Safari, Edge, and Firefox were the favorite targets that fell to white hat hackers at the world’s most well-known competitive hacking competition —Pwn2Own 2018— held over the past two days in Vancouver, Canada.
Hackers took home $267,000 of the total $2 million prize pool, which is way less than the usual sum hackers earned at such contests in the past years.
Contest marred by controversy
The competition was marred by controversy, as Chinese researchers pulled out after the Chinese government took steps to discourage security researchers from participating in Pwn2Own and other similar hacking contests.
Government officials argued they didn’t want Chinese researchers sharing vulnerability and exploit information with third-parties in foreign countries, encouraging researchers to report flaws to vendors directly.
No Chinese researcher entered the contest, even if Chinese research teams dominated and won almost all recent Pwn2Own competitions. Nonetheless, the contest went on as scheduled, albeit with fewer contestants than in previous years.
Richard Zhu wins Pwn2Own 2018
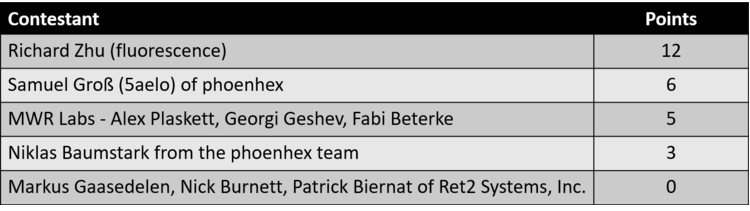
Richard Zhu (@fluorescence) won the contest by gaining 12 points for hacking Edge and Firefox. Zhu took home $120,000 of the $267,000 total prize money awarded at the event. Each researcher also got to keep the laptop they tried their exploits on.
Products like Oracle VirtualBox, VMware Workstation, Microsoft Hyper-V Client, Chrome, Safari, Edge, Firefox, Adobe Reader, Microsoft Office 365 ProPlus, Microsoft Outlook, NGINX, Apache Web Server, Microsoft Windows SMB, and OpenSSL were available for hacking, with the highest prize being $250,000 for a sandbox escape to hypervisor or kernel for Microsoft’s Hyper-V virtual machine client.
Each contestant had 30 minutes and three tries to run a successful exploit on a test computers. Contestants received points based on the type of exploits they used. The results of the two-day event are as follow.
| Contestant | Hack | Result |
|---|---|---|
| Richard Zhu | Targeted Apple Safari with a sandbox escape | Failed |
| Niklas Baumstark (Phoenhex team) | Achieved code execution on Oracle VirtualBox via OOB and TOCTOU exploits | Partial |
| Samuel Groß (Phoenhex team) | Used a combination of a JIT optimization bug in the browser, a macOS logic bug to escape the sandbox, and finally a kernel overwrite to execute code with a kernel extension to successfully exploit Apple Safari | Success |
| Richard Zhu | First try (failed): Targeted Microsoft Edge with a Windows kernel EoP Second try (failed): Same exploit, but computer entered a BSOD Third try: Used two use-after-free (UAF) bugs in the browser and an integer overflow in the kernel to pawn Edge with 00:01:37 on the clock left. |
Success |
| Richard Zhu | Used an out-of-bounds (OOB) write in Firefox followed by an integer overflow in the Windows kernel to take full control over Firefox | Success |
| Markus Gaasedelen, Nick Burnett, and Patrick Biernat of Ret2 Systems, Inc. | Targeted Apple Safari with a macOS kernel EoP | Failed |
| Alex Plaskett, Georgi Geshev, and Fabi Beterke of MWR Labs | Used a heap buffer underflow in the browser and an uninitialized stack variable in macOS to escape the sandbox and gain code execution on Safari | Success |
The contest was organized by Trend Micro’s Zero Day Initiative (ZDI), which rewarded contestants with monetary prizes for each exploit, even for those that failed to execute during the contest, albeit with a smaller reward.
ZDI experts than forwarded details on all vulnerabilities used during the contest to vendor representatives present at the event, who now have 90 days to issue patches.
To read the original article :
