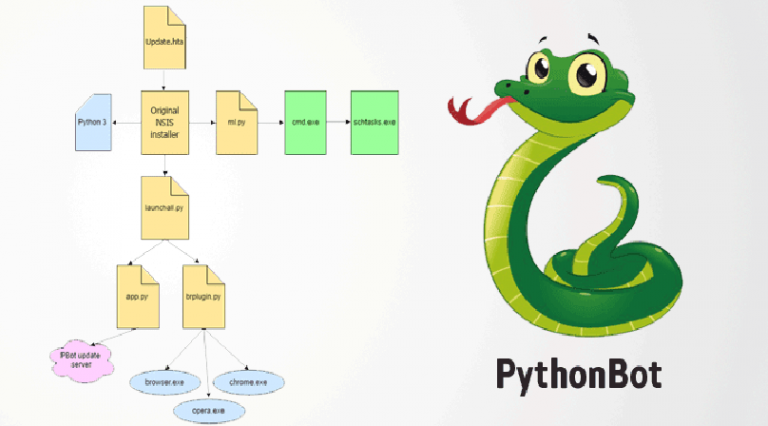
De nouvelles variantes d’un logiciel publicitaire (adware) basé sur Python sont distribuées sur Internet. Ces variantes infectent les machines et affichent des publicités sur les postes. De la même manière, elles installent des extensions malicieuses et des mineurs de cryptomonnaie sur les machines. Baptisé PBot ou PythonBot, ce publiciel a […]
Haythem Elmir
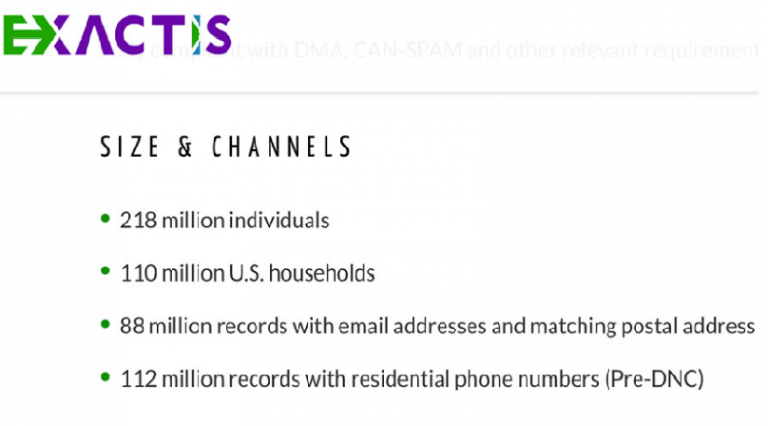
Data Broker Exactis data breach, one of the biggest ever, exposes millions of Americans
Security expert Vinny Troia has found a huge trove of data belonging to millions of Americans that were left unsecured online. The security researcher Vinny Troia was analyzing the level of security for Elasticsearch installs exposed online when discovered millions of records belonging to Americans that were left unsecured online. The expert […]
Zerodium offers up to $500,000 for Linux Zero-Day exploits
The sale of Zero-day exploits is a prolific business, zero-day broker Zerodium offers rewards of up to $500,000 FreeBSD, OpenBSD, NetBSD, Linux Zero-Days. The sale of Zero-day exploits is a prolific business that most people totally ignore, to better understand its evolution let’s analyze together the offer of the popular […]
RIG Exploit Kit operators leverage PROPagate Injection Technique to deliver Miner
FireEye reported the PROPagate code injection technique that was observed for the first time in a malware distribution campaign in the wild. Security experts from FireEye have documented the PROPagate code injection technique that was observed for the first time in a malware distribution campaign in the wild. The PROPagate code […]
ProtonMail DDoS Attacks Are a Case Study of What Happens When You Mock Attackers
For the past two days, secure email provider ProtonMail has been fighting off DDoS attacks that have visibly affected the company’s services, causing short but frequent outages at regular intervals. « The attacks went on for several hours, although the outages were far more brief, usually several minutes at a time […]
Researchers Uncover New Attacks Against LTE Network Protocol
If your mobile carrier offers LTE, also known as the 4G network, you need to beware as your network communication can be hijacked remotely. A team of researchers has discovered some critical weaknesses in the ubiquitous LTE mobile device standard that could allow sophisticated hackers to spy on users’ cellular […]
RAMpage Attack Explained—Exploiting RowHammer On Android Again!
A team of security researchers has discovered a new set of techniques that could allow hackers to bypass all kind of present mitigations put in place to prevent DMA-based Rowhammer attacks against Android devices. Dubbed RAMpage, the new technique (CVE-2018-9442) could re-enable an unprivileged Android app running on the victim’s device […]
Rewards of Up to $500,000 Offered for FreeBSD, OpenBSD, NetBSD, Linux Zero-Days
Exploit broker Zerodium is offering rewards of up to $500,000 for zero-days in UNIX-based operating systems like OpenBSD, FreeBSD, NetBSD, but also for Linux distros such as Ubuntu, CentOS, Debian, and Tails. The offer, first advertised via Twitter earlier this week, is available as part of the company’s latest zero-day […]
Hackers compromised Gentoo Linux GitHub Page and planted a malicious code
The development team of the Gentoo Linux distribution notifies users that hackers compromised one of the GitHub accounts and planted a malicious code. Developers of the Gentoo Linux distribution announced that hackers compromised one of the GitHub accounts used by the organization and planted a malicious code. “Today 28 June […]
Apophis Squad hacker group is the alleged responsible for the DDoS attack against ProtonMail
A massive DDoS attack hit encrypted email provider ProtonMail, experts believe it was powered by Russian hackers. On Wednesday morning, ProtonMail informed customers that its systems were under attack that was causing a delay in the delivery of the messages. Anyway, the company highlighted that the emails systems did not suffer […]