Netgear recently issued 50 patches for its routers, switches, NAS devices, and wireless access points to resolve vulnerabilities ranging from remote code execution bugs to authentication bypass flaws. Twenty of the patches address “high” vulnerability issues with the remaining 30 scored as “medium” security risks. Netgear posted advisories for the […]
Tunisian School of Internet Governance 2017
Call for applications to the first Tunisian School of Internet Governance (TSIG) 16 October 2017 SESAME University, Ariana Tunisia The deadline for submission is 12 October 2017 at 23:59 UTC Background In today’s fast-paced world, Internet Governance (IG) discussions are playing a significant role in shaping the world’s Digital future at the […]
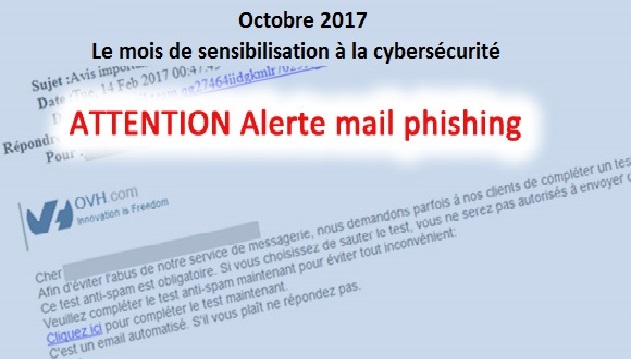
Attention au phishing ciblant les clients d’OVH
La semaine dernière une panne chez OVH a causé des perturbations chez plusieurs clients propriétaires de domaine .tn. Aujourd’hui, des personnes malveillantes profitent de ce type d’incidents pour lancer des tentatives de vol d’argent en utilisant l’attaque de phishing. Qu’est ce qu’un phishing? Il faut faire attention!!! Des clients d’OVH ont […]
Dossier Ransomware: Wannacry a fait le Buzz, mais Locky fait les dégâts.
Les ransomwares sont la menace la plus importante pour les données des entreprises et des simples utilisateurs. Dans ce dossier nous allons parler du cas de Locky qui est en train de se propager massivement et de causer beaucoup de dégâts. Notre dossier va traiter les sections suivantes: Locky est […]
According to Kaspersