Security researchers have discovered a new, sophisticated form of malware based on the notorious Zeus banking Trojan that steals more than just bank account details.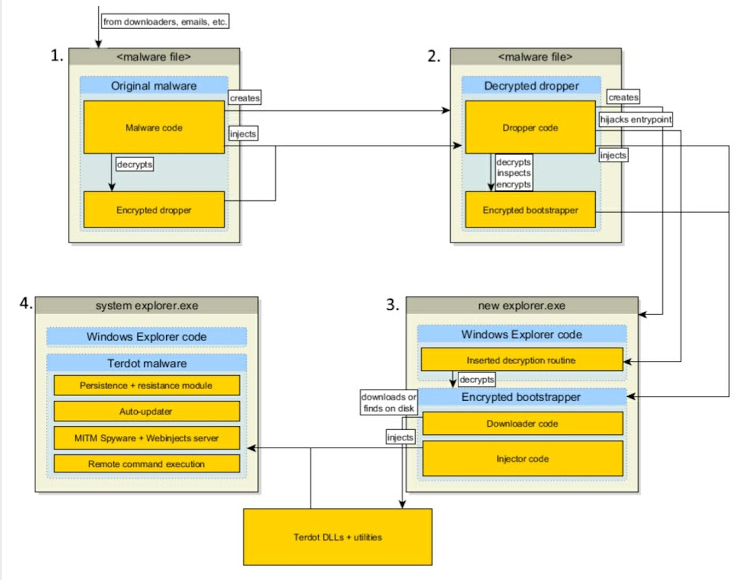
Dubbed Terdot, the banking Trojan has been around since mid-2016 and was initially designed to operate as a proxy to conduct man-in-the-middle (MitM) attacks, steal browsing information such as stored credit card information and login credentials and injecting HTML code into visited web pages.
However, researchers at security firm Bitdefender have discovered that the banking Trojan has now been revamped with new espionage capabilities such as leveraging open-source tools for spoofing SSL certificates in order to gain access to social media and email accounts and even post on behalf of the infected user.
Terdot banking trojan does this by using a highly customized man-in-the-middle (MITM) proxy that allows the malware to intercept any traffic on an infected computer.
Besides this, the new variant of Terdot has even added automatic update capabilities that allow the malware to download and execute files as requested by its operator.
Usually, Terdot targeted banking websites of numerous Canadian institutions such as Royal Bank, Banque Nationale, PCFinancial, Desjardins, BMO (Bank of Montreal) and Scotiabank among others.
This Trojan Can Steal Your Facebook, Twitter and Gmail accounts
However, according to the latest analysis, Terdot can target social media networks including Facebook, Twitter, Google Plus, and YouTube, and email service providers including Google’s Gmail, Microsoft’s live.com, and Yahoo Mail.
Interestingly, the malware avoids gathering data related to Russian largest social media platform VKontakte (vk.com), Bitdefender noted. This suggests Eastern European actors may be behind the new variant.
The banking Trojan is mostly being distributed through websites compromised with the SunDown Exploit Kit, but researchers also observed it arriving in a malicious email with a fake PDF icon button.
If clicked, it executes obfuscated JavaScript code that downloads and runs the malware file. In order to evade detection, the Trojan uses a complex chain of droppers, injections, and downloaders that allow the download of Terdot in pieces.
Once infected, the Trojan injects itself into the browser process to direct connections to its own Web proxy, read traffic and inject spyware. It can also steal authentication info by inspecting the victim’s requests or injecting spyware Javascript code in the responses.
To read the original article :
https://thehackernews.com/2017/11/facebook-twitter-hack.html
