An attacker is attempting to take advantage of the recent warnings about possible Iranian cyberattacks by using it as a theme for a phishing attack that tries to collect Microsoft login credentials.
With the rising escalations between the United States and Iran, the U.S. government has been issuing warnings about possible cyberattacks by Iran and potential attacks on critical U.S. infrastructure.
To take advantage of this increased tension, an attacker has created a phishing scam that pretends to be from ‘Microsoft MSA’ and has an email subject of ‘Email users hit by Iran cyber attack’ warning that Microsoft’s servers were hit by a cyberattack from Iran.
The phishing email goes on to say that in response to this attack, Microsoft was forced to protect their user by locking their email and data on Microsoft’s servers. To gain full access again to this locked data, the phishing email says that the recipient must log in again.
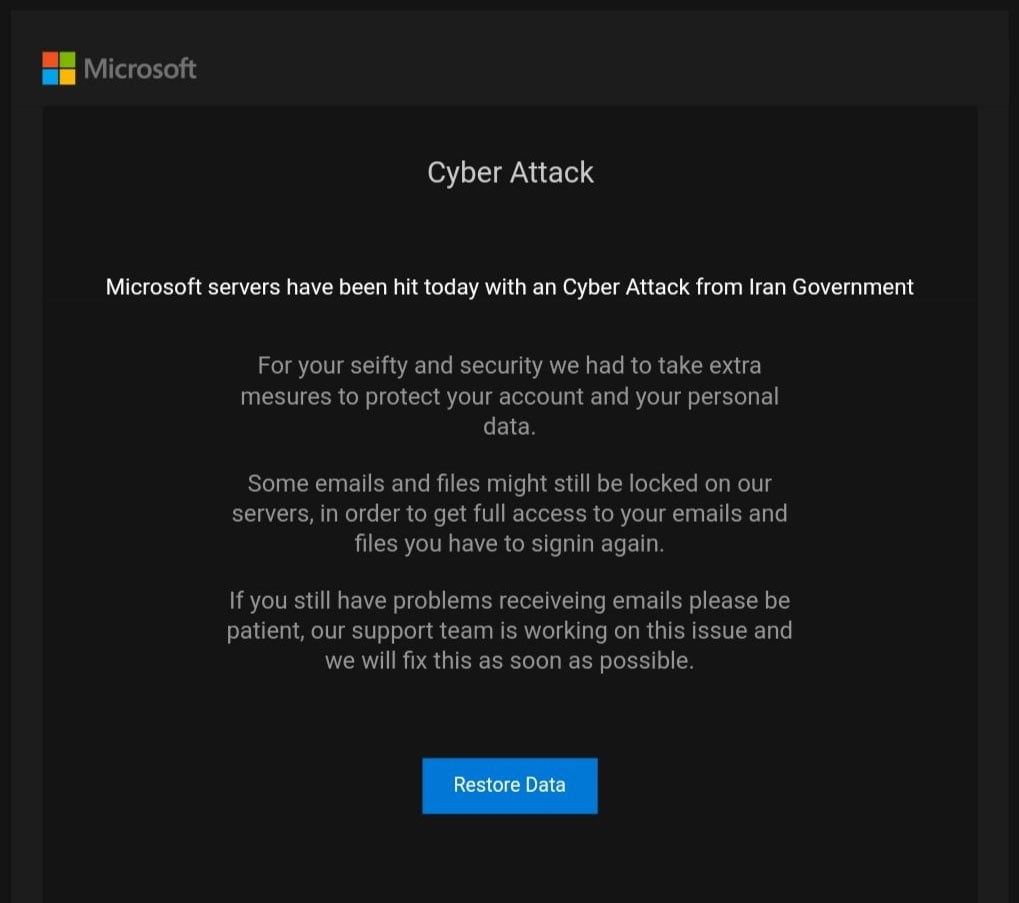
According to Michael Gillett, who received this phishing scam and shared it with BleepingComputer, it was able to bypass Outlook’s spam filters and arrive in the service’s inbox.
The full text of this phishing email, which needed a run through a spell checker, can be read below.
Cyber Attack
Microsoft servers have been hit today with an Cyber Attack from Iran Government
For your seifty and security we had to take extra mesures to protect your account and your personal data.
