New Microsoft unpatched Zero-day bug exposed in online again along with proof-of-concept(PoC) by the same security researcher who has previously leaked another critical zero-day vulnerability in Twitter.
Previously exposed Windows Zero-day vulnerability exploit online that discovered in Microsoft Windows Task Scheduler.
Twitter name SandboxEscaper, A security researcher famous for leaking Zero-day bugs online along with PoC and now she exposed second Microsoft Zero-day bug.
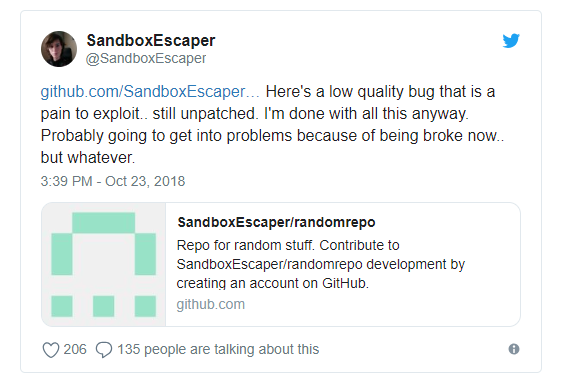
Also she said, “Not the same bug I posted a while back, this doesn’t write garbage to files but actually deletes them.. meaning you can delete application dll’s and hope they go look for them in user write-able locations. Or delete stuff used by system services c:\windows\temp and hijack them.”
This Vulnerability referred as a Deletebug and it allows non-admins to delete any file by abusing a new Windows service not checking permissions again.
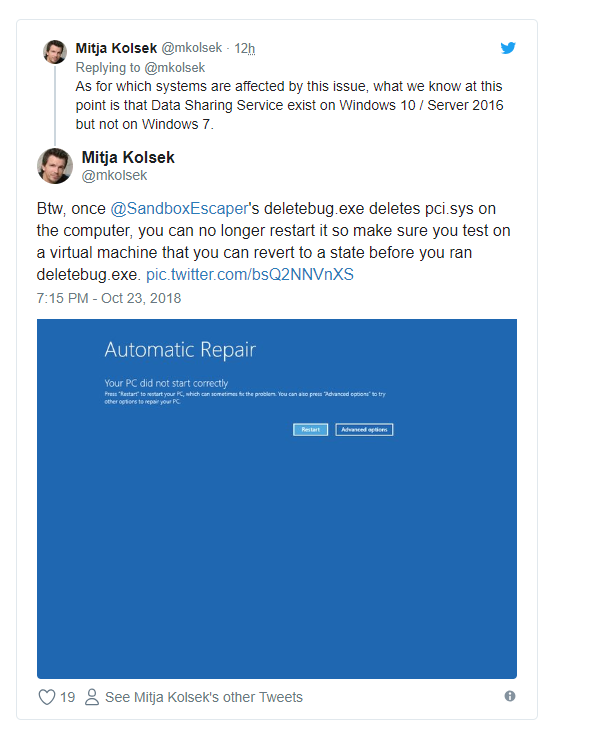
Experts who have analyzed this bug believes that once @SandboxEscaper‘s deletebug.exe deletes pci.sys on the computer, you can no longer restart it so make sure you test on a virtual machine that you can revert to a state before you ran deletebug.exe.
Mitja Kolsek, Co-founder of 0patch said, This Unpatched Zero-day exactly affecting data sharing service (dssvc.dll)which is only presented in exist on Windows 10 / Server 2016 but not on Windows 7 And Windows 8.
“The Internet seems to know that it crashes a lot and it describes itself as “Provides data brokering between applications.”
Kevin Beaumont who analyzed this Zero-day believes that the current Zero-day that she exposed will only work in Windows 10 and Server 2016 and 2019.
To read the original article
https://gbhackers.com/microsoft-unpatched-zero-day-bug-online/
