More than 95,000 servers could still be vulnerable to being abused to launch massive distributed denial-of-service attacks.
The risk comes via Memcached, an open source utility designed to cache in RAM frequently used web pages.
The web page caching utility was never designed to be internet-accessible and requires no authentication to access. But some administrators – as well as some Linux instances by default – have left TCP or UDP port 11211 open to internet-borne requests.
Attackers have begun demonstrating how badly servers with misconfigured Memcached can be abused.
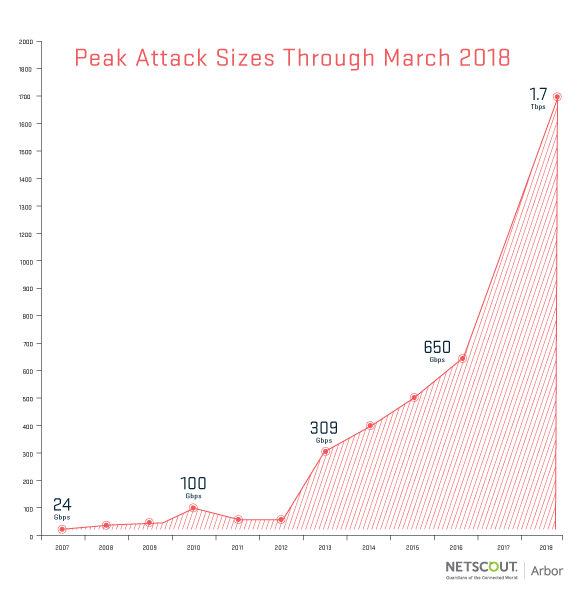 Source: Arbor Networks
Source: Arbor NetworksPopular code-sharing website GitHub reported that on Feb. 28, it was hit by a massive DDoS attack that left its site unavailable or intermittently unreachable, but only for 10 minutes. Akamai, which provides DDoS defenses for GitHub, clocked the attack’s peak at a whopping 1.35 terabits per second.
On Monday, however, DDoS defense firm Arbor Networks, part of Netscout, reported that one of its customers, a U.S.-based service provider, was hit by a 1.7 Tbps reflection/amplification attack « based on the same Memcached reflection/amplification attack vector that made up the Github attack, » according to Arbor’s Carlos Morales, who says his firm successfully repelled the disruption.
Arbor says the biggest-ever previous DDoS attack that it logged was in the summer of 2016, when a Brazilian customer was hit with a 650 Gbps attack.
« The Memcached UDP protocol [is] a fine example of double trouble with potential for severe operational impact. »
« Memcached servers are now being used as reflectors/amplifiers to launch extremely high-volume UDP reflection/amplification attacks, » Morales says in a March 1 blog post. « They are proving especially effective because Memcached servers have high-bandwidth access links and reside on networks with high-speed transit uplinks. This makes Memcached servers ideal for use in high-bandwidth reflection/amplification DDoS attacks. »
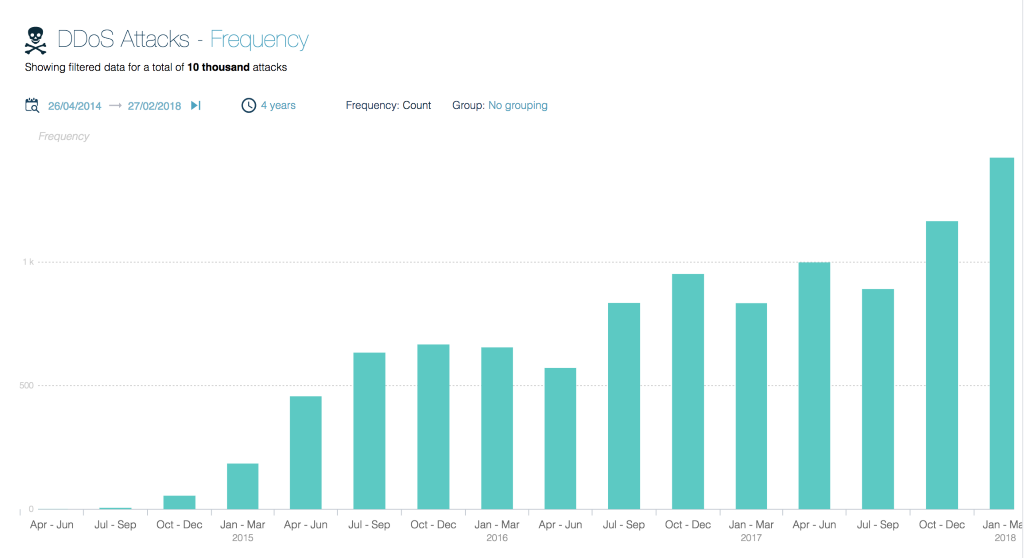 Frequency of DDoS attacks from April 2014 to Feb. 2018 against customers of Arbor Networks. Irrespective of frequency, the firm says attack intensity has spiked in recent months. (Source: Arbor Networks)
