Endpoint security solutions are failing to provide adequate protections to address today’s security threats, specifically malware, according to Minerva Labs. A majority of the respondents surveyed indicated a heightened concern of a major malware breach in the coming year and acknowledged that they require more than an AV solution on the […]
Cybersecurity
Carthage Cyber Arena CCA Edition 2018
CCA regroupe l’élite du monde de la cybersécurité et du Hacking, les responsables de sécurité, les chefs d’entreprises, les représentants de la communauté Internet et les étudiants pour coopérer et résoudre les problèmes de sécurité. CCA couvre les problèmes les plus actuels liés à la sécurité de l’information. L’édition CCA […]
Les meilleures pratiques de sécurité à adopter pour protéger son entreprise
En faisant les gros titres en 2017, les cyberattaques ont fait réaliser aux entreprises l’importance de s’en prémunir. Dans le même temps, elles ont démontré que la simple installation d’un antivirus ne suffit plus face aux menaces les plus récentes. Tribune par José Fernandes, directeur France de Malwarebytes – L’heure est désormais aux […]
Probably you ignore that Facebook also tracks non-users across the web
Facebook explained how it is tracking Non-Users across the Internet and for which purposes it is using their metadata. Facebook is still in the middle of a storm for its conduct and the way it approached the privacy of its users after the Cambridge Analytica case. Now Facebook is under scrutiny after Zuckerberg […]
Cisco Smart Install Protocol Misuse
Cisco is aware of a significant increase in Internet scans attempting to detect devices where, after completing setup, the Smart Install feature remains enabled and without proper security controls. This could leave the involved devices susceptible to misuse of the feature. Customers who have not done so are encouraged to […]
Financial Services DDoS Attacks Tied to Reaper Botnet
Recorded Future’s « Insikt » threat intelligence research group has linked the Mirai variant IoTroop (aka Reaper) botnet with attacks on the Netherlands financial sector in January 2018. The existence of IoTroop was first noted by Check Point in October 2017. At that point the botnet had not been used to deliver any known DDoS […]
Project Kalamata – Apple will replace Intel processors in Macs with its custom designed chips
In the wake of the discovery of severe flaws in Intel chips, so-called Meltdown and Spectre vulnerabilities, Apple announced it plans to use custom-designed ARM chips in Mac computers starting as early as 2020. The move aims to replace the Intel processors running on its desktop and laptop systems like done for its own […]
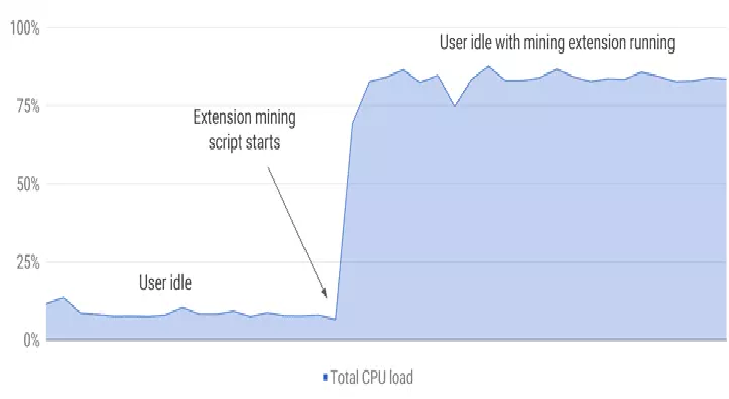
Google to banish cryptocurrency mining extensions from official Chrome Web Store
Google will ban cryptocurrency mining extensions from the official Chrome Web Store after finding many of them abusing users’ resources without consent. The number of malicious extensions is rapidly increased over the past few months, especially those related to mining activities. The company has introduced a new Web Store policy that bans […]
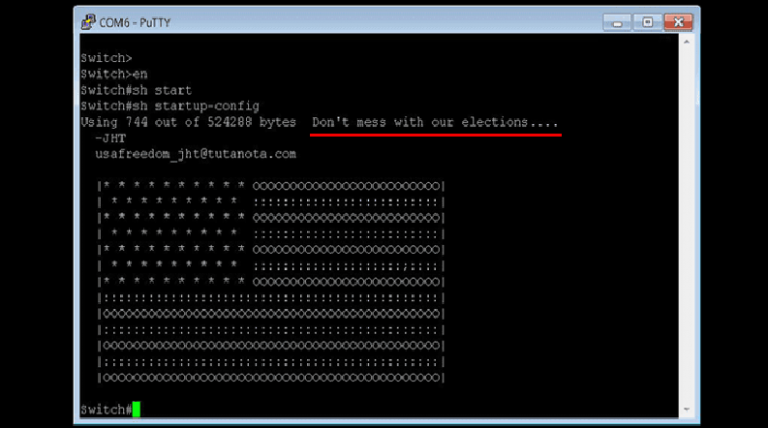
Cisco Removes Backdoor Account from IOS XE Software
isco removed today a backdoor account from its IOS XE operating system that would have allowed a remote attacker to log into Cisco routers and switches with a high-privileged account. The company says the « undocumented user account » only impacts devices running Cisco XE Software 16.x —an operating system deployed mostly […]
Preventing the Next Ransomware Attack
2018 is quickly moving by us, and while we have yet to see an attack on the scale of 2017’s WannaCry or NotPetya, it’s clear that the adversaries are not letting up on their mission to line their pockets at our expense. Ransomware has dominated the headlines for the last two years, while […]