Online scammers have made over $5,000 worth of Ethereum in one night alone, showing how gullible some cryptocurrency users can be. Miscreants achieved this by creating fake Twitter profiles for real-world celebrities and spamming the social network with messages tricking users to participate in « giveaways. » Crooks deceived users into sending […]
Non classé
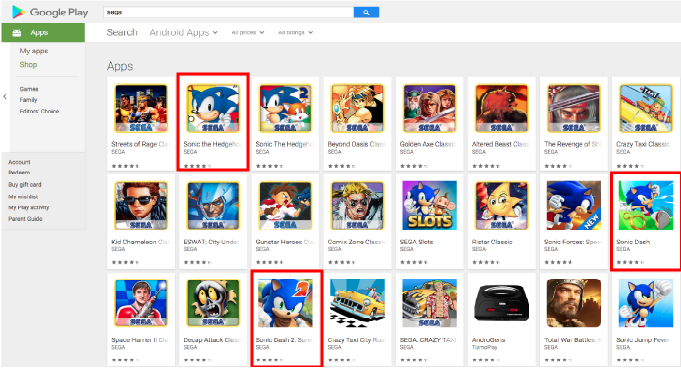
Three Sonic apps in the Google Play are leaking data to uncertified servers
Three Sonic apps in the Google Play are leaking data to uncertified servers According to a researcher from security firm Predeo, three Sonic apps in the Google Play published by SEGA leak users’ data to uncertified servers. According to a researcher from security firm Predeo, some game applications in the Google […]
Critical Intel AMT Flaw Lets Attackers Hack Laptops in Mere Seconds
It has been a matter of days when we found out about the flaws in AMD, ARM and Intel’s computer microchips that allowed attackers to carry out Spectre and Meltdown attacks. Since these microchips are widely used in almost all desktops/laptops, smartphones and tablets, therefore, the discovery sent out shockwaves […]
Two Romanians charged with infecting US Capital Police cameras with ransomware early this year
Two Romanian people have been arrested and charged with hacking into US Capital Police cameras ahead of the inauguration of President Trump. Two Romanian people have been arrested and charged with hacking into control systems of the surveillance cameras for the Metropolitan Police Department in the US. The two suspects, […]
Researchers discover a vulnerability in the DIRTY COW original patch
Researchers discovered that the original patch for the Dirty COW vulnerability (CVE-2016-5195) is affected by a security flaw. The original patch for the Dirty COW vulnerability (CVE-2016-5195) is affected by a security flaw that could be exploited by an attacker to run local code on affected systems and exploit a race condition […]
Assessing Weaknesses in Public Key Infrastructure
Assessing Weaknesses in Public Key Infrastructure Spreading malware with a legitimate digital certificate is an adversary’s dream come true, with plenty of successful examples tracing back to nation-state attacks such as Stuxnet and Flame, and other misuse that crops up on a regular basis. For a group of University of Maryland researchers, the nagging […]