Two days after Cisco patched a severe vulnerability in a popular brand of SOHO routers, and one day after the publication of proof-of-concept code, hackers have started scans and attacks exploiting the said security bug to take over unpatched devices.
The vulnerability, tracked as CVE-2019-1663, was of note when it came out on February 27 because it received a severity score from the Cisco team of 9.8 out of a maximum of 10.
It received such a high rating because the bug is trivial to exploit and does not require advanced coding skills and complicated attack routines; it bypasses authentication procedures altogether; and routers can be attacked remotely, over the internet, without attackers needing to be physically present on the same local network as the vulnerable device.
Affected models include the Cisco RV110, RV130, and RV215, all of which are WiFi routers deployed in small businesses and residential homes.
This means that the owners of these devices won’t likely be keeping an eye on Cisco security alerts, and most of these routers will remain unpatched –unlike in large corporate environments where IT personnel would have already deployed the Cisco fixes.
According to a scan by cyber-security firm Rapid7, there are over 12,000 of these devices readily available online, with the vast majority located in the US, Canada, India, Argentina, Poland, and Romania.
All of these devices are now under attack, according to cyber-security firm Bad Packets, which reported detecting scans on March 1.
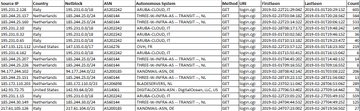
The company detected hackers scanning for these types of routers using an exploit that was published a day earlier on the blog of Pen Test Partners, a UK-based cyber-security firm.
It was one of the Pen Test Partners’ researchers, together with two other Chinese security experts, who found this particular vulnerability last year.
In its blog post, Pen Test Partners blamed the root cause of CVE-2019-1663 on Cisco coders using an infamously insecure function of the C programming language -namely strcpy (string copy).
The company’s blog post included an explanation of how using this C programming function left the authentication mechanism of the Cisco RV110, RV130, and RV215 routers open to a buffer overflow that allowed attackers to flood the password field and attach malicious commands that got executed with admin rights during authentication procedures.
Attackers who read the blog post appear to be using the example provided in the Pen Test Partners article to take over vulnerable devices.
Any owner of these devices will need to apply updates as soon as possible. If they believe their router has already been compromised, reflashing the device firmware is recommended.
Source: https://www.zdnet.com/article/hackers-have-started-attacks-on-cisco-rv110-rv130-and-rv215-routers/
