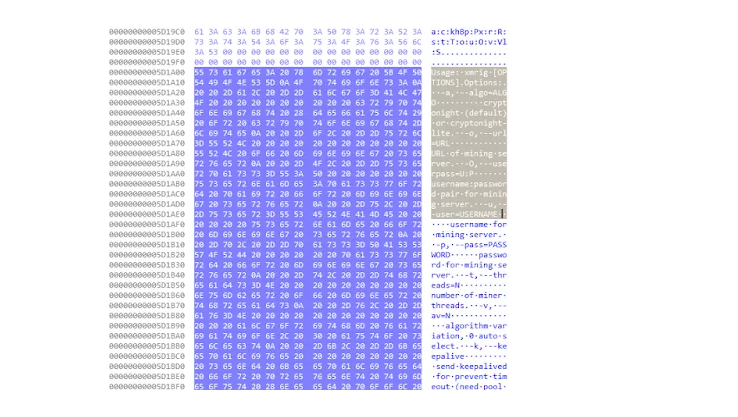
Sustes Malware doesn’t infect victims by itself, but it is spread via brute-force activities with special focus on IoT and Linux servers. Today I’d like to share a simple analysis based on a fascinating threat that I like to call Sustes (you will see name genesis in a bit). Everybody knows Monero […]
Hacking
Adobe issued a critical out-of-band patch to address CVE-2018-12848 Acrobat flaw
Adobe releases a critical out-of-band patch for CVE-2018-12848 Acrobat flaw, the security updates address a total of 7 vulnerabilities. Adobe address seven vulnerability in Acrobat DC and Acrobat Reader DC, including one critical vulnerability that could be exploited by attackers to execute arbitrary code. “Adobe has released security updates for Adobe […]
Selon le rapport, la violation des données Newegg expose les informations de carte de crédit client
Certains clients de Newegg auraient eu leur numéro de carte de crédit, alors que le groupe de piratage Magecart frappe à nouveau. Les chercheurs en sécurité RiskIQ ont déclaré mercredi que Magecart avait inséré un code malveillant dans le système de paiement du détaillant de matériel et d’électronique et qu’il […]
Focus on HMRC as Many Targeted Through an Email Phishing Campaign
A new phishing attack discovered by Malwarebytes is said to be from under a new campaign, utilizing an old trick with an end goal to steal login credentials, payment details and other sensitive data from victims by claiming to offer them a tax refund which must be asserted online. The […]
The makers of the Mirai IoT-hijacking botnet are sentenced
Three men who operated and controlled the notorious Mirai botnet have been sentenced to five years of probation. The Mirai botnet notoriously launched a massive distributed denial-of-service (DDoS) attack on DNS service company Dyn in October 2016 and made it impossible for many users to reach popular sites such as Amazon, Reddit, […]
MongoDB server leaks 11 million user records from e-marketing service
Database has now been secured. Server was also ransomed by a criminal group back in June. On Monday, a security researcher specialized in finding exposed databases has identified an unsecured MongoDB server that was leaking the personal details of nearly 11 million users. The server appears to belong to an […]
A flaw in Alpine Linux could allow executing arbitrary code
Security researcher Max Justicz has discovered several flaws in the distribution Alpine Linux, including an arbitrary code execution. Alpine Linux is an independent, non-commercial, general purpose Linux distribution that is heavily used in containers, including Docker. Alpine Linux is based on musl libc and busybox, it is a tiny distro and is […]
Cracked Windows installations are serially infected with EternalBlue exploit code
According to Avira, hundreds of thousands of unpatched Windows systems are serially infected with EternalBlue exploit code. The EternalBlue, is the alleged NSA exploit that made the headlines with DOUBLEPULSAR in the WannaCry attack. The malicious code was leaked online by the Shadow Brokers hacking group that stole it from the arsenal of the NSA-linked Equation Group. ETERNALBLUE targets the Server […]
HIDE AND SEEK Tracking NSO Group’s Pegasus Spyware to Operations in 45 Countries
In this post, we develop new Internet scanning techniques to identify 45 countries in which operators of NSO Group’s Pegasus spyware may be conducting operations. Key Findings Between August 2016 and August 2018, we scanned the Internet for servers associated with NSO Group’s Pegasus spyware. We found 1,091 IP addresses […]
Old WordPress Plugin Being Exploited in RCE Attacks
Old instances of the popular WordPress Duplicator Plugin are leaving sites open to remote code execution attacks. Researchers are warning that attackers are abusing a vulnerability in WordPress site admins’ outdated versions of a migration plugin called Duplicator – allowing them to execute remote code. Made by Snap Creek Software, all Duplicator plugins […]