to not allow these databases to be remotely accessible.
