Poor DNS housekeeping opens the door to account takeover. A proof-of-concept (PoC) attack details how an attacker can gain access a victim’s Microsoft Live webmail session, without having the person’s credentials. It relies upon the hijack of a Microsoft-owned Live.com website subdomain. The PoC, developed by CyberInt, demonstrates what it […]
Hacking
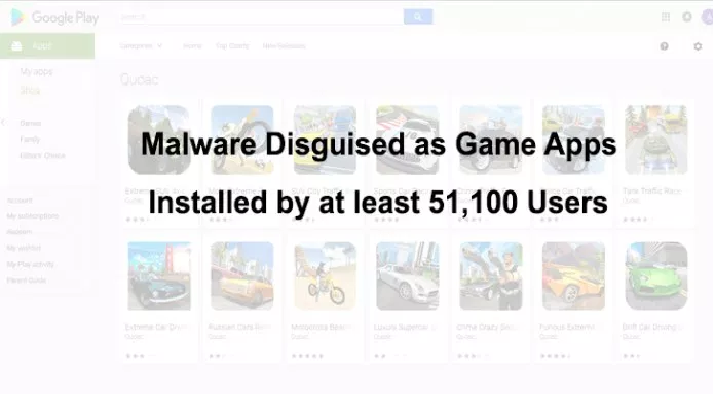
Beware! Downloader Malware Disguised as Game Apps Found On Google Play with More Than 51,100 Installations
The downloader malware dubbed Android.DownLoader.819.origin malware found on Google play downloaded by more than 51,100 Android users. The downloader malware is capable of installing other malicious applications on the affected devices and launches them. Doctor Web security researchers found 14 copies of the malicious application distributed by Quoac developer disguised as […]
BLEEDINGBIT Bluetooth flaws in TI chips expose enterprises to remote attacks
Two vulnerabilities in new Bluetooth chip, dubbed BLEEDINGBIT expose millions of access points and other networking devices to remote attacks. Security experts from the IoT security firm Armis, the same that found the BlueBorne Bluetooth flaws, have discovered two serious vulnerabilities in BLE chips designed by Texas Instruments. The flaws, dubbed BLEEDINGBIT by Armis, could be exploited by a […]
Now use Internet anonymously through Tor-enabled SIM card Onion3G
Now use Internet anonymously through Tor-enabled SIM card Onion3G Privacy concerns are rising with the advancement of technology. Today, we need to be a lot more careful about online browsing than we needed to a few years back despite that we have come far ahead with technology. Tor browser and VPNs are generally […]
Cisco Warns of Zero-Day Vulnerability in Security Appliances
Cisco informed customers on Wednesday that some of its security appliances are affected by a serious vulnerability that has been actively exploited. The zero-day flaw, tracked as CVE-2018-15454, is related to the Session Initiation Protocol (SIP) inspection engine used in the company’s Adaptive Security Appliance (ASA) and Firepower Threat Defense […]
Cyber Criminals attacked the system of Russian Railways and S7 airlines and killed the investigator
The court of Moscow began consideration of the case of fraud in the purchase of tickets. A group of hackers, consisting of 29 people, earned $ 258,000 on fictitious refunds of tickets of Russian Railways and S7 airlines in 2013-2014. This case was conducted by Evgenija Shishkina, the senior investigator […]
Kraken Ransomware Upgrades Distribution with RaaS Model
Affiliates pocket 80 percent of every ransom payment. The Kraken ransomware author has released a second version of the malicious code, along with a unique affiliate program on the Dark Web. According to research into Kraken v.2 the new version is being promoted in a ransomware-as-a-service (RaaS) model to underground […]
Many CMS plugins are disabling TLS certificate validation… and that’s very bad
An absurd number of CMS plugins and PHP libraries are disabling SSL/TLS certificate validation on purpose, and by doing so, they’re putting millions of internet users at great risk. To make matters worse, many of these plugins and libraries are used to establish connections to payment provider servers, connections through […]
IBM CORRIGE PLUSIEURS VULNÉRABILITÉS CRITIQUES DANS DIVERS PRODUITS
IBM a publié 35 bulletins de sécurité sur ses produits, entre le 19 et le 26 octobre. Parmi ceux-ci, 18 sont jugées élevées, 16 modérées et 1 faible. Parmi les vulnérabilités corrigées les plus critiques, aucune n’est spécifique aux produits IBM. Celles-ci sont référencées de la manière suivante : CVE-2018-16741 [CVSS 9.8] : Une vulnérabilité dans […]
UNE VULNÉRABILITÉ CRITIQUE CORRIGÉE SUR SOPHOS HITMANPRO
Des chercheurs de Talos ont découvert deux vulnérabilités, dont une critique dans Sophos HitmanPro, un outil de détection et de suppression des malwares. Un attaquant pourrait l’exploiter pour exécuter du code à distance ou élever ses privilèges. L’attaque est peu complexe à réaliser, ne peut être effectuée qu’en local, ne nécessite ni privilèges ni […]