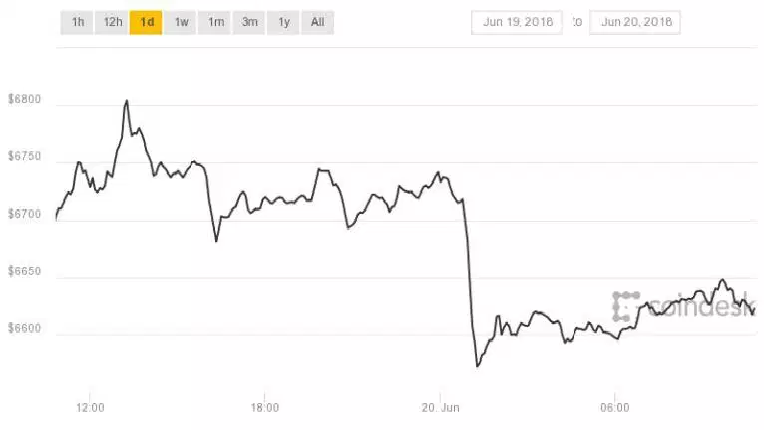
One of Asia’s largest crypto exchanges, Bithumb announced that they have fallen victim to a hack attack, with hackers reportedly stealing more than $30 million worth digital currencies. Wallet change backfires Last Tuesday, June 19, the cryptocurrency exchange made an announcement that they would be temporarily suspending deposits to give […]
Hacking
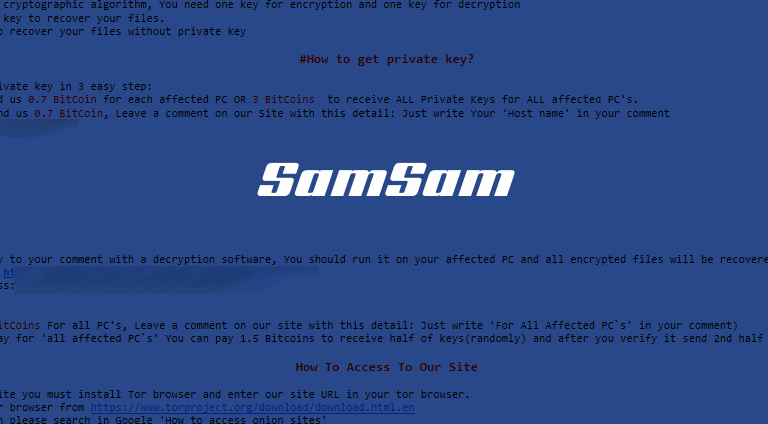
New SamSam Variant Requires Special Password Before Infection
New versions of the SamSam ransomware will not execute unless the person running the malware’s payload enters a special password via the command-line. This is a new protection mechanism added by the SamSam crew in a recent SamSam version discovered by Malwarebytes researchers. Previous versions did not feature this mechanism, […]
Google Developer Discovers a Critical Bug in Modern Web Browsers
Google researcher has discovered a severe vulnerability in modern web browsers that could have allowed websites you visit to steal the sensitive content of your online accounts from other websites that you have logged-in the same browser. Discovered by Jake Archibald, developer advocate for Google Chrome, the vulnerability resides in […]
Building a malware distribution network is too easy with Kardon Loader
Researchers at Netscout Arbor have discovered a malware downloader advertised on underground forums as a paid open beta product, its name is Kardon Loader. Researchers from Netscout Arbor have discovered a downloader advertised on underground forums dubbed Kardon Loader, it allows customers to build a malware distribution network or a botshop. Advs for Kardon Loader were first discovered […]
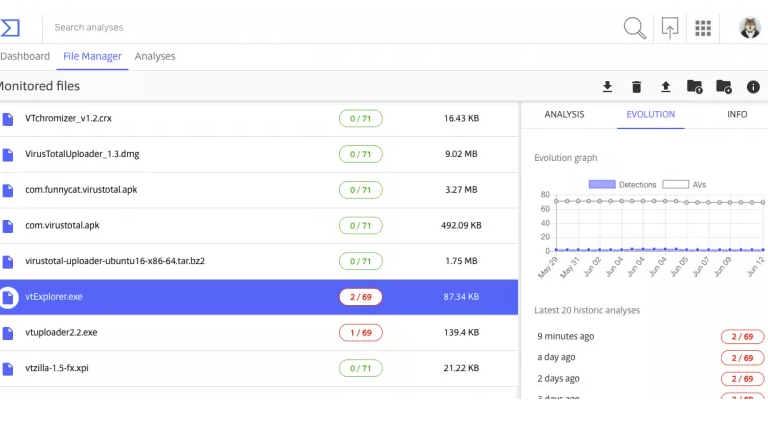
Chronicle launches VirusTotal Monitor to reduce false positives
Alphabet owned cybersecurity firm Chronicle announced the launch of a new VirusTotal service that promises to reduce false positives. VirusTotal Monitor service allows developers to upload their application files to a private cloud store where they are scanned every day using anti-malware solutions from antivirus vendors in VirusTotal. Every time the service […]
