A new MBR bootlocker called DiskWriter, or UselessDisk, has been discovered that overwrites the MBR of a victim’s computer and then displays a ransom screen on reboot instead of booting into Windows. This ransom note asks for $300 in bitcoins in order to gain access to Windows again.
First discovered by security researcher Dmitry Melikov, this infection is being distributed under the DiskWriter.exe or UselessDisk.exe filenames. The sample also includes a PDB string of E:\Debug\UselessDisk.pdb, which indicates that the developer named this infection UselessDisk.
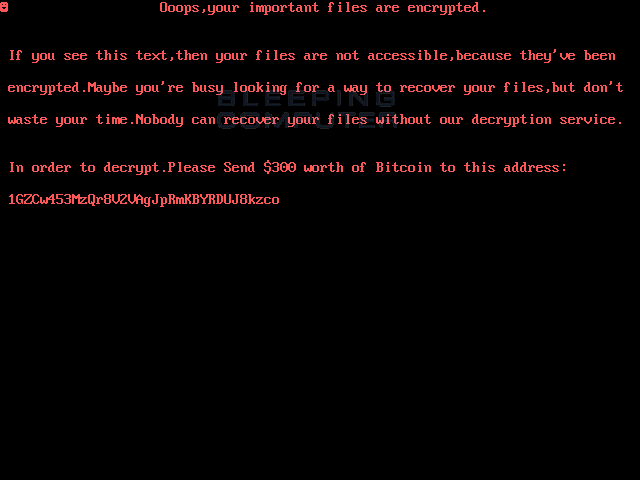
When this infection is executed it will replace the MBR with its own bootloader and then reboots the computer using the « shutdown -r -t 0 » command. Once the computer is rebooted, it will display the ransom screen shown above.
This screen contains instructions to send $300 USD in bitcoins to the static bitcoin address of 1GZCw453MzQr8V2VAgJpRmKBYRDUJ8kzco. At this time, no payments have been made to this address.
When I tested this sample, I was not able to remove the bootlocker by simply fixing the Master Boot Record (MBR), and after fixing the MBR, the machine was displaying an invalid partition table error. Therefore, it’s likely the MFT or partition table is purposely corrupted or encrypted.

Furthermore, as all victims receive the same bitcoin address, there is no contact information, the internal project name is UselessDisk, and there is no way for the developers to know who paid a ransom, I feel that this infection was designed to be destructive and not to actually be a ransomware. As more information becomes available, I will update this article.
to read the original article: