LONDON (Reuters) – Britain blamed Russia on Thursday for a cyber-attack last year, publicly pointing the finger at Moscow for spreading a virus which disrupted companies across Europe including UK-based Reckitt Benckiser. The so-called NotPetya attack in June started in Ukraine where it crippled government and business computers before spreading […]
Haythem Elmir
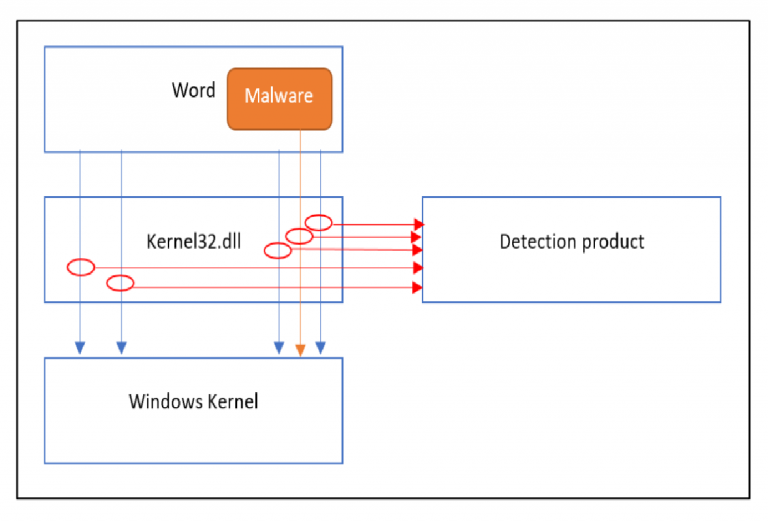
Hackers Keep it Simple: Malware Evades Detection by Simply Copying a File
Hackers Keep it Simple: Malware Evades Detection by Simply Copying a File New malware technique evades detection by simply copying a file We break it down step-by-step to show you how it works Innovative hackers continue to deliver sophisticated malware that evades detection The Bromium Lab is back to break […]
Unknown Threat Actor Conducts OPSEC Targeting Middle East
Hackers conduct OPSEC Targeting Middle East – Classified Documents That May Pertain To The Jordanian Research House Dar El-Jaleel Are Being Used As Bait In A Campaign Targeting The Middle East. The researchers Paul Rascagneres with help of Martin Lee, from CISCO TALOS, described a campaign of targeted attacks against the middle […]
Uber aurait enregistré des pertes s’élevant à 4,5 milliards USD en 2017
Sur l’année 2017, Uber aurait enregistré des pertes colossales s’élevant à 4,5 milliards USD. Ce déficit est largement supérieur aux 2,8 milliards USD de perte relevés en 2016 : près de 2 milliards USD de plus. Sur la base des données fournies par le site The Information et confirmées à l’AFP par Uber, le […]
Microsoft Patch Tuesday for February 2018 addresses 14 critical flaws
Microsoft Patch Tuesday for February 2018 addressed a total of 50 vulnerabilities in affecting Windows operating system, Microsoft Office, web browsers and other products of the tech giant. Fourteen issues are listed as critical, 34 are rated as important, and only two of them are rated as moderate in severity. […]
Microsoft Won’t Patch a Severe Skype Vulnerability Anytime Soon
A serious vulnerability has been discovered in Microsoft-owned most popular free web messaging and voice calling service Skype that could potentially allow attackers to gain full control of the host machine by granting system-level privileges to a local, unprivileged user. The worst part is that this vulnerability will not be […]
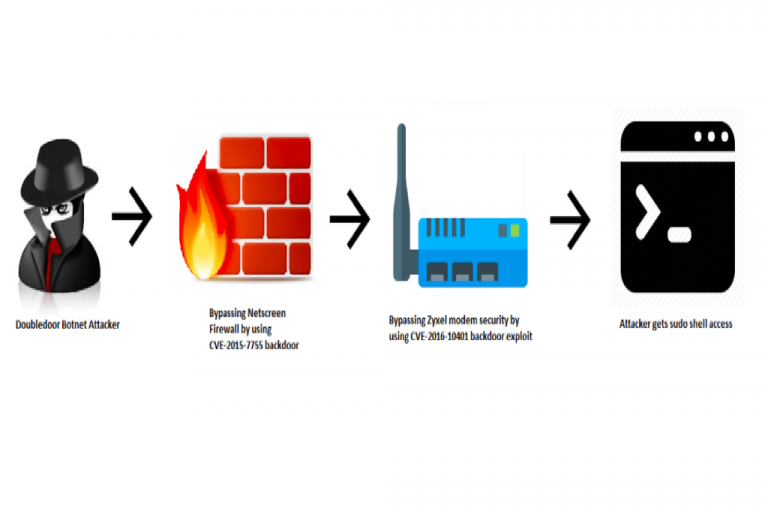
DoubleDoor, a new IoT Botnet bypasses firewall using two backdoor exploits
Security researchers spotted a new IoT botnet dubbed DoubleDoor that is able to bypass firewall as well as modem security using two backdoor exploits. IoT devices continue to be a privileged target of cyber criminals, cyber attackers against so-called smart objects has seen a rapid evolution. Security researchers at NewSky Security (NewSky Security) have […]
A new variant of the dreaded AndroRAT malware appeared in threat landscape
Security researchers from Trend Micro detected a new variant of the popular AndroRAT Android RAT in the criminal ecosystem. Security experts from Trend Micro reported the availability of a new variant of the popular AndroRAT. The malware was first born in 2012 as a university project, designed as an open-source client/server […]
Hackers in the Russian underground exploited a Telegram Zero-Day vulnerability to deliver malware
Security researcher Alexey Firsh at Kaspersky Lab last discovered a Telegram zero-day in the desktop Windows version that was exploited in attacks in the wild. Security researcher Alexey Firsh at Kaspersky Lab last discovered a zero-day vulnerability in the desktop Windows version of the popular Telegram instant messaging app. The […]
All You Need to Know About North Korea and its cyber army
What Type Of Technology Does North Korea Have? How Did The Country Begin Using Hackers? How Do Hacking Efforts Comply with the Political Situation? North Korea is not known for technological sophistication. The country does not have any global technological franchises, such as Apple or Samsung, and its citizens continue to […]