Des chercheurs d’ESET et Microsoft ont publié les détails techniques de deux vulnérabilités de type «zero-day» découvertes en mars 2018. Les deux failles ont été corrigées par Microsoft lors du Patch Tuesday de mai 2018. L’exploitation de la première vulnérabilité permettrait l’exécution de code arbitraire à distance dans Adobe Acrobat et […]
Haythem Elmir
Malware “WellMess” Targeting Linux and Windows
Some malware is designed to run on multiple platforms, and most commonly they are written in Java. For example, Adwind malware (introduced in a past article) is written in Java, and it runs on Windows and other OS. Golang is another programming language, and it is used for Mirai controller, which […]
Hamas cyber-operatives lure Israeli soldiers to spyware hidden in tainted apps
Israeli military intelligence accused Hamas operatives of creating tainted apps to lure soldiers into downloading spyware onto their phones. According to a report published by the Israeli military, Hamas hackers are attempting to lure Israel Defence Forces (IDF) soldiers into installing tainted apps on their devices. Israeli military already blamed Hamas […]
Gentoo Publishes Incident Report After GitHub Hack
Maintainers of the Gentoo Linux distribution published an incident report on Wednesday after someone hijacked one of the organization’s GitHub accounts and planted malicious code. The attack started on June 28 and the hacker (or hackers) not only changed content in compromised repositories, but also locked out Gentoo developers from the targeted […]
HPE CORRIGE UNE VULNÉRABILITÉ IMPORTANTE DANS INTEGRATED LIGHTS-OUT
HPE Integrated Lights-Out (iLO) est une technologie de gestion de serveurs à distance de Hewlett-Packard. Elle offre des fonctionnalités de gestion hors-bande (démarrage d’une machine éteinte à distance, accès à la console système à distance…). Une vulnérabilité importante a été identifiée dans iLO 4 et 5. Son exploitation permettrait la […]
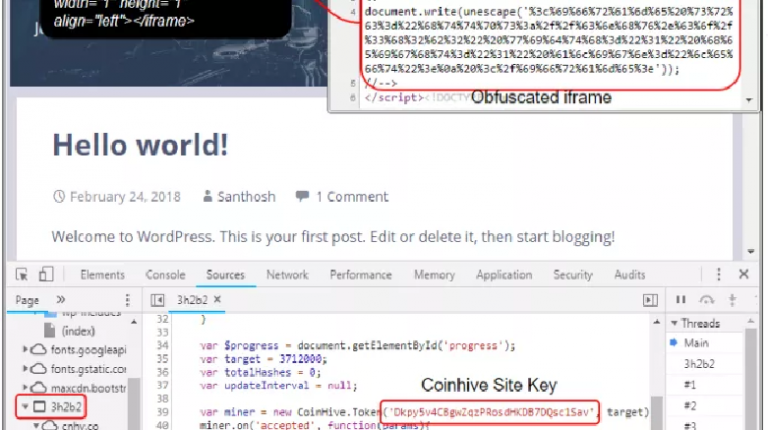
Crooks leverage obfuscated Coinhive shortlink in a large crypto-mining operation
Crooks leverage an alternative scheme to mine cryptocurrencies, they don’t inject the CoinHive JavaScript miner directly into compromised websites. Security researchers at MalwareLabs have uncovered a new crypto mining campaign that leverages an alternative scheme to mine cryptocurrencies, differently from other campaigns, crooks don’t inject the CoinHive JavaScript miner directly in compromised […]
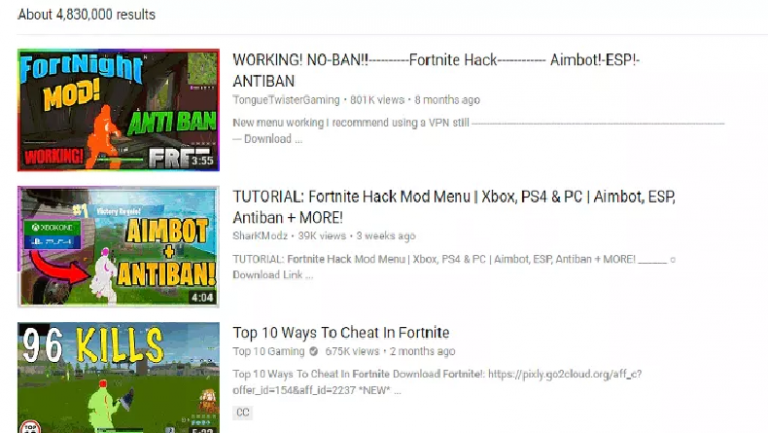
Adware already infected at least 78000 Fortnite Players
Rainway reported that tens of thousands of Fortnite players have been infected with an adware while downloading fake v-buck generators Fortnite continues to be one of the most popular game and crooks are attempting to target millions of fans in different ways. In June, experts observed cyber criminals attempting to exploit […]
The New Face of Necurs: Noteworthy Changes to Necurs’ Behaviors
Six years after it was first spotted in the wild, the Necurs malware botnet is still out to prove that it’s a malware chameleon. We recently discovered noteworthy changes to the way Necurs makes use of its bots, such as pushing infostealers on them and showing a special interest in […]
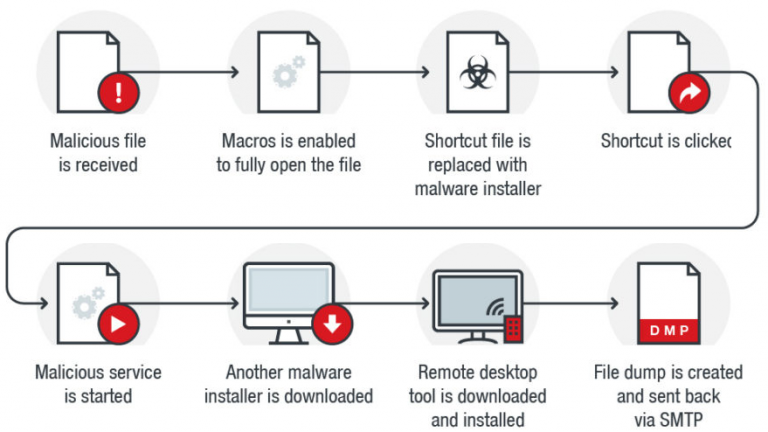
Malicious Macro Hijacks Desktop Shortcuts to Deliver Backdoor
Despite being around for decades, cybercriminals are still using malicious macro to deliver malware, albeit in more creative ways to make them more effective. The threat actors behind a recent case used macro in a more roundabout way, with a macro that searches for specific shortcut files in the user’s […]
Huawei enterprise and broadcast products have a crypto bug. Fix it now!
Huawei has rolled out security fixes for some enterprise and broadcast products to address a cryptography issue tracked as CVE-2017-17174. Huawei has released security updates for some enterprise and broadcast products to address a cryptography issue that was discovered in late 2017. The vulnerability, tracked as CVE-2017-17174, is related to the […]