Security researchers have discovered 13 critical Spectre/Meltdown-like vulnerabilities throughout AMD’s Ryzen and EPYC lines of processors that could allow attackers to access sensitive data, install persistent malware inside the chip, and gain full access to the compromised systems. All these vulnerabilities lie in the secure part of the AMD’s Zen architecture […]
Haythem Elmir
Microsoft Admits It Incorrectly Upgraded Some Windows 10 Users to v1709
Microsoft admitted last week that it incorrectly updated some Windows 10 users to the latest version of the Windows 10 operating system —version 1709— despite users having specifically paused update operations in their OS settings. The admission came in a knowledge base article updated last week. Not all users of […]
Facebook Flaws Exposed Friend Lists, Payment Card Data
A researcher last year discovered some information disclosure vulnerabilities in Facebook that exposed users’ friend lists and partial payment card information. The social media giant patched one of the flaws within hours. Web security consultant Josip Franjković had been analyzing the Facebook application for Android when he identified a flaw […]
LARGE SCALE TROJAN ATTACKS SEEK CRYPTOCURRENCY
Despite Russia’s growing comfort with the crypto industry, they suffered large-scale attacks from cybercriminals attempting to install crypto mining malware this week. Nearly half a million computers experienced a persistent 12 hour attack. The attack was easily foiled On March 6, a large-scale attack on over 400 thousand PC’s took […]
Malware ‘Cocktails’ Raise Attack Risk
Malware mash-ups hiding in encrypted traffic are boosting attack numbers and increasing the danger to data, according to recent reports. It was good while it lasted. The drop in malware attacks seen in 2016 – from 8.19 billion in 2015 to 7.87 billion – is but a fond memory, as […]
Here’s a List of 29 Different Types of USB Attacks
Researchers from the Ben-Gurion University of the Negev in Israel have identified 29 ways in which attackers could use USB devices to compromise users’ computers. The research team has classified these 29 exploitation methods in four different categories, depending on the way the attack is being carried out. A) By […]
Update Samba Servers Immediately to Patch Password Reset and DoS Vulnerabilities
Samba has just released new security patches for two critical vulnerabilities that could allow unprivileged remote attackers to launch DoS attacks against servers and change any other users’ passwords, including admin’s. Samba is open-source software (re-implementation of SMB networking protocol) that runs on the majority of operating systems available today, […]
Researchers find critical flaws in SecurEnvoy SecurMail, patch now!
If you’re a user of SecurEnvoy SecurMail and you haven’t yet implemented the latest patch, do so now – or risk getting your encrypted emails read by attackers. The warning comes from SEC Consult researchers, who discovered a number of vulnerabilities in the product that break its core security […]
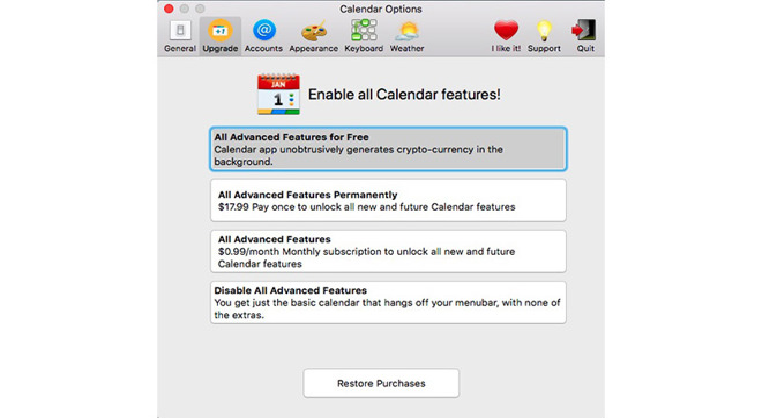
Mac Software Mines Cryptocurrency in Exchange for Free Access to Premium Account
Would you be okay with allowing a few paid services to mine cryptocurrencies using your system instead of paying the subscription fee? Most free websites and services often rely on advertising revenue to survive, but now there is a new way to make money—using customers’ computer to generate virtual […]
New Cyberespionage Attacks Linked to MuddyWater Campaign
Recent attacks targeting organizations in Turkey, Pakistan and Tajikistan appear to be linked to the previously detailed MuddyWater campaigns, according to Trend Micro. The MuddyWater campaigns were named so because of a high level of confusion they managed to create, thus making it difficult to attribute to a specific actor. […]