Frequency of DDoS attacks from April 2014 to Feb. 2018 against customers of Arbor Networks. Irrespective of frequency, the firm says attack intensity has spiked in recent months. (Source: Arbor Networks)
Johannes B. Ullrich, dean of research at SANS Technology Institute, describes the Memcached abuse as « a classic reflective amplified DDoS attack, » adding that « luckily, it isn’t too hard to block. »
Here’s how: « You should see traffic *from* port 11211 if you are hit by this attack, » he says in a blog post. « Blocking all traffic from port 11211 should be possible, as all modern operating systems tend to use a source port higher than that for client connections. But given the traffic volumes people are seeing, you will likely need help « upstream » or from an anti-DDoS company. »
Some DDoS extortionists are now threatening to unleash Memcached-enabled disruptions on victims unless they pay ransoms of 50 monero – aka XMR – cryptocurrency, worth about $16,000. But Ullrich says all attacks seen to date have directed victims to pay into a single monero wallet address, meaning that these opportunistic criminals would have no way to verify which victims paid or did not pay.
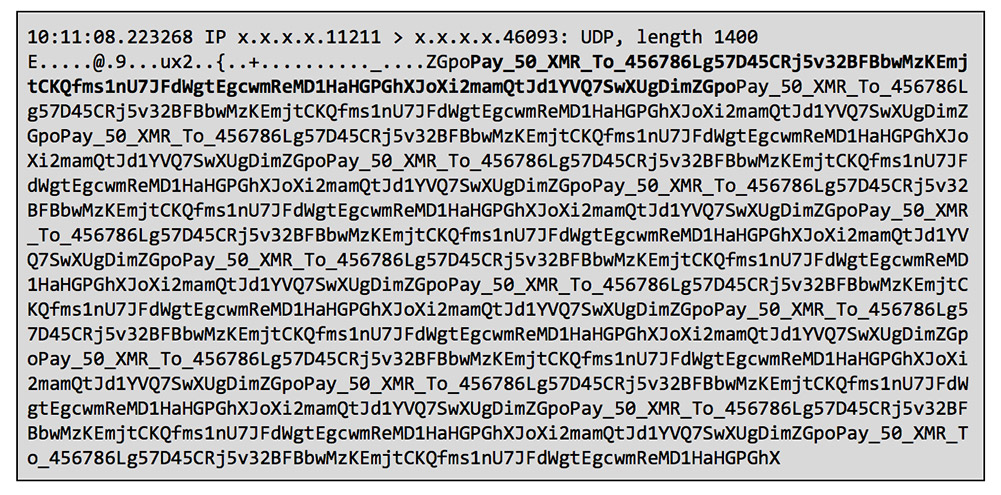 Memcached DDoS packet with request for payment in monero, aka XMR, cryptocurrency. (Source: Akamai)
Memcached DDoS packet with request for payment in monero, aka XMR, cryptocurrency. (Source: Akamai)
The Power of Amplification
Memcached offers massive bang for attackers’ buck. For starters, it can be abused to inject massive keys – up to 50 kilobytes – and attackers can then use IP spoofing to create DDoS attacks with a massive rate of amplification.
The U.S. Computer Emergency Readiness Team has updated its alert on UDP-based amplification attacks, originally released in 2014, to include Memcached-based reflection DDoS attacks via UDP/TCP port 11211. It warns that abusing Memcached can result in attacks being amplified by 10,000 to 51,000 times.
To read the original article:
https://www.bankinfosecurity.com/memcached-ddos-attacks-95000-servers-vulnerable-to-abuse-a-10705
