If you’ve been following the infosec Twitter community for the last few days, you couldn’t ignore the constant talk about the massive scans currently taking place online, carried out by a Hajime IoT botnet looking to mass-infect unpatched MikroTik devices.
All of the hoopla started on Sunday, March 25, when suspicious scans for port 8291 popped up out of the blue on everyone’s honeypots.
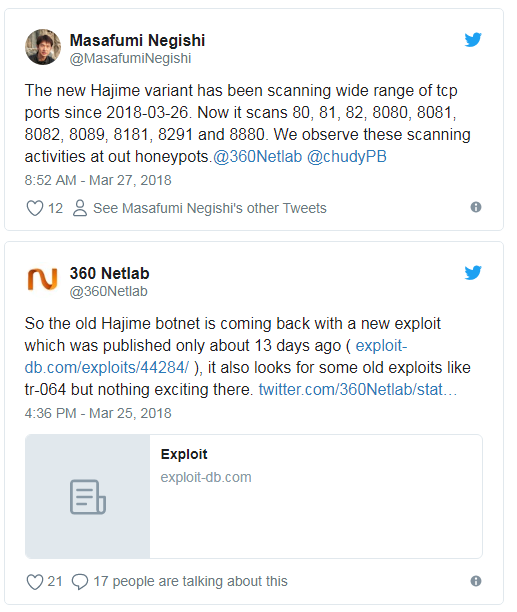
The scans only continued in the following days, showing no sign of abating, and attracting attention from security researchers from all over the globe.
The attention was warranted as the scans weren’t something small, and continued at an intensive rate. The first to spot the scans were researchers from Qihoo 360’s Netlab team, who said today this Hajime botnet performed over 860,000 scans in the last three days, albeit they couldn’t tell how many of these scans were also successful infections.
Attackers use eChimay Red exploit against MikroTik devices
The exploit attackers were trying to use was a vulnerability known as « Chimay Red, » a bug that affects MikroTik RouterOS firmware 6.38.4 and earlier, and allows attackers to execute code and take over the device.
This is the same flaw that was included in the WikiLeaks « Vault 7 » leak of alleged CIA hacking tools, and the same flaw that some jokesters used during the past year to deface MikroTik routers by changing hostnames of vulnerable devices to all sorts of expressions that included the word « hacked. »
But this time around, attackers didn’t joke around and they installed the Hajime bot, a strain of IoT malware known primarily for building giant botnets, with the last one reaching over 300,000 devices in the spring of 2017.
MikroTik firmware patch available for almost a year
These massive scans didn’t go unnoticed on MikroTik’s side either. Users reported the scans on MikroTik’s forums, and the company’s engineers looked into the attacks.
« It has come to our attention that a mass scan for open ports 80/8291(Web/Winbox) is taking place, » said MikroTik on Twitter. « To be safe, firewall these ports and upgrade RouterOS devices to v6.41.3 (or at least, above v6.38.5).
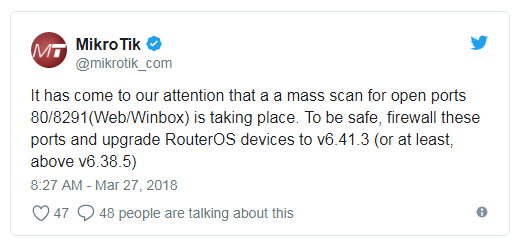
As MikroTik points out, the Chimay Red vulnerability was fixed last year, when the company’s engineers released RouterOS firmware version 6.38.5.
Bot has simple scan & infect mechanism
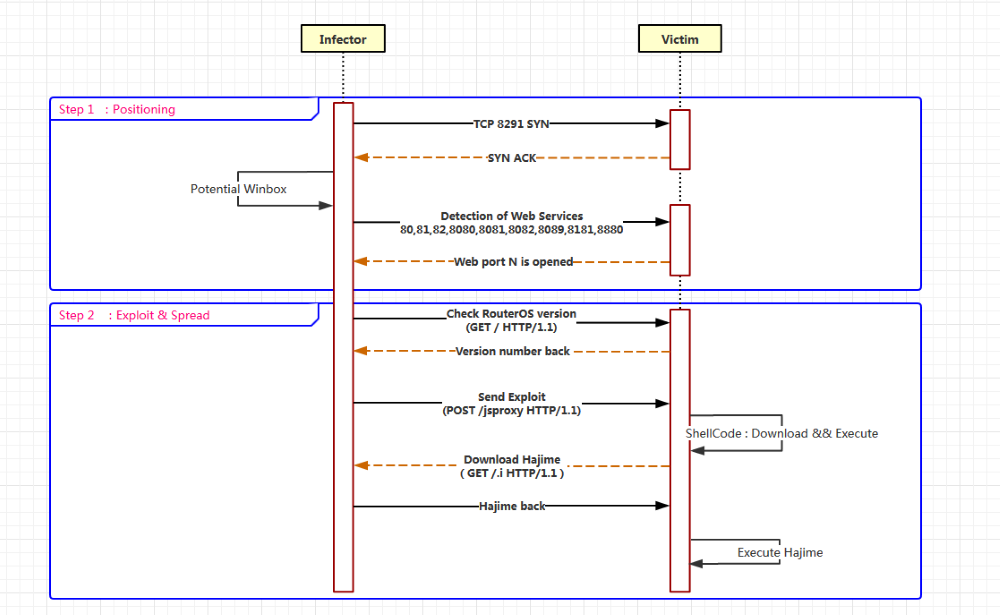
As for the Hajime bot’s infection attempts, this follows a quite simplistic pattern. Other Hajime infected bots scan random IP addresses on port 8291. This initial scan is to determine if the remote IP is running a MikroTik device.
Once the bot has identified one of such devices, it then tries to infect the device with a public exploit package sent via one of the following ports: 80, 81, 82, 8080, 8081, 8082, 8089, 8181, and 8880.
Once a new device has been infected with a Hajime bot, this new device also starts scanning to infect other MikroTik routers.
It is worth mentioning that in the past, the Hajime IoT botnet was never used for massive DDoS attacks, and its existance was a mystery for many researchers, as the botnet only gathered infected devices but almost never did anything with them (except scan for other vulnerable devices).
IOCs and technical write-ups about this new bot are also available, authored by the research teams from Netlab and Radware.
To read the original article:
https://www.bleepingcomputer.com/news/security/hajime-botnet-makes-a-comeback-with-massive-scan-for-mikrotik-routers/
