On March 22, a ransomware outbreak hit Atlanta city government systems, freezing not just the city’s technology but also its ability to get work done.
As a result of the outbreak, the city’s 8,000 employees were unable to use their PCs for several days (see Atlanta After Ransomware Attack: Please Restart Your PC).
The outbreak disrupted access to email, Oracle financial software, Siebel customer relationship management applications and Accela « civic engagement » software, as well as a Capricorn software self-service portal for residents. As a result, city residents were unable to pay for everything from water bills to parking tickets.
City officials said they also ordered Atlanta’s airport WiFi to be taken offline, « out of an abundance of caution. »
Atlanta has not confirmed whether it did or did not pay a ransom to attackers to help restore systems. City officials didn’t immediately respond to a request for comment, although they have previously said the city had backups and was using them to restore systems (see Crypto-Locking Malware Hits Atlanta, Baltimore, Boeing).
Based on the city’s cleanup bill, however, Atlanta appears to have brought in incident response and consulting firms to help it restore systems from backups.
Awarded Emergency Procurements
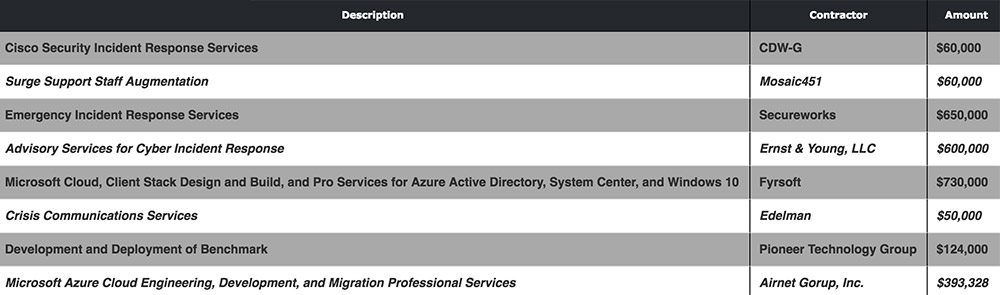
A list of « awarded emergency procurements » published by the city of Atlanta shows that from March 22 to April 2, the city paid eight different firms to assist with ransomware cleanup efforts, including $600,000 to Ernst & Young for « advisory services for cyber incident response »; $650,000 to Dell’s SecureWorks and $60,000 to Cisco Security for incident response services; $60,000 for « surge support staff augmentation »; and $50,000 to public relations firm Edelman for « crisis communications services. » The city also paid two service providers – $730,000 to Fyrsoft and $393,328 to Airnet Group – for help with its Microsoft environment, including Azure cloud, Windows 10 devices as well as « client stack design and build. »
As part of its cleanup efforts, the city said that it was migrating some on-premises applications to cloud services, as well as to help defend against repeat ransomware attacks.
City officials didn’t immediately respond to a query about whether there might be further ransomware cleanup expenses.
Missed Opportunity: Prevention
Experts say it would have been better for the city of Atlanta if it had properly budgeted to prevent the ransomware outbreak from ever occurring.
 Alert issued by the city of Atlanta on March 22.
Alert issued by the city of Atlanta on March 22.« Looking at the fallout from the Atlanta ransomware incident … they may have spent $2.6 million reactively, but that money would have gone much farther if spent to prevent such an incident in the first place, » says Jake Williams, head of cybersecurity consultancy Rendition Infosec, via Twitter.
Security experts say there were obvious flaws that should have been eradicated, including servers with incorrectly configured ports that left city systems vulnerable to remote compromise. « Atlanta’s flaw is failing to do the very basics. It’s kinda pointless asking which of the basic flaws was the one that let SamSam in their network, » said Robert Graham, head of offensive security research firm Errata Security, via Twitter
But Atlanta is hardly unique, Graham says. « Municipal, county, state governments are notoriously bad at doing the basics of IT and cybersecurity. Thus, what happened to Atlanta is likely in their future as well. »
SamSam Epidemic
Indeed, Atlanta is one of a number of public sector as well as healthcare organizations that are known to have fallen victim in recent months to SamSam ransomware (see Crypto-Locking Ransomware Attacks Spike).
« It seems most SamSam attacks are carried out by a human using legitimate credentials – usually stolen from a third-party vendor – actively working on the victim network and looking for ways to propagate and elevate privileges, » Max Henderson, a security analyst at Pondurance – a security consulting firm that helped the Hancock Health healthcare system recover from its Jan. 11 SamSam outbreak – told Information Security Media Group.
Hancock Health reported in January that it paid its attacker four bitcoins – worth about $55,000 at the time – to receive a decryption key that did enable it to unlock its crypto-locked systems (see HHS Warns of SamSam Ransomware Attacks).
Preparation Prevents Ransomware
Security experts and law enforcement officials have long urged organizations to invest in ransomware defenses in advance, so they’re not left in the position of having to decide whether to pay attackers for a decryption key that may or may not work (see Ransomware: Your Money or Your Life).
Paying attackers, experts warn, provides an incentive for criminals to continue such attacks – sometimes hitting the same victim multiple times – and directly funds cybercrime research and development. But the choice of whether to pay rests with victims (see Ransomware: Is It Ever OK to Pay?).
To read the original article:
https://www.govinfosecurity.com/atlantas-ransomware-cleanup-costs-hit-26-million-a-10888
