Threat intelligence (TI) is at the maturity level to become a decision making tool. TI refers to evidence based information including context such as mechanisms, Indicators of Compromise (IOC), Indicators of Attribution (IOA), implications and actionable advice about existing or emerging hazards to assets. TI allows the technical staff professionals […]
Haythem Elmir
Réseaux sociaux : vers une meilleure protection de la vie privée ?
A l’heure où les internautes du monde entier jugent indispensable de pouvoir partager en ligne leur intimité avec tous leurs amis, réels et virtuels, et où la société Facebook a annonce qu’elle a adépassé les 2 milliards d’utilisateurs en juin 2017. Twitter aussi fait désormais partie intégrante des principaux réseaux sociaux. Il […]
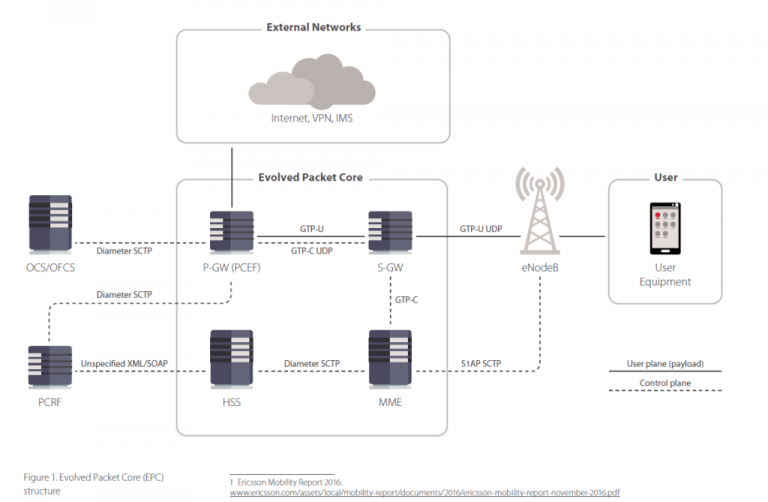
4G/5G Wireless Networks as Vulnerable as WiFi and putting SmartCities at Risk
Researchers from security firm Positive Technologies warns of 4G/5G Wireless Networks as vulnerable as WiFi and putting smart-cities at risk The Internet of Things (IoT) presents many new opportunities and some different challenges. The vast number of devices makes it very expensive to connect everything with traditional network cabling and in many […]
ASD revealed hacker stole 30GB of sensitive data on Australia’s military capabilities
The Australia’s foreign intelligence agency, the Australian Signals Directorate (ASD), admitted a hacker has stolen over 30 GB of military documents. Stolen data includes details on fighter jets, military aircraft, and naval ships. The hacker stole the huge trove of confidential data on military capabilities at an unnamed Department of […]
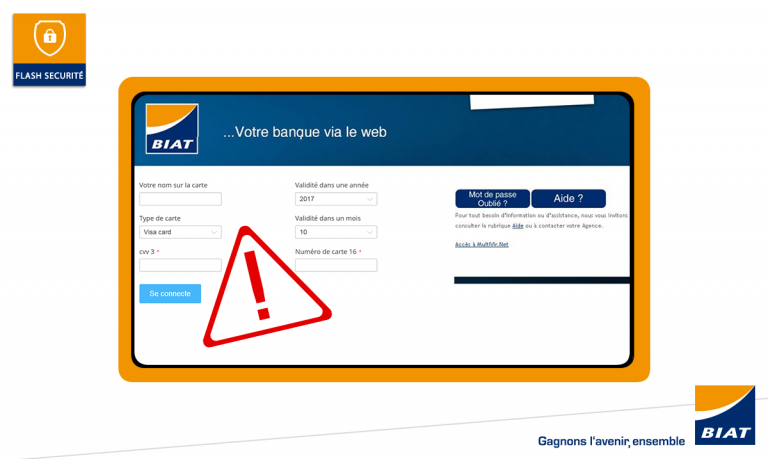
La BIAT victime d’une tentative d’attaque par Phishing
La BIAT attire l’attention de ses clients sur un site web fictif ( https://biatnet.yolasite.com/ ) qui usurpe l’identité visuelle de son vrai site de banque en ligne BIATNET . La BIAT tient à préciser qu’elle n’est pas associée à ce site et vous invite à ne pas y accéder. Ce site fictif […]
Ingénierie sociale, anatomie d’une attaque classique
Ingénierie sociale, les bons réflexes
North Korea and Iran Use CodeProject to Develop Their Malware
Software developers and malware authors share a desire to work smart, not hard In the software development world, engineers frequently use ready-made code for various tasks, whether it involves copying a snippet from Stack Overflow, taking a library from Github, or reusing a company’s own rich, legacy code base. On […]
FIN7 Hackers Change Attack Techniques
The financially-motivated FIN7 hacking group recently switched to a new delivery technique and has been employing a different malware obfuscation method, ICEBRG security researchers reveal. Highly active since the beginning of 2017, FIN7 (also known as Anunak, or Carbanak) started distributing malware via LNK files embedded in Word documents using […]
4G/5G Wireless Networks as Vulnerable as WiFi and putting SmartCities at Risk
Researchers from security firm Positive Technologies warns of 4G/5G Wireless Networks as vulnerable as WiFi and putting smart-cities at risk The Internet of Things (IoT) presents many new opportunities and some different challenges. The vast number of devices makes it very expensive to connect everything with traditional network cabling and […]