Introduction
GandCrab ransomware was first reported on Friday 2018-01-26. Since then, we’ve seen it distributed by campaigns using exploit kits and HoeflerText popup windows. But today on Wednesday 2018-02-07, we’ve also seen GandCrab ransomware distributed through malicious spam (malspam). Today’s GandCrab is a file-less infection using a DLL file called by a PowerShell script initiated by a Word document macro. This particular malspam campaign uses PDF attachments to kick off the infection chain. My Online Security has already reported most of the details.
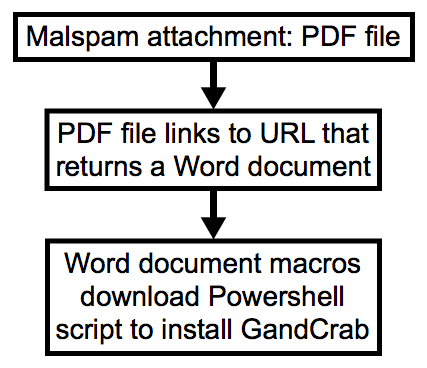
Shown above: Chain of events from today’s wave of malspam.
Background on the malspam
As early as 2018-01-30, a distinct wave of malspam contained PDF attachments designed to infected Windows computers with Dridex. These emails follow consistent patterns. But today, instead of pushing Dridex, this malspam is now pushing GandCrab ransomware.
The timeline so far is:
- 2018-01-30 through 2018-02-05: PDF attachments link to 7-Zip archives. Extracted VBS files designed to infect Windows hosts with Dridex
- 2018-02-06: PDF files link to Microsoft Word document instead of 7-Zip archives. Macro in Word doc designed to infect Windows hosts with Dridex .
- 2018-02-07: PDF files still link to Word doc, Macro now pushes GandCrab ransomware instead of Dridex
GandCrab ransomware
Until today, the GandCrab ransomware samples I’ve seen have been Windows executables using an .exe file extension. @_qaz_qaz has already posted a quick analysis on unpacking a GandCrab executable shortly after it was discovered. But today’s GandCrab is a DLL file called from a Base64 string in a PowerShell script. As other sources have already pointed out, GandCrab is notable because it calls for Dash cryptocurrency instead of Bitcoin for the ransom payment
To read the original article:
https://isc.sans.edu/forums/diary/GandCrab+Ransomware+Now+Coming+From+Malspam/23321
