A recently disclosed severe 17-year-old vulnerability in Microsoft Office that lets hackers install malware on targeted computers without user interaction is now being exploited in the wild to distribute a backdoor malware.
First spotted by researchers at security firm Fortinet, the malware has been dubbed Cobalt because it uses a component from a powerful and legitimate penetration testing tool, called Cobalt Strike.
Cobalt Strike is a form of software developed for Red Team Operations and Adversary Simulations for accessing covert channels of a system.
The vulnerability (CVE-2017-11882) that Cobalt malware utilizes to deliver the backdoor is a memory-corruption issue that allows unauthenticated, remote attackers to execute malicious code on the targeted system when opened a malicious file and potentially take full control over it.
This vulnerability impacts all versions of Microsoft Office and Windows operating system, though Microsoft has already released a patch update to address the issue. You can read more details and impact of the vulnerability in our previous article.
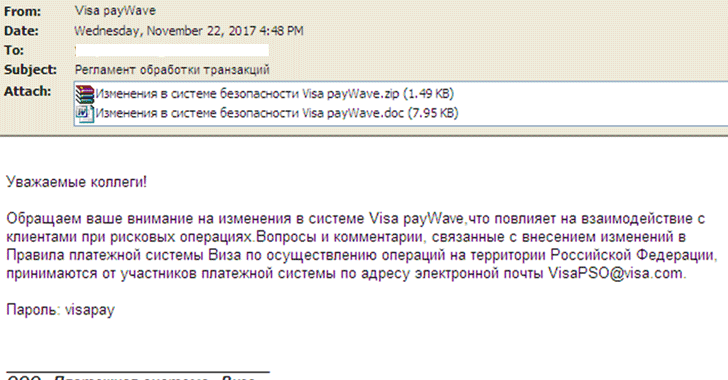
Since cybercriminals are quite quick in taking advantage of newly disclosed vulnerabilities, the threat actors started delivering Cobalt malware using the CVE-2017-11882 exploit via spam just a few days after its disclosure.
According to Fortinet researchers, the Cobalt malware is delivered through spam emails, which disguised as a notification from Visa regarding rule changes in Russia, with an attachment that includes a malicious RTF document, as shown.
To read the original article:
https://thehackernews.com/2017/11/cobalt-strike-malware.html
