At our recent Pwn2Own 2018 competition, Richard Zhu (fluorescence) targeted and successfully exploited Mozilla Firefox with only one bug. After handing over the bug to Mozilla at the contest, they have promptly coordinated an update in less than 24 hours. The response was certainly impressive, but I wanted to take a closer […]
Haythem Elmir
Five year old vulnerability used for Monero mining on Linux servers
A security vulnerability that is nearly 5 years old has now become the favorite tool of hackers as they are using it to infect Linux servers with crypto mining malware. The vulnerability that is being exploited in this cryptojacking campaign is classified as CVE-2013-2618. The miner is an altered XMRig tool, which is […]
Best Buy Hit by [24]7.ai Payment Card Breach
After Delta Air Lines and Sears Holdings, Best Buy has also come forward to warn customers that their payment card information may have been compromised as a result of a breach suffered by online services provider [24]7.ai. Similar to Delta and Sears, Best Buy contracted [24]7.ai for online chat/support services. The retailer […]
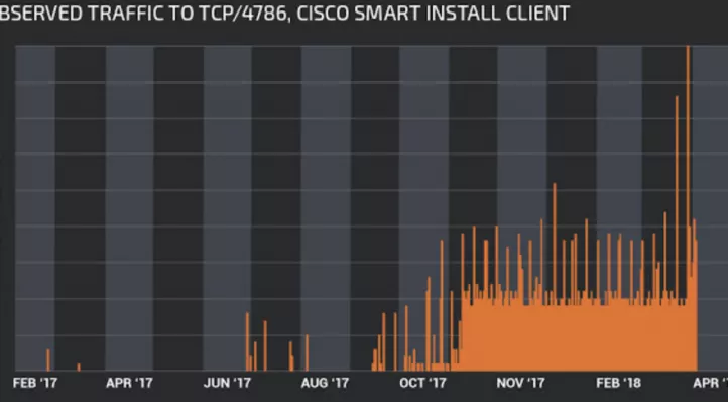
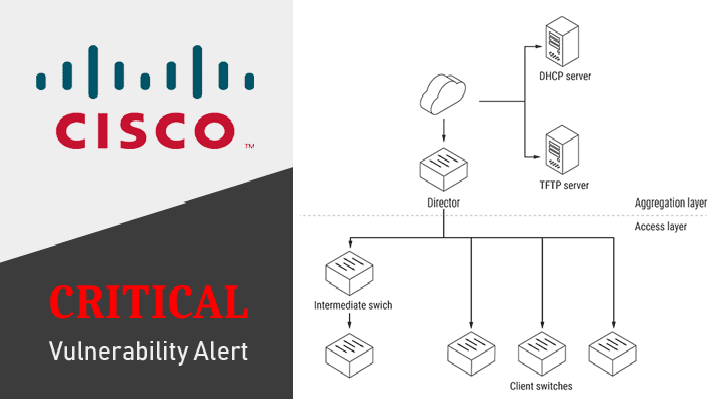
Cisco Smart Install Protocol misuse could expose critical infrastructure to attacks
Cisco PSIRT has published a new security advisory for abuse of the Smart Install protocol, the IT giant has identified hundreds of thousands of exposed devices online. Cisco is advising organizations that hackers could target its switches via the Smart Install protocol. The IT giant has identified hundreds of thousands of exposed […]
Critical flaw leaves thousands of Cisco Switches vulnerable to remote hacking
Security researchers at Embedi have disclosed a critical vulnerability in Cisco IOS Software and Cisco IOS XE Software that could allow an unauthenticated, remote attacker to execute arbitrary code, take full control over the vulnerable network equipment and intercept traffic. The stack-based buffer overflow vulnerability (CVE-2018-0171) resides due to improper […]
INTEL TELLS REMOTE KEYBOARD USERS TO DELETE APP AFTER CRITICAL BUG FOUND
Intel said Tuesday it was putting the kibosh on a popular Android and iOS app called Intel Remote Keyboard after researchers discovered that local attackers can inject keystrokes into a remote keyboard session when in use. The Intel Remote Keyboard product is an Android and iOS app that works in […]
New macOS Backdoor Linked to Cyber-espionage Group
A recently discovered macOS backdoor is believed to be a new version of malware previously associated with the OceanLotus cyber-espionage group, Trend Micro says. Also known as APT 32, APT-C-00, SeaLotus, and Cobalt Kitty, OceanLotus is believed to be operating out of Vietnam and has been targeting high-profile corporate and government […]
RAROG TROJAN ‘EASY ENTRY’ FOR NEW CRYPTOMINING CROOKS, REPORT WARNS
A malware family called Rarog is becoming an appealing and affordable tool for hackers to launch cryptocurrency mining attacks, researchers say. They say the Trojan is low priced, easily configurable and supports multiple cyrptocurrencies, making it an appealing option for hackers. Palo Alto Networks’ Unit 42 research team, which posted a blog on […]
Un satellite et un système de GPS 100% tunisiens
Dans le cadre de sa lutte contre le terrorisme, l’Armée Nationale compte miser sur les nouvelles technologies, selon le militaire Nizar Tabia, qui a affirmé, ce mercredi 4 avril 2018 sur Mosaïque FM, que l’Armée est en train de travailler sur un projet de géolocalisation basé sur la technologie GPS. […]
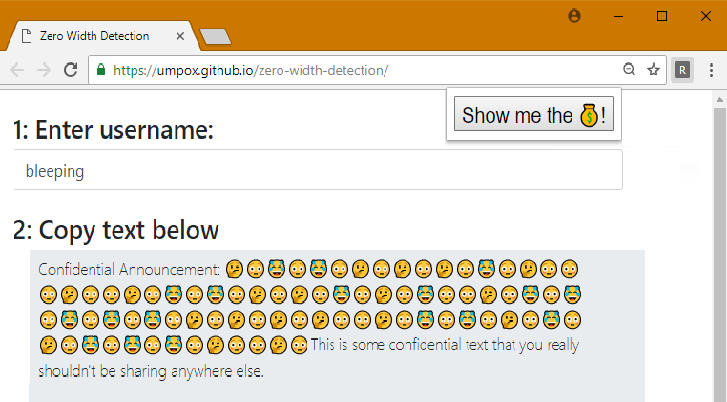
Google Chrome Extension Detects « Zero-Width Character » Fingerprinting Attacks
Google Chrome Extension Detects « Zero-Width Character » Fingerprinting Attacks Software developer Marco Chiappetta has built a Google Chrome extension that can detect attempts to fingerprint text using the « zero-width character » technique. The extension, named « Replace zero-width characters with emojis » is available on the official Google Chrome Web Store and on GitHub. Zero-width characters can […]

![Best Buy Hit by [24]7.ai Payment Card Breach](https://cyber.tn/wp-content/uploads/2018/04/best-buy.png)