A new Mirai variant is rapidly spreading, experts observed around 100K IPs running the scans in the past 60 hours searching for flawed ZyXEL PK5001Z routers. According to Li Fengpei, a security researcher with Qihoo 360 Netlab, the publication of the proof-of-concept (PoC) exploit code in a public vulnerabilities database is […]
Haythem Elmir
The Cobalt group is exploiting the CVE-2017-11882 Microsoft Office flaw in targeted attacks
A few days after details about the CVE-2017-11882 Microsoft Office flaw were publicly disclosed, the firm Reversing Lab observed Cobalt group using it. A few days after details about the CVE-2017-11882 Microsoft Office vulnerability were publicly disclosed, security experts from firm Reversing Lab observed criminal gang using it in the wild. The gang is […]
Unix mailer Exim is affected by RCE, DoS vulnerabilities. Apply the workaround asap
The Exim Internet mail message transfer agent warned of flaws through the public bug tracker, sys admins have to apply the workaround asap. Exim is a message transfer agent (MTA) developed at the University of Cambridge for use on Unix systems connected to the Internet, it is the most popular MTA on the […]
Facebook Flaw Allowed Removal of Any Photo
A researcher says he received a $10,000 bounty from Facebook after finding a critical vulnerability that could have been exploited to delete any photo from the social media network. In early November, Facebook announced a new feature for posting polls that include images and GIF animations. Iran-based security researcher and […]
Imgur—Popular Image Sharing Site Was Hacked In 2014; Passwords Compromised
Only after a few days of Uber admitting last year’s data breach of 57 million customers, the popular image sharing site disclosed that it had suffered a major data breach in 2014 that compromised email addresses and passwords of 1.7 million user accounts. In a blog post published on Friday, […]
SAML POST-INTRUSION ATTACK MIRRORS ‘GOLDEN TICKET’
Researchers at CyberArk Labs have created a post-intrusion attack technique known as a Golden SAML that could allow an attacker to fake enterprise user identities and forge authentication to gain access to valuable cloud resources in a federation environment. “Using this post-exploit technique, attackers can become any user they want […]
Data release: list of websites that have third-party “session replay” scripts
Here’s the list of 1,239 popular websites using third-party “session replay” scripts to record your every keystroke and mouse movement. In a recent study we analyzed seven “session replay” services and revealed how they exfiltrate sensitive user data. Here we release the data behind our study, specifically, the list of […]
OVH choisit Ooredoo Tunisie pour un hébergement sécurisé et réglementaire des noms de domaines ».tn » et » تونس. » sur le territoire tunisien
Ooredoo Tunisie, opérateur-hébergeur leader, et OVH, leader européen du cloud, ont scellé un partenariat visant à rapatrier les serveurs DNS de l’ensemble des noms de domaine gérés par OVHportant l’extension «.tn » ou « تونس.» sur le territoire tunisien. Ces données seront recueillies dans le datacenter de l’opérateur situé à Mghira et […]
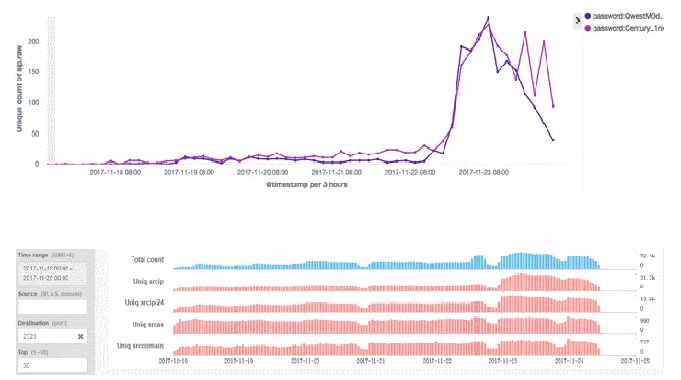
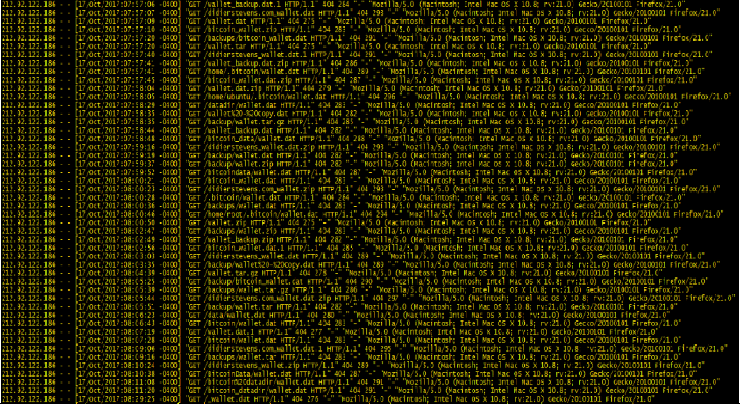
There’s Some Intense Web Scans Going on for Bitcoin and Ethereum Wallets
With both Bitcoin and Ethereum price hitting all-time highs in the past seven days, cyber-criminals have stepped up efforts to search and steal funds stored in these two cryptocurrencies. These mass Internet scanning campaigns have been recently picked up by various honeypots installed by security researchers across the Internet. Scans […]
Only 12% or organizations are likely to detect a sophisticated cyber attack
Organizations believe that today’s cyber threat landscape places them at high risk of cyber attacks. The EY survey of nearly 1,200 C-level leaders of the world’s largest and most recognized organizations examines some of the most urgent concerns about cybersecurity and their efforts to manage them. Findings show that […]