Facebook has confirmed over the weekend reports that an app made by a team of academics had collected vasts amounts of user data, who then shared this information with Cambridge Analytica —a commercial data analytics firm that allegedly used this info to target US voters in the 2016 Presidential election. […]
Hacking
Firefox Master Password System Has Been Poorly Secured for the Past 9 Years
For at past nine years, Mozilla has been using an insufficiently strong encryption mechanism for the « master password » feature. Both Firefox and Thunderbird allow users to set up a « master password » through their settings panel. This master password plays the role of an encryption key that is used to encrypt […]
Cisco Meraki Offers Up to $10,000 in Bug Bounty Program
Cisco Meraki, a provider of cloud-managed IT solutions, announced last week the launch of a public bug bounty program with rewards of up to $10,000 per vulnerability. Cisco Meraki, which resulted from Cisco’s acquisition of Meraki in late 2012, started with a private bug bounty program on the Bugcrowd platform. […]
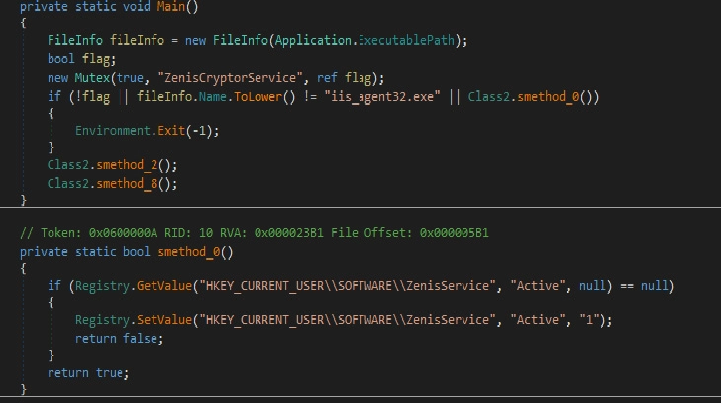
Zenis Ransomware Encrypts Your Data & Deletes Your Backups
A new ransomware was discovered this week by MalwareHunterTeam called Zenis Ransomware. While it is currently unknown how Zenis is being distributed, multiple victims have already become infected with this ransomware. What is most disturbing about Zenis is that it not encrypts your files, but also purposely deletes your backups. When MalwareHunterTeam found the first […]
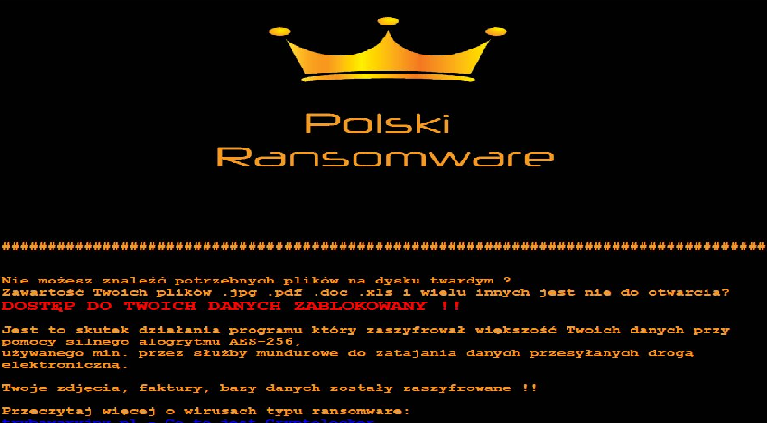
Author of Polski, Vortex, and Flotera Ransomware Families Arrested in Poland
Polish law enforcement announced on Friday the arrest of Tomasz T., a well-known cyber-criminal believed to be the author of the Polski, Vortex, and Flotera ransomware strains. The arrest took place on Wednesday, March 14, in the Polish town of Opole, while Tomasz —a Polish national living in Belgium— was […]
Vulnérabilité dans VMware Workstation et Fusion
VMware a publié des mises à jour de sécurité pour résoudre les vulnérabilités dans VMware Workstation et Fusion. Un attaquant distant pourrait exploiter ces vulnérabilités pour provoquer un déni de service. RISQUE(S) Déni de service SYSTÈMES AFFECTÉS Workstation versions 14.x antérieures à 14.1.1 Workstation versions 12.x Fusion versions 10.x sur OS […]
Suspected Chinese Cyber Espionage Group (TEMP.Periscope) Targeting U.S. Engineering and Maritime Industries
Intrusions Focus on the Engineering and Maritime Sector Since early 2018, FireEye (including our FireEye as a Service (FaaS), Mandiant Consulting, and iSIGHT Intelligence teams) has been tracking an ongoing wave of intrusions targeting engineering and maritime entities, especially those connected to South China Sea issues. The campaign is linked […]
Pre-installed malware on Android devices made $115k revenue in 10 days
Check Point Mobile Security Team discovered a massive, on-going malware campaign that so far has claimed 5 million victims. Reportedly, the malware dubbed as RottenSys has managed to create a massive army of botnets comprising of 5 million mobile devices from across the globe. The malware is hidden in a […]
Firefox, Edge, and Safari Browsers Fall at Famous Pwn2Own Hacking Contest
Safari, Edge, and Firefox were the favorite targets that fell to white hat hackers at the world’s most well-known competitive hacking competition —Pwn2Own 2018— held over the past two days in Vancouver, Canada. Hackers took home $267,000 of the total $2 million prize pool, which is way less than the […]
Mossack Fonseca law firm shuts down operations 2 years after Panama Papers
News of the day is that the Mossack Fonseca law firm would shut down operations due to the reputational damage caused by the Panama Papers security breach. The Panama Papers is a huge trove of strictly confidential documents from the Panamanian law firm Mossack Fonseca that was leaked online on April 3, 2016. […]