A lesser known hacker group believed to be working on behalf of the North Korean government has been expanding the scope and sophistication of its campaigns, according to a report published on Tuesday by FireEye.
The threat actor is tracked by FireEye as APT37 and Reaper, and by other security firms as Group123 (Cisco) and ScarCruft (Kaspersky). APT37 has been active since at least 2012, but it has not been analyzed as much as the North Korea-linked Lazarus group, which is said to be responsible for high-profile attacks targeting Sony and financial organizations worldwide.
Cisco published a report in January detailing some of the campaigns launched by the threat actor in 2017, but APT37 only started making headlines in early February when researchers revealed that it had been using a zero-day vulnerability in Adobe Flash Player to deliver malware to South Korean users.
APT37, whose goals appear to align with North Korea’s military, political and economic interests, has mainly focused on targeting public and private entities in South Korea, including government, defense, military and media organizations.
However, according to FireEye, the group expanded its attacks to Japan, Vietnam and even the Middle East last year. The list of targets includes organizations in the chemicals, manufacturing, electronics, aerospace, healthcare, and automotive sectors.
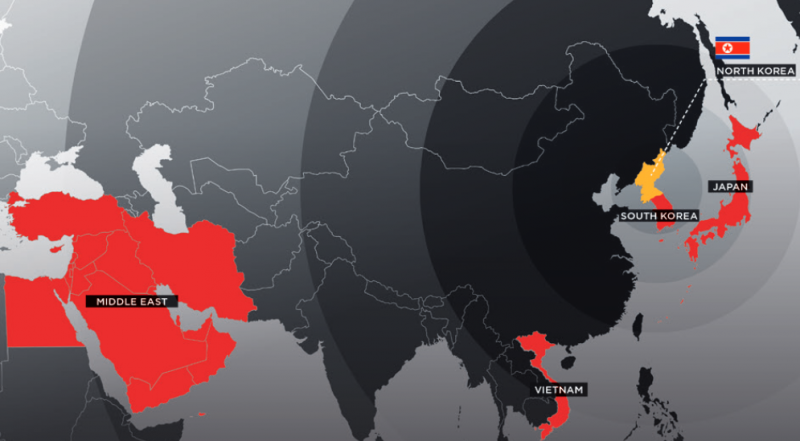
One of the targets in the Middle East was a telecommunications services provider that had entered an agreement with the North Korean government. The deal fell through, which is when APT37 started hacking the Middle Eastern company, likely in an effort to collect information, FireEye said.
APT37 has exploited several Flash Player and Hangul Word Processor vulnerabilities to deliver various types of malware, including the RUHAPPY wiper, the CORALDECK exfiltration tool, the GELCAPSULE and HAPPYWORK downloaders, the MILKDROP and SLOWDRIFT launchers, the ZUMKONG infostealer, the audio-capturing tool SOUNDWAVE, and backdoors tracked by FireEye as DOGCALL, KARAE, POORAIM, WINERACK and SHUTTERSPEED.
This malware has been delivered using social engineering tactics, watering holes, and even torrent sites for wide-scale distribution.
FireEye is highly confident that APT37 is linked to the North Korean government based on several pieces of evidence, including the use of a North Korean IP, malware compilation timestamps consistent with a typical workday in North Korea, and objectives that align with Pyongyang’s interests.
“North Korea has repeatedly demonstrated a willingness to leverage its cyber capabilities for a variety of purposes, undeterred by notional redlines and international norms,” FireEye said in its report. “Though they have primarily tapped other tracked suspected North Korean teams to carry out the most aggressive actions, APT37 is an additional tool available to the regime, perhaps even desirable for its relative obscurity. We anticipate APT37 will be leveraged more and more in previously unfamiliar roles and regions, especially as pressure mounts on their sponsor.”
Neither Kaspersky nor Cisco have explicitly attributed the APT37 attacks to North Korea.