Some emails and files might still be locked on our servers, in order to get full access to your emails and files you have to signin again.
If you still have problems receiveing emails please be patient, our support team is working on this issue and we will fix this as soon as possible.
Restore Data
If a recipient clicks on the ‘Restore Data’ button, they will be redirected to a phishing landing page that pretends to be a Microsoft log in form. As you can see by the URL, this is not a legitimate Microsoft site.
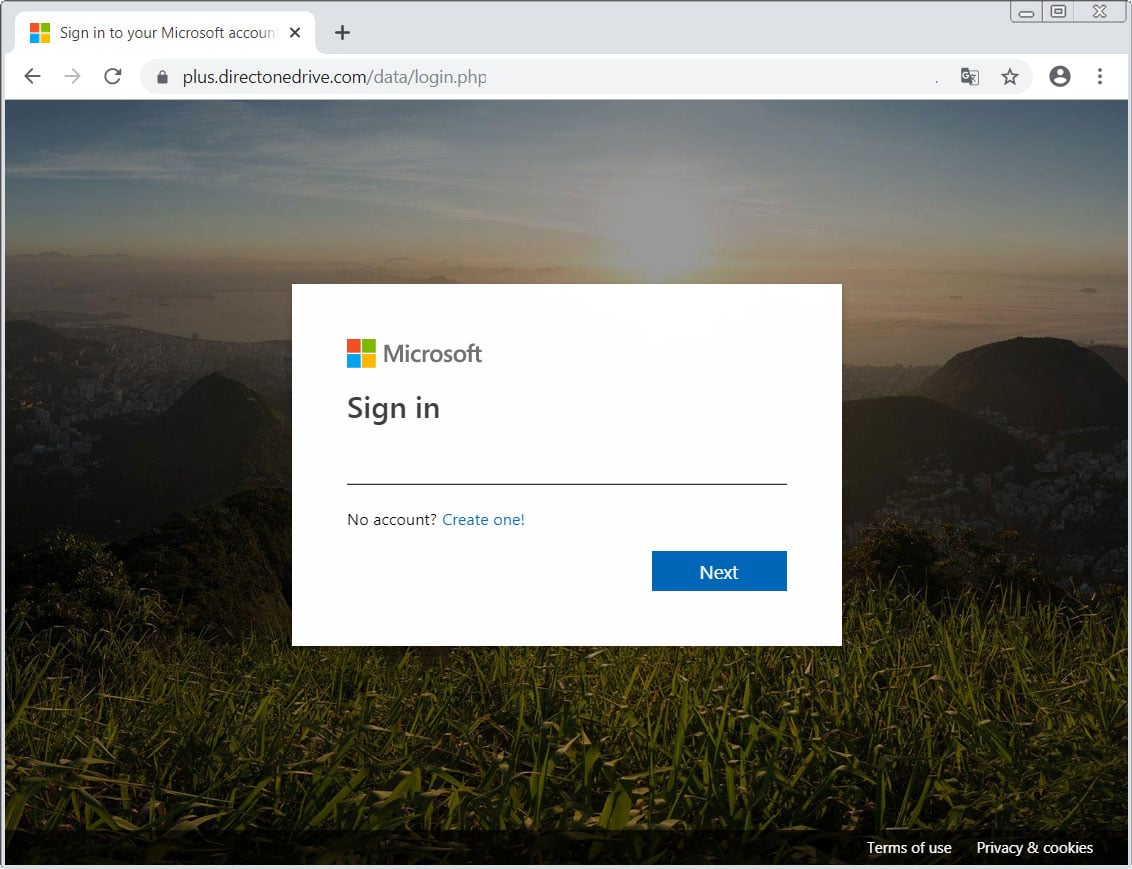
If a user enters their login credentials, it will be stolen by the attackers and used for other attacks. These attacks could include targeted phishing scams, credential stuffing attacks, or even data theft.
As always, when receiving strange emails that ask you to log in to perform some task, you should always be suspicious and contact your network or mail administrator.
Furthermore, users should always examine the URLs of any landing pages that contain Microsoft login forms and to remember that legitimate login forms will be on the microsoft.com, live.com, and outlook.com domains.