All these numbers…. « More than 5 billion records from 6,500 data breaches were exposed in 2018 » — a report from Risk Based Security says. « More than 59,000 data breaches have been reported across the European since the GDPR came into force in 2018 » — a report from DLA Piper says. […]
Haythem Elmir
Facebook login phishing campaign can deceive tech-savvy users
Security experts at Myki have recently discovered a new phishing campaign that could deceive even most tech-savvy users. The technique relies upon the concept of being able to reproduce a social login prompt in a very realistic format inside an HTML block. Crooks are distributing links to blogs and services that display […]
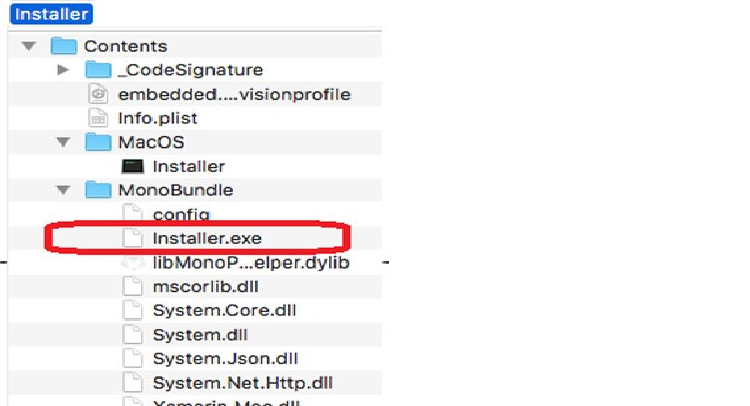
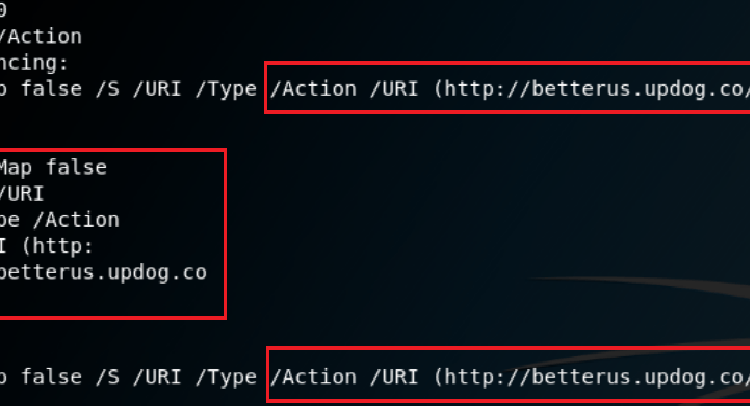
Windows App runs on Mac to download MacOS malware
Experts at Trend Micro have detected a new strain of MacOS malware that hides inside a Windows executable to avoid detection. Security experts at Trend Micro have spotted a new strain of MacOS malware disguises itself as a Windows executable file to evade detection. The malware is carried via .EXE file […]
Toyota PASTA Car-Hacking Tool will be soon on GitHub
Takuya Yoshida from Toyota’s InfoTechnology Center and his colleague Tsuyoshi Toyama are members of a Toyota team that developed the new tool, called PASTA (Portable Automotive Security Testbed). PASTA is an open-source testing platform specifically designed for car hacking, it was developed to help experts to test cyber security features of […]
Experts found a way to create a super-malware implanted in SGX-enclaves
Researchers devised a new technique to hide malware in the security Intel SGX enclaves, making it impossible to detect by several security technologies. Security researchers devised a new technique to hide malware in the security Intel SGX enclaves. Intel Software Guard eXtensions (SGX) is a technology for application developers that allows protecting select code […]
Malicious PDF Analysis
In the last few days I have done some analysis on malicious documents, especially PDF. Then I thought, “Why not turn a PDF analysis into an article?” Let’s go to our case study: I received a scan request for a PDF file that was reported to support an antivirus vendor, and it […]
Hacker deleted all data from VFEmail Servers, including backups
A destructive cyberattack hit the email provider VFEmail, a hacker wiped its servers in the United States, including the backup systems. An unknown attacker has launched a destructive cyber attack against the email provider VFEmail, he erased information on its server including backups, 18 years’ worth of customer emails were […]
Microsoft Patch Tuesday updates for February 2019 fixes IE Zero-Day
Microsoft released Patch Tuesday updates for February 2019 that address 77 flaws, including an Internet Explorer issue that has been exploited in attacks. Microsoft released Patch Tuesday updates for February 2019 that address 77 flaws, 20 critical vulnerabilities, 54 important and 3 moderate in severity. One of the issue fixed by the […]
620 million accounts stolen from 16 hacked websites available for sale on the dark web
620 million accounts stolen from 16 hacked websites (Dubsmash, Armor Games, 500px, Whitepages, ShareThis) available for sale on the dark web The Register revealed in exclusive that some 617 million online account details stolen from 16 hacked websites are available for sale on the dark web. The advertising for the sale of the […]
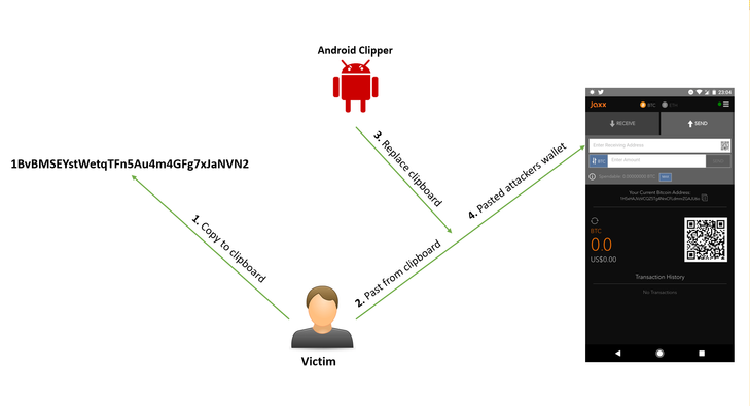
First Android Clipboard Hijacking Crypto Malware Found On Google Play Store
A security researcher has discovered yet another cryptocurrency-stealing malware on the official Google Play Store that was designed to secretly steal bitcoin and cryptocurrency from unwitting users. The malware, described as a « Clipper, » masqueraded as a legitimate cryptocurrency app and worked by replacing cryptocurrency wallet addresses copied into the Android […]