In October last year, three Android apps on Play Store were found infected with Coinhive cryptocurrency miner to generate Monero digital coins. Now, an IT security researcher Elliot Alderson found fake Android apps that are infected with Coinhive cryptocurrency miner specially developed to use the CPU power of a targeted device.
Fake App Real Miner
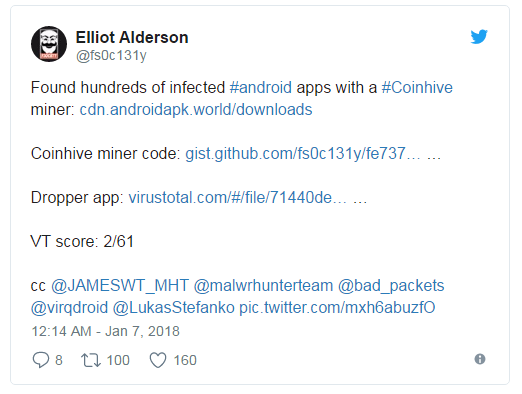
According to Elliot, whose real name is Robert Baptiste, these apps are available on a third-party website that claims to provide free APKs (Android application package) to users but in reality, these APKs are infected with Coinhive miner from the beginning.
“I don’t think these apps are the original apps. The “hacker” modified it and repacked it and after that, he uses multiple dropper apps to distribute these modified apps. Only the package name and the app name has been changed and I just dig up more and in fact, this is the same app 291 times which means there are 291 applications with different icons and names, Baptiste told HackRead.
Upon scanning, some of the APK files available on the site, VirusTotal showed that these files were infected with the Coinhive miner. Remember, secret use of any cryptocurrency miner is considered as using malware against users. To prove the point, last year, CloudFlare booted off one of their customers for secretly using Coinhive miner and not letting site visitors to opt-out or disable the code.

A look at the scam website (androidapk.world), that is hosting these malicious apps, shows it has been fully indexed in Google search engine without raising any suspicion. Also, the site claims to provide APKs for top apps including Super Mario Run, Netflix, Mobile Strike, Clash of Clans and others.

Moreover, the site was registered in March last year and since then the download counter shows some APK files have been downloaded millions of times. However, it is unclear if the download counter displays real-time figures or cybercriminals behind the scam are manually displaying the numbers to pose as an active and trustworthy APK download site.
Android Users Be Vigilant
Until now, the biggest victims of cryptocurrency miners were website owners and unsuspecting visitors. Now, Android users are also at risk. In the past, cybercriminals preferred malware attacks but since the price of Bitcoin has suddenly surged there has been an increase in attacks involving cryptocurrency miners.
To read the original article:
https://www.hackread.com/fake-android-app-coinhive-miner/
