SquirtDanger Is Capable Of Draining Crypto-Wallets, Killing Process, Stealing Passwords From Web Browser And Taking Screenshots.
In a new research report published on April 17, Palo Alto’s Unit 42 researchers revealed that there is a freshly identified strain of malware that takes screenshots, download files, steals passwords as well as drains cryptocurrency wallets.
The botnet malware, dubbed as SquirtDanger belongs to the Swiss Army Knife Malware family. The malware is distributed through illegal software downloads that are known as Warez. So far, nearly 1,277 samples of this new malware linked to 119 unique C&C servers have been identified by researchers across multiple campaigns. Prominent targets are located in France, Netherlands, French Guinea and Russia.
Additional capabilities of SquirtDanger include deleting malware, removing browser cookies, sending files, listing processes, uploading/deleting/executing files, killing processes and obtaining directory information.
According to Palo Alto’s blog post, when SquirtDanger infects a system, it persists through a ‘scheduled task,’ which automatically runs after every minute to obtain as much information as possible. SquirtDanger used ‘raw TCP connections’ for initiating network communications to a remote C&C server, claimed researchers.
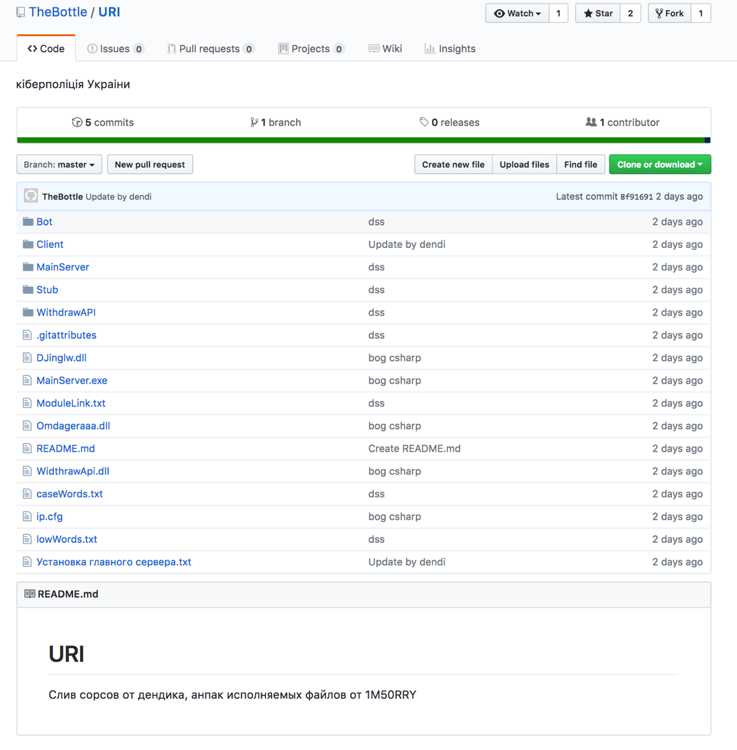
It must be noted that Swiss Army Knife malware family was designed by a seasoned Russian cybercriminal who uses the alias TheBottle and has been quite active on shady underground marketplaces on the web. The malware has been named SquirtDanger because of a dynamic-link library/DLL file written in C Sharp. This file comprises of various layers of embedded code.
As per the findings of researchers at Palo Alto Networks, individuals and organizations across the globe have become targets of SquirtDanger. This includes an African telecom firm, Turkish university and an internet service provider based in Singapore. Researchers claim that there isn’t any specific industry that’s been attacked with SquirtDanger because the malware is up for sale so targets are diverse.
SquirtDanger can extract cryptocurrency wallets’ contents by using switch tactics quite like the ones adopted by ComboJack malware. However, Grunzweig states that SquirtDanger is not the only one out there in the wild and there might be much more malware belonging to the same family.
To read the original article:
https://www.hackread.com/squirtdanger-malware-steals-passwords-take-screenshots/