Dubbed RottenSys, the malware that disguised as a ‘System Wi-Fi service’ app came pre-installed on millions of brand new smartphones manufactured by Honor, Huawei, Xiaomi, OPPO, Vivo, Samsung and GIONEE—added somewhere along the supply chain.
All these affected devices were shipped through Tian Pai, a Hangzhou-based mobile phone distributor, but researchers are not sure if the company has direct involvement in this campaign.
« According to our findings, the RottenSys malware began propagating in September 2016. By March 12, 2018, 4,964,460 devices were infected by RottenSys, » researchers said.
To evade detection, the fake System Wi-Fi service app comes initially with no malicious component and doesn’t immediately start any malicious activity.
Instead, RottenSys has been designed to communicate with its command-and-control servers to get the list of required components, which contain the actual malicious code.
RottenSys then downloads and installs each of them accordingly, using the « DOWNLOAD_WITHOUT_NOTIFICATION » permission that does not require any user interaction.
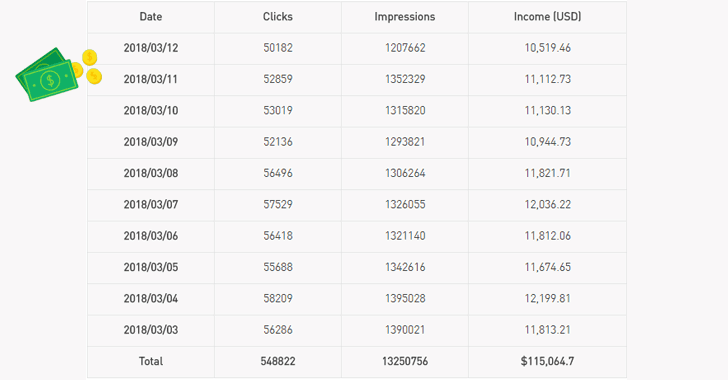
Hackers Earned $115,000 in Just Last 10 Days
At this moment, the massive malware campaign pushes an adware component to all infected devices that aggressively displays advertisements on the device’s home screen, as pop-up windows or full-screen ads to generate fraudulent ad-revenues.
« RottenSys is an extremely aggressive ad network. In the past 10 days alone, it popped aggressive ads 13,250,756 times (called impressions in the ad industry), and 548,822 of which were translated into ad clicks, » researchers said.
According to the CheckPoint researchers, the malware has made its authors more than $115,000 in the last 10 days alone, but the attackers are up to « something far more damaging than simply displaying uninvited advertisements. »
The investigation also disclosed some evidence that the RottenSys attackers have already started turning millions of those infected devices into a massive botnet network.
Some infected devices have been found installing a new RottenSys component that gives attackers more extensive abilities, including silently installing additional apps and UI automation.
« Interestingly, a part of the controlling mechanism of the botnet is implemented in Lua scripts. Without intervention, the attackers could re-use their existing malware distribution channel and soon grasp control over millions of devices, » researchers noted.
This is not the first time when CheckPoint researchers found top-notch brands affected with the supply chain attack.
Last year, the firm found smartphone belonging to Samsung, LG, Xiaomi, Asus, Nexus, Oppo, and Lenovo, infected with two pieces of pre-installed malware (Loki Trojan and SLocker mobile ransomware) designed to spy on users.