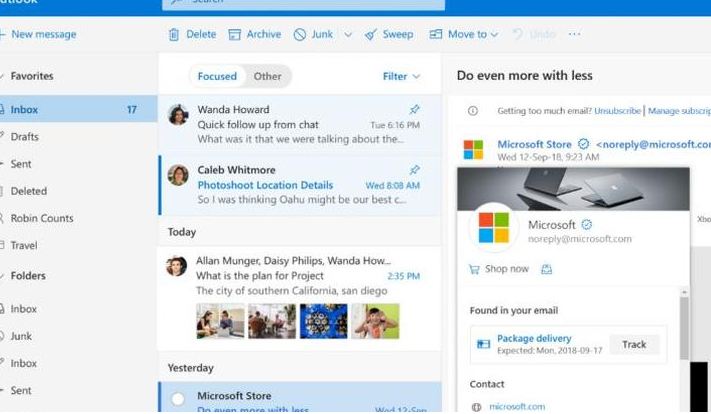
Microsoft is beta testing some new features for Outlook.com that are meant to help brands and businesses grow their presence and promotion capabilities.The Microsoft Business Profile experience will offer customers the ability to become a verified business with Microsoft. A blue check mark will flag Outlook.com emails from verified businesses. […]
Haythem Elmir
Russia’s Hackers Long Tied to Military, Secret Services
During the Soviet era, the country’s top computer scientists and programmers largely worked for the secret services. That practice appears to have resumed under President Vladimir Putin, as Russia faces accusations of waging a global campaign of cyber attacks. Dutch officials on Thursday accused four Russians from the GRU military intelligence […]
D-Link Security Updates Fixed Multiple Vulnerabilities in WiFiManager Software
D-Link Security Updates fixed vulnerabilities with Central WiFiManager Software Controller that allows an attacker to execute the code remotely with system permissions. The vulnerabilities were discovered by Core Security Consulting Services and these vulnerabilities directly impact the software package and put the host computer at risk. The Central WiFiManager Software […]
Sony Bravia Smart TVs affected by a critical vulnerability
Experts at FortiGuard Labs team discovered three vulnerabilities in eight Sony Bravia smart TVs, one of them rated as critical. Patch management is a crucial aspect for IoT devices, smart objects are surrounding us and represent a privileged target for hackers. Experts at FortiGuard Labs team discovered three vulnerabilities (a stack […]
La Tunisie s’inquiète pour sa cyberdéfense
La sécurité des personnes et des biens n’ont cessé, ces dernières années, de croitre, mais paradoxalement, avec l’évolution technologique et informatique, la cybercriminalité n’a fait qu’augmenter. Les menaces qui pèsent sur le cyberespace sont bien réelles, allant de la « militarisation » des réseaux sociaux, aux cyberattaques orchestrées par les États en […]
Windows 10 : arrêtez tout ! La mise à jour d’octobre effacerait les données personnelles !
L’édition « October 2018 Update » de Windows 10, déployée cette semaine par Microsoft, serait victime d’un énorme bug : la mise à jour supprimerait purement et simplement les données personnelles des utilisateurs. Disponible depuis quelques jours, la nouvelle édition de Windows 10 fait décidément beaucoup parler d’elle, et pas nécessairement en […]
ThreatList: 83% of Routers Contain Vulnerable Code
Five out of six name brand routers, such as Linksys, NETGEAR and D-Link, contain known open-source vulnerabilities. A staggering 83 percent of home and office routers have vulnerabilities that could be exploited by attackers. Of those vulnerable, over a quarter harbor high-risk and critical vulnerabilities, according to a report released […]
Instagram Influencers Targeted in Ransomware Campaign
The company does not have two-factor authentication set by default High-profile accounts on Instagram are being targeted by phishing and ransomware attacks, with evidence that many are paying the attackers. Hackers are gaining access to accounts via phishing scams; posing as personal representatives from well known branding companies, they are […]
Mozilla Releases Critical Security Update For Thunderbird
Mozilla releases security updates for Thunderbird that fixes one critical vulnerability, two high-level vulnerabilities, and three medium level vulnerabilities. Critical vulnerability CVE-2018-12376: Memory corruption issue that may allow an attacker to run arbitrary code on the vulnerable machine. The Vulnerability has a critical impact. High-level Vulnerability CVE-2018-12378: Use-after-free vulnerability occur […]
Make it a cyber-habit: Five simple steps to staying safe online
What are some essential steps you can take to increase your online safety – now and in the long run? Here’s a question: What makes October special beyond Oktoberfest – which mostly takes place in September, anyway? Correct, October is recognized as European Cyber Security Month in Europe and as National Cyber Security […]