Today a reader sent me info regarding the LockCrypt Ransomware being actively distributed over hacked remote desktop services. This variant, when installed, will encrypt a victim’s files and then append the .1btc extension to encrypted file names.
For those not familiar with the LockCrypt Ransomware, AlienVault has a good writeup about an older version. In summary, attackers will look for accessible computers running Remote Desktop Services and try to brute force login credentials. Once they are able to login to a computer, they will execute the ransomware on as many computers in the network as they are able to access.
The ransomware developers then provide contact info where a victim can pay a certain price for a single machine decryption or a reduced price if decrypting multiple machines.
This version works the same way, but the developers have changed the extension appended to file names and are using different contact email addresses. This variant has been distributed since the end of December 2017 and when encrypting files will base64 encode the file name and then append the .1btc exension to the filename. You can see an example of this from the image sent to BleepingComputer.
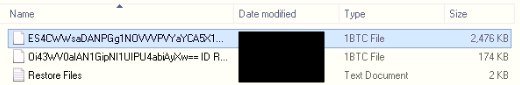
LockCrypt will then create ransom notes on the infected machine with the file name Restore Files.TxT. These ransom notes contain a unique victim ID and instructions to email Jacob_888jk@aol.com or Jacob_888jk@bitmessage.ch in order to receive payment instructions.
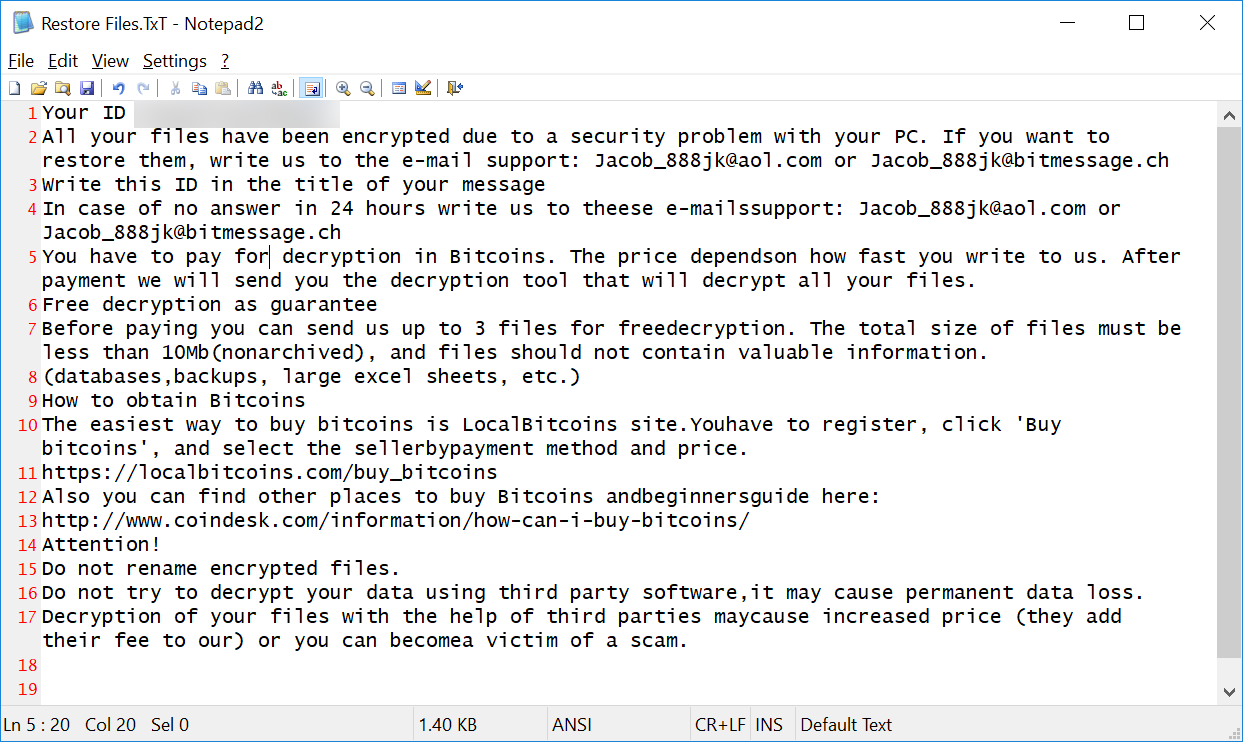
It is currently unknown how much the attackers are asking for a ransom payment, but based on the extension it may be 1 bitcoin per machine.
Finally, LockCrypt adds a legal notice to the victim’s machine that displays an alert about the computer being encrypted before a user even logs in.
To read the original article:https://www.bleepingcomputer.com/news/security/lockcrypt-1btc-variant-installed-over-hacked-remote-desktop-services/
