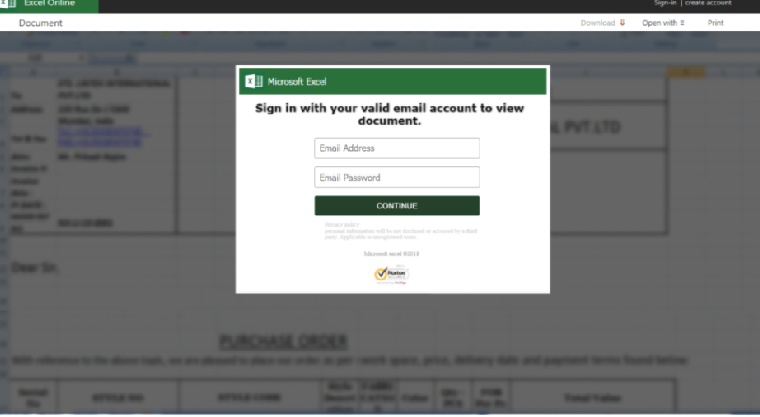
A threat actor was observed targeting Drupal vulnerabilities patched earlier this year to install a backdoor on compromised servers, IBM reports. The hackers target CVE-2018-7600, or Drupalgeddon2, a critical vulnerability found to impact Drupal versions 6, 7 and 8, but which was addressed in March this year. Assigned a risk score […]
Haythem Elmir
Nouvelle backdoor TeleBots : Première preuve liant Industroyer à NotPetya
L’analyse par ESET d’une récente backdoor (ou porte dérobée) utilisée par TeleBots – le groupe à l’origine de l’épidémie massive de rançon de NotPetya – révèle de fortes similitudes de code avec la backdoor principale d’Industroyer, révélant une connexion rumeur qui n’avait pas été démontrée auparavant. rmi les incidents de […]
How Can Businesses Protect against Phishing Attacks on Employee Smartphones?
martphones have become synonymous with everyday business operations, enabling employees to store important contact details, browse the web and reply to emails while on the move. However, the ubiquity of such devices has led scammers to increasingly target them with a variety of phishing attacks – all designed to […]
New Backdoor Ties NotPetya and Industroyer to TeleBots Group
Security researchers found the missing link that helps them prove that the NotPetya disk-wiping malware and the Industroyer backdoor for electric power systems are the work of the TeleBots group. Both pieces of malware were used in attacks against targets in Ukraine and researchers have found clues in the past pointing to the […]
Innovative Phishing Tactic Makes Inroads Using Azure Blob
A brand-new approach to harvesting credentials hinges on users’ lack of cloud savvy. A fresh tactic for phishing Office 365 users employs credential-harvesting forms hosted on Azure Blob storage – signed with legitimate Microsoft SSL certificates to lend an air of legitimacy. Azure Blob Storage is a cloud storage solution […]
Italian Police Finally Identified 25-Year-old Italian Hacker who have Defaced NASA Websites
After 5 years Italian police identified the hacker who is behind the NASA Websites hack and sixty institutional sites of local authorities. The Hackers almost defaced around 70 websites that belong to Italian and foreign institutional sites along with American spy agencies and 8 NSA owned domainsback in 2013. A 23-year-old […]
New Gallmaker APT group eschews malware in cyber espionage campaigns
A previously unknown cyber espionage group, tracked as Gallmaker, has been targeting entities in the government, military and defense sectors since at least 2017. A new cyber espionage group tracked as Gallmaker appeared in the threat landscape. According to researchers from Symantec, who first spotted the threat actor, the group has launched […]
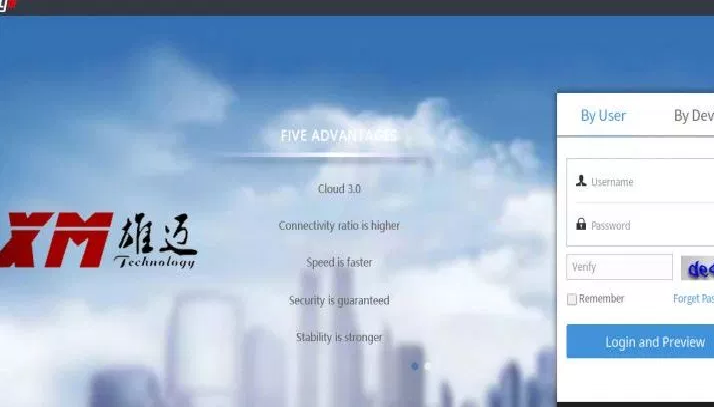
Millions of Xiongmai video surveillance devices can be easily hacked via cloud feature
Millions of Xiongmai video surveillance devices can be easily hacked via cloud feature, a gift for APT groups and cyber crime syndicates Security experts from security firm SEC Consult have identified over 100 companies that buy and re-brand video surveillance equipment (surveillance cameras, digital video recorders (DVRs), and network video recorders […]
Group-IB: $49.4 million of damage caused to Russia’s financial sector from cyber attacks
Security firm Group-IB has estimated that in H2 2017-H1 2018 cyber attacks caused $49.4 million (2.96 billion rubles) of damage to Russia’s financial sector Group-IB, an international company that specializes in preventing cyber attacks, has estimated that in H2 2017-H1 2018 cyber attacks caused $49.4 million (2.96 billion rubles) of […]
Meet GhostDNS: The dangerous malware behind IoT botnet targeting banks
Security researchers at NetLab, a sub-division of the Chinese cybersecurity firm Qihoo 360, have discovered a new, wide-scale, and very active malware campaign that has managed to hijack more than 100,000 home routers between Sept 21 and 27. A majority of routers (almost 88%) are located in Brazil. The malware […]