Samba has just released new security patches for two critical vulnerabilities that could allow unprivileged remote attackers to launch DoS attacks against servers and change any other users’ passwords, including admin’s. Samba is open-source software (re-implementation of SMB networking protocol) that runs on the majority of operating systems available today, […]
Hacking
Researchers find critical flaws in SecurEnvoy SecurMail, patch now!
If you’re a user of SecurEnvoy SecurMail and you haven’t yet implemented the latest patch, do so now – or risk getting your encrypted emails read by attackers. The warning comes from SEC Consult researchers, who discovered a number of vulnerabilities in the product that break its core security […]
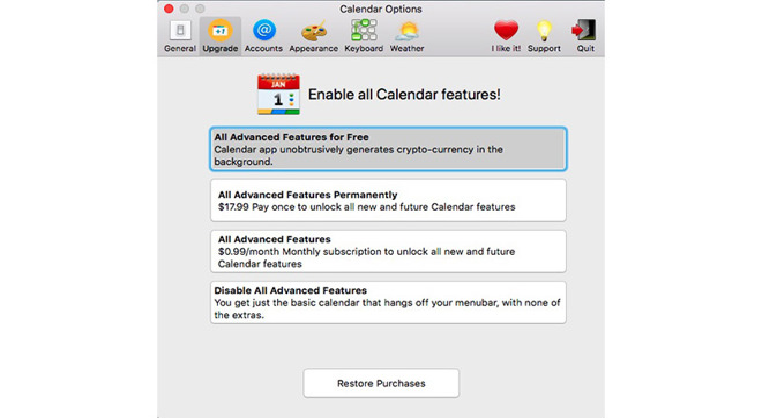
Mac Software Mines Cryptocurrency in Exchange for Free Access to Premium Account
Would you be okay with allowing a few paid services to mine cryptocurrencies using your system instead of paying the subscription fee? Most free websites and services often rely on advertising revenue to survive, but now there is a new way to make money—using customers’ computer to generate virtual […]
New Cyberespionage Attacks Linked to MuddyWater Campaign
Recent attacks targeting organizations in Turkey, Pakistan and Tajikistan appear to be linked to the previously detailed MuddyWater campaigns, according to Trend Micro. The MuddyWater campaigns were named so because of a high level of confusion they managed to create, thus making it difficult to attribute to a specific actor. […]
OceanLotus ships new backdoor using old tricks
ESET researchers have dissected some of the latest additions to the malicious toolkit of the Advanced Persistent Threat (APT) group known as OceanLotus, also dubbed APT32 and APT-C-00. A prolific purveyor of malware, OceanLotus has its sights set on high-profile corporate and government targets in Southeast Asia, particularly in Vietnam, […]
Report: Three of Top Four Malware Threats Are In-Browser Cryptocurrency Miners
Three in-browser cryptocurrency mining scripts ranked first, second, and fourth in Check Point’s most active malware top ten, outranking classic high-output malware distribution infrastructures such as spam botnets, malvertising, and exploit kit operations. The three are Coinhive (ranked #1), Crypto-Loot (ranked #2), and JSEcoin (ranked #4). These three are online services […]
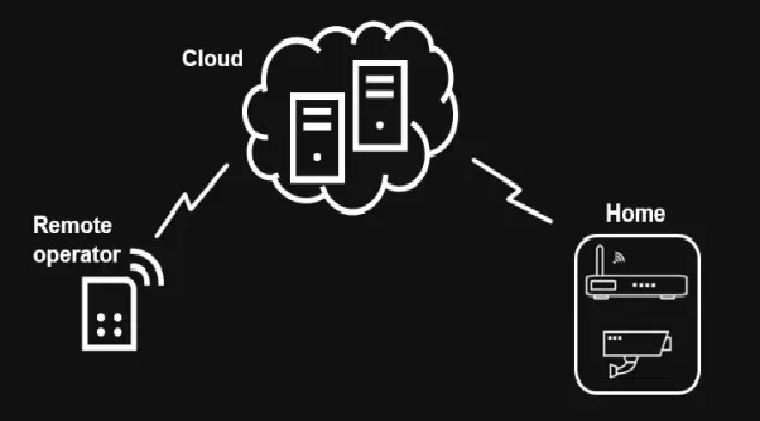
New security vulnerabilities found in smart devices
Kaspersky Lab security researchers have admitted to finding multiple security vulnerabilities across popular smart devices. According to research from the company the uncovered flaws could allow attackers to obtain remote access to video and audio feeds from the smart cameras, which are used frequently for baby monitors or internal home […]
13 Vulnerabilities in Hanwha SmartCams Demonstrate Risks of Feature Complexity
The researchers at Kaspersky Lab ICS CERT decided to check the popular Hanwha SmartCams and discovered 13 vulnerabilities. Wikipedia describes Attack Surface, as “[the] sum of the different points (the “attack vectors”) where an unauthorized user (the “attacker”) can try to enter data to or extract data from an environment.” Basically, the more […]
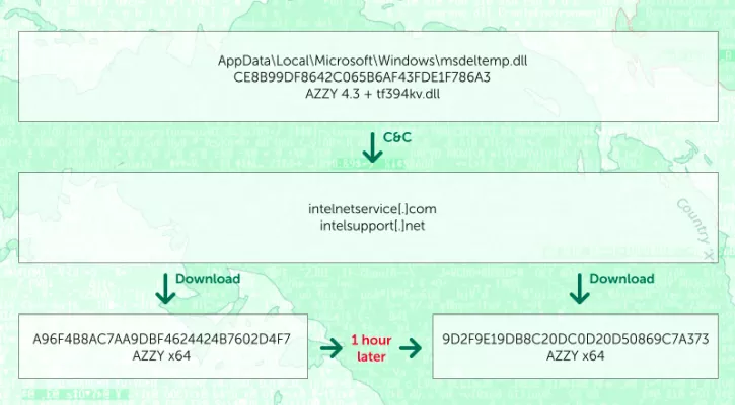
China-Linked APT15 used new backdoors in attack against UK Government’s service provider
China-Linked APT15 used new backdoors is an attack that is likely part of a wider operation aimed at contractors at various UK government departments and military organizations. Last week Ahmed Zaki, a senior malware researcher at NCC Group, presented at the Kaspersky’s Security Analyst Summit (SAS), details of a malware-based attack against […]
Kaspersky – Sofacy ‘s campaigns overlap with other APT groups’ operations
According to Kaspersky, the Sofacy APT is particularly interested in military, defense and diplomatic entities in the far east, but overlap with other APT’s operations makes hard the attribution. Last week, during the Kaspersky Security Analyst Summit (SAS) held in Cancun, researchers from Kaspersky illustrated the results of their investigation on the […]