For the past two days, secure email provider ProtonMail has been fighting off DDoS attacks that have visibly affected the company’s services, causing short but frequent outages at regular intervals.
« The attacks went on for several hours, although the outages were far more brief, usually several minutes at a time with the longest outage on the order of 10 minutes, » a ProtonMail spokesperson said describing the attacks.
The email provider claims to « have traced the attack back to a group that claims to have ties to Russia, » a statement that some news outlets took at face value and ran stories misleading readers into thinking this was some kind of nation-state-planned cyber-attack.
But in reality, the DDoS attacks have no ties to Russia, weren’t even planned to in the first place, and the group behind the attacks denounced being Russian, to begin with.
Small hacker group behind ProtonMail DDoS attacks
Responsible for the attacks is a hacker group named Apophis Squad. In a private conversation with Bleeping Computer today, one of the group’s members detailed yesterday’s chain of events.
The Apophis member says they targeted ProtonMail at random while testing a beta version of a DDoS booter service the group is developing and preparing to launch.
The group didn’t cite any reason outside « testing » for the initial and uncalled for attack on ProtonMail, which they later revealed to have been a 200 Gbps SSDP flood, according to one of their tweets.
« After we sent the first attack, we downed it for 60 seconds, » an Apophis Squad member told us. He said the group didn’t intend to harass ProtonMail all day yesterday or today but decided to do so after ProtonMail’s CTO, Bart Butler, responded to one of their tweets calling the group « clowns. »
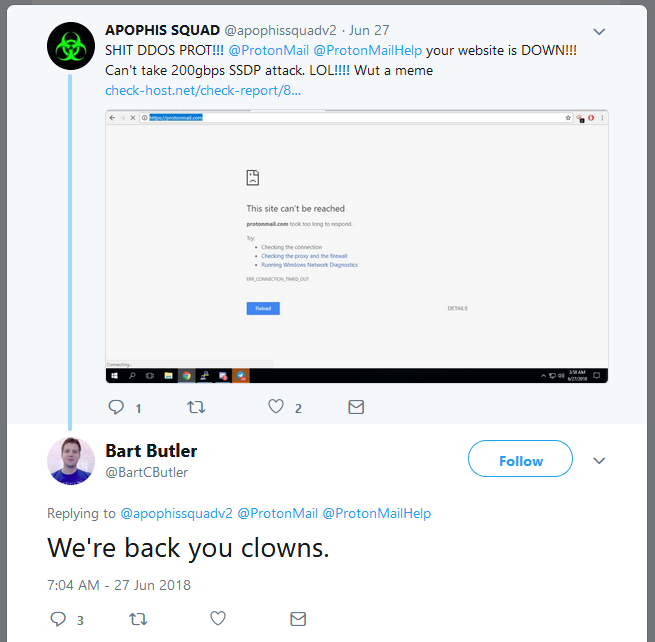
This was a questionable response on the part of the ProtonMail CTO, as it set the hackers against his company even more.
« So we then downed them for a few hours, » the Apophis Squad member said. Subsequent attacks included a whopping TCP-SYN flood estimated at 500 Gbps, as claimed by the group…
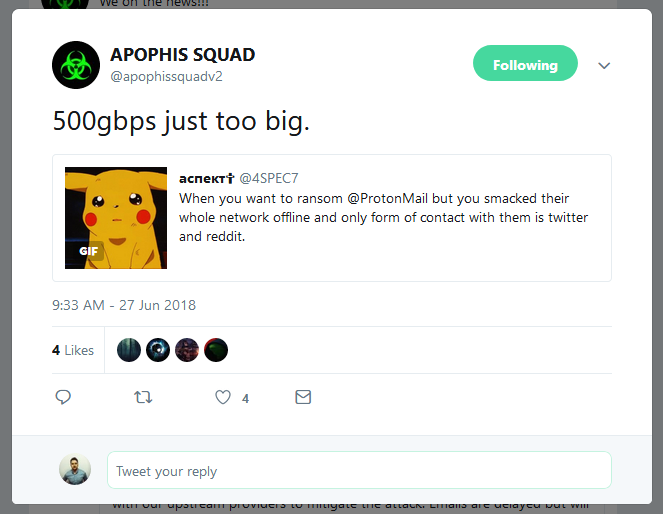
…and NTP and CLDAP floods, as observed by a security researcher at NASK and confirmed by another Apophis Squad member.[…]
To read the original article: