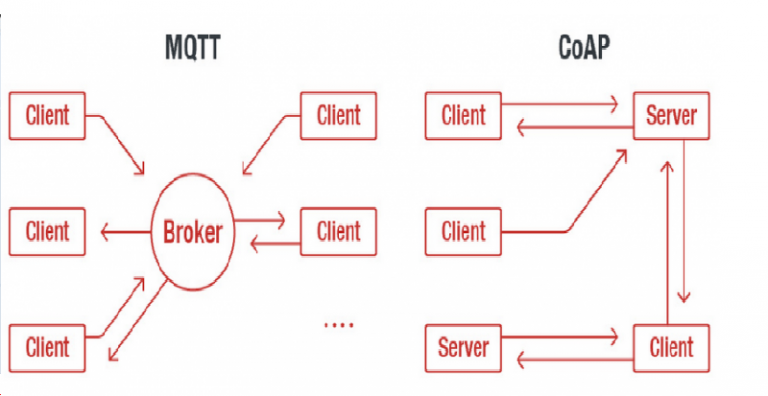
Security experts from Trend Micro discovered that some machine-to-machine (M2M) protocols can be abused to attack IoT and industrial Internet of Things (IIoT) systems. According to a study conducted by experts from Trend Micro and the Polytechnic University of Milan. attackers abuse M2M protocols to target IoT and IIoT devices. The experts […]
Haythem Elmir
New strain of Ransomware infected over 100,000 PCs in China
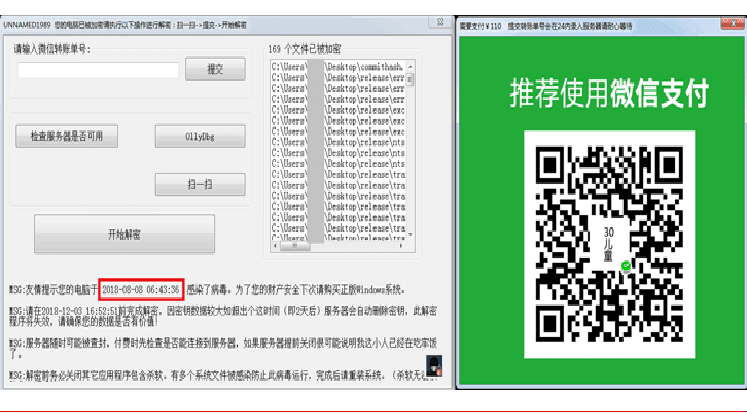
New strain of Ransomware infected over 100,000 PCs in China Security experts reported a new strain of malware spreading in China, the malicious code rapidly infected over 100,000 PCs in just four days. Unfortunately, the number of infections is rapidly increasing because hackers compromised a supply chain. It is […]
Email accounts of top NRCC officials were hacked in 2018
Email accounts of top NRCC officials were hacked in 2018 Threat actors had access to the email accounts of at least four NRCC aides and spied on thousands of sent and received emails for several months. The email system at the National Republican Congressional Committee (NRCC), the Republican Party’s campaigning […]
Données personnelles compromises : Uber condamné à 1 M€ d’amende
Les autorités de protection des données des Pays-Bas et du Royaume-Uni mettent Uber à l’amende, pour un total de 1 M€, pour avoir compromis les données personnelles d’utilisateurs lors d’une intrusion en 2016, soit avant l’arrivée du RGPD. La plateforme américaine n’avait pas prévenu les personnes concernées. 57 millions d’utilisateurs […]
500 Million Marriott Guest Records Stolen in Starwood Data Breach
500 Million Marriott Guest Records Stolen in Starwood Data Breach The world’s biggest hotel chain Marriott International today disclosed that unknown hackers compromised guest reservation database its subsidiary Starwood hotels and walked away with personal details of about 500 million guests. Starwood Hotels and Resorts Worldwide was acquired by Marriott […]
Hacker hijacks printers worldwide to promote popular YouTube channel
The TheHackerGiraffe used the Printer Exploitation Toolkit (PRET) to hijack +50k vulnerable printers to Promote PewDiePie YouTube Channel. An anonymous hacker hijacked over 50,000 internet-connected printers worldwide to print out messages promoting the subscription to the PewDiePie YouTube channel. Felix Arvid Ulf Kjellberg, aka PewDiePie, is a popular Swedish Youtuber, comedian, and video game commentator, formerly best […]
ETERNALSILENCE – 270K+ devices vulnerable to UPnProxy Botnet build using NSA hacking tools
Over 270,000 connected devices run vulnerable implementations of UPnP, threat actors are attempting to recruit them in a multi-purpose botnet. In April, Akamai reported that threat actors compromised 65,000 home routers by exploiting vulnerabilities in Universal Plug’N’Play (UPnP), experts tracked the botnet as UPnProxy. Now the company provided an update to […]
New PowerShell-based Backdoor points to MuddyWater
Security researchers at Trend Micro recently discovered PowerShell-based backdoor that resembles a malware used by MuddyWater threat actor. Malware researchers at Trend Micro have discovered a Powershell-based backdoor that is very similar to a malware used by MuddyWater APT group. The first MuddyWater campaign was observed in late 2017, then researchers from Palo Alto Networks […]
U.S Charges Two Iranian Hackers for SamSam Ransomware Attacks
U.S Charges Two Iranian Hackers for SamSam Ransomware Attacks The Department of Justice announced Wednesday charges against two Iranian nationals for their involvement in creating and deploying the notorious SamSam ransomware. The alleged hackers, Faramarz Shahi Savandi, 34, and Mohammad Mehdi Shah, 27, have been charged on several counts of computer hacking […]
Dell data breach – Dell forces password reset after the incident
Dell data breach – Dell forces password reset after the incident Dell data breach – IT giant Dell disclosed a data breach, the company confirmed it has detected an intrusion in its systems on November 9th 2018. Attackers were trying to exfiltrate customer data (i.e. names, email addresses, and hashed passwords) […]