Google rolled out today new security features for G Suite, its collection of enterprise, cloud computing, productivity, and collaboration tools.
While several of the G Suite services received improvements, the most interesting additions have been made to Gmail for Business, the Google service that allows companies to use Gmail as their internal email service over a custom domain.
Starting today, G Suite admins can enable new AI-powered security features inside the G Suite backend. These features have been built to detect and alert users of emails carrying potential malware and emails that are part of spear-phishing attempts.
More specifically, Google will start flagging emails carrying encrypted files, scripting files, emails containing shortened URLs, and emails that appear to come from spoofed domains or using spoofed sender names.
Here are the new features that G Suite admins can tweak in their Gmail control panels, complete with their location and a helpful image.
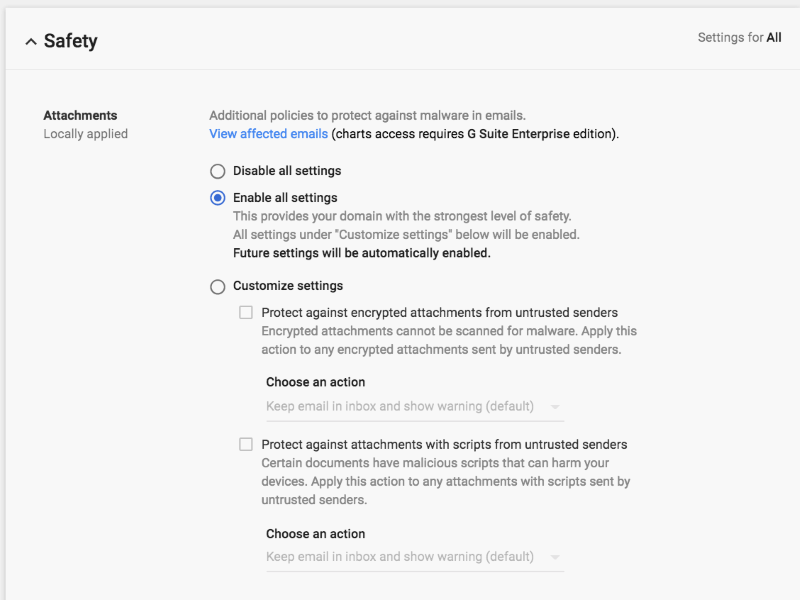
Apps > G Suite > Gmail > Safety > Attachments
⋙ Protect against attachments with scripts from untrusted senders
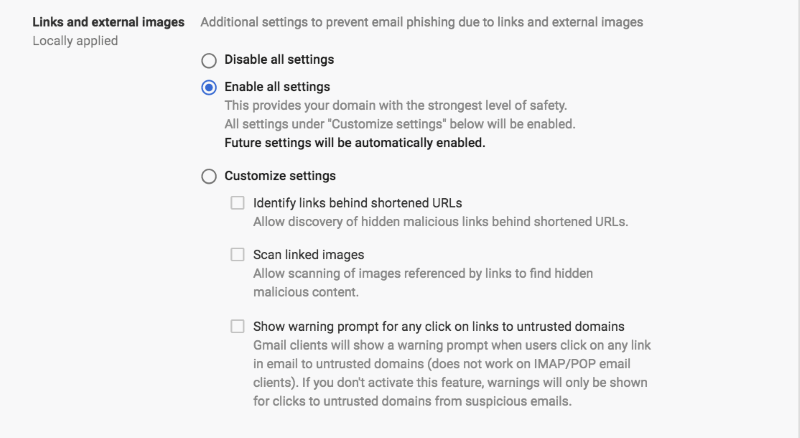
Apps > G Suite > Gmail > Safety > Links and external images
⋙ Scan linked images
⋙ Show warning prompt for any click on links to untrusted domains
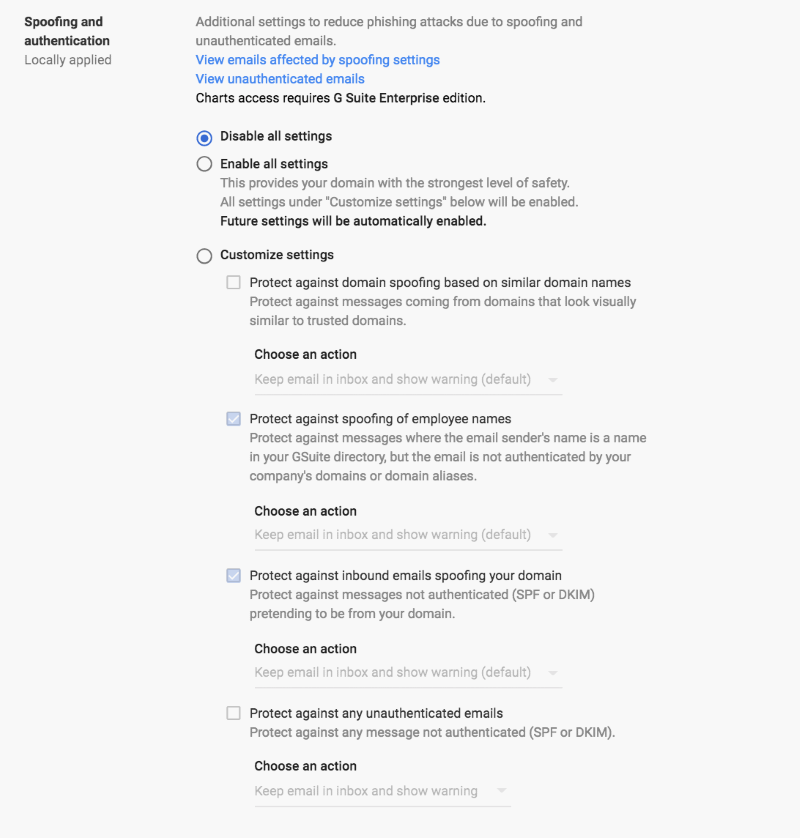
Apps > G Suite > Gmail > Safety > Spoofing and authentication
⋙ Protect against spoofing of employee names
⋙ Protect against inbound emails spoofing your domain
⋙ Protect against any unauthenticated emails
All these new features have been rolled out today. Google plans to enable two of these by default for all G Suite customers on April 4. these are:
⋙ Scan linked images