Flight tracking service Flightradar24 suffered a data breach
The popular flight tracking service Flightradar24 has discovered a data breach that affected one of its servers. The company notified the incident to its users via email and asked them to change their passwords, affected users’ passwords have been reset. FlightRadar24 promptly reported the incident to the Swedish Data Protection Authority in […]
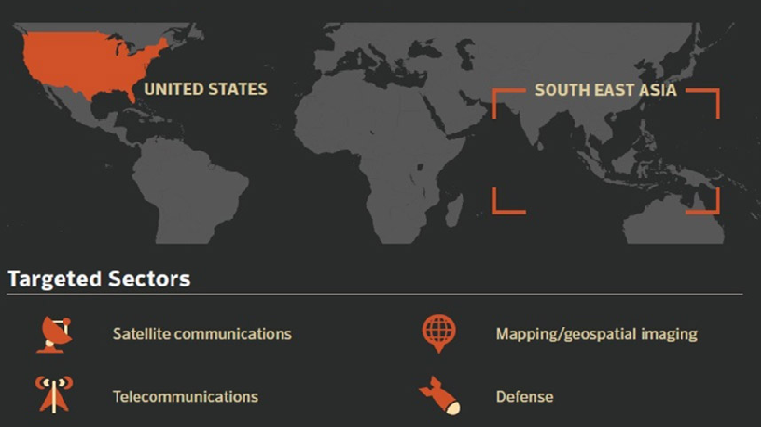
Espionage Group Hits Satellite, Telecoms, and Defense Companies
Symantec’s artificial intelligence-based Targeted Attack Analytics uncovers new wide-ranging espionage operation. One of the most significant developments in cyber espionage in recent years has been the number of groups adopting “living off the land” tactics. That’s our shorthand for the use of operating system features or legitimate network administration tools […]
ZeroFont phishing attack can bypass Office 365 protections
ZeroFont phishing attack – Crooks are using a new technique that involves manipulating font sizes to bypass Office 365 protections. According to cloud security firm Avanan, one of the detection mechanisms in Office 365 involves natural language processing to identify the content of the messages typically used in malicious emails. […]
Olympic Destroyer was involved in a new wave of cyber attacks
Olympic Destroyer, the malicious code that was used in attacks against Winter Games in Pyeongchang, was involved in a new wave of cyber attacks. The same malware used in recent Olympic Winter Games in Pyeongchang, tracked as Olympic Destroyer, has been used in a new wave of attacks against organizations in Germany, […]
Hackers Steal $31 Million from South Korean cryptocurrency exchange Bithumb
Just weeks after Korean exchange Coinrail was hacked, the Bithumb crypto exchange was hacked, crooks stole over $30 million in cryptocurrency. It has happened again, for the second time in a year, the cryptocurrency exchange Bithumb has been hacked. The South Korean cryptocurrency exchange confirmed that hackers stole 35 billion won […]