The malicious apps have all been removed from the official Android store but not before the apps were installed by almost 30,000 users Malware authors keep testing the vigilance of Android users by sneaking disguised mobile banking Trojans into the Google Play store. We’ve recently analyzed a set of 29 […]
Haythem Elmir
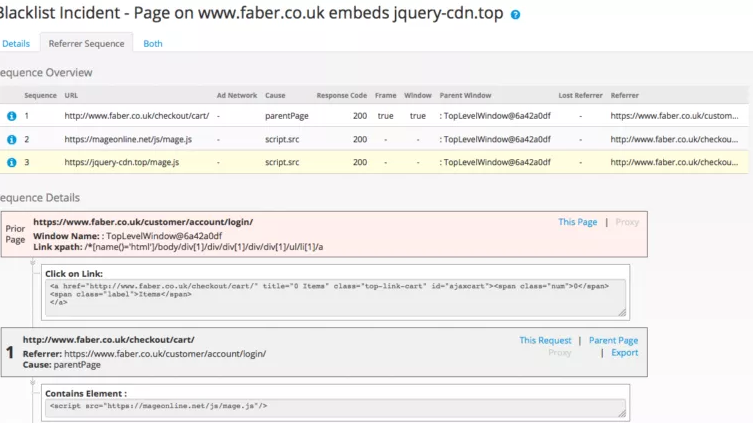
Magecart hackers change tactic and target vulnerable Magento extensions
Magecart cybercrime gang made the headlines again, the cyber criminal gang is now targeting vulnerable Magento Extensions. Magecart cybercrime gang switches tactic, it is now targeting vulnerable Magento extensions. instead of compromising large websites or third-party services to steal credit card data. In previous campaigns, attackers customize the attack for each victim tailoring the code […]
Chalubo, a new IoT botnet emerges in the threat landscape
Security experts from Sophos Labs have spotted a new piece of IoT malware tracked as Chalubo that is attempting to recruit devices into a botnet used to launch DDoS attacks. Security experts from Sophos Labs have spotted a new piece of Linux malware tracked as Chalubo (ChaCha-Lua-bot) that is targeting IoT devices in an […]
Signal Desktop Leaves Message Decryption Key in Plain Sight
A mistake in the process used by the Signal Desktop application to encrypt locally stored messages leaves them wide open to an attacker. When Signal Desktop is installed, it will create an encrypted SQLite database called db.sqlite, which is used to store the user’s messages. The encryption key for this database is automatically generated […]
Firefox Targeting Competing VPN Sites With ProtonVPN Offer in New Test
Mozilla has announced a Shield study where Firefox will promote the ProtonVPN service as a new revenue source. BleepingComputer was able to gain access to the study’s extension and it appears that the ProtonVPN will be recommended when visiting VPN provider sites, streaming services, or when connecting to insecure wireless […]
Again Hacker Exposed New Microsoft Unpatched Zero-day Bug In Twitter With PoC
New Microsoft unpatched Zero-day bug exposed in online again along with proof-of-concept(PoC) by the same security researcher who has previously leaked another critical zero-day vulnerability in Twitter. Previously exposed Windows Zero-day vulnerability exploit online that discovered in Microsoft Windows Task Scheduler. Twitter name SandboxEscaper, A security researcher famous for leaking Zero-day bugs online along with PoC […]
Tunisie : “Elissa”, c’est le futur nom d’un nouveau système de gestion électronique des courriers
Un nouveau système national de gestion électronique des courriers baptisé “Elissa” verra prochainement le jour et s’ajoutera aux systèmes relevant du Centre national de l’informatique (CNI). C’est Anouar Mâarouf, ministre des Technologies de la Communication et de l’Economie numérique, qui l’a annoncé, lundi 22 octobre à l’Assemblée des représentants du peuple […]
GitHub is down because of data storage issues (Updated)
Update: October 23(4:33 AM IST/ 1:03 AM CEST): GitHub noted on its status blog that all the services are now up and running. Update: (3:26PM IST/ 11:56PM CEST) GitHub said that the majority of restore processes have completed. And they anticipate all data stores will be fully consistent within the next hour. Update (03:17PM IST / 11:47AM CEST): GitHub noted that it needs […]
FreeRTOS IoT OS Critical Vulnerabilities Affected Million of Smart Home & Critical Infrastructure Based IoT Devices
A critical Vulnerabilities that affected FreeRTOS TCP/IP Stack puts millions of IoT devices at risk and let attackers allows to compromise the Smart home devices and Critical Infrastructure Systems. FreeRTOS is a real-time operating system kernel for embedded devices that support various architectures such as Altera Nios II, ARM architecture, Fujitsu, Microchip Technology, STMicroelectronics etc. Vulnerabilities affected multiple Versions of […]
Tesla Car Has Been Hacked and Stolen By Intercepting the Signal From Key Fob
Hackers steal a Tesla Model S car by intercepting the signal from car’s key fob with a tablet to unlock and start the car. The car was stolen by capturing its passive entry that used to automatically unlock the car when approached with the key. Antony Kennedy who lives in […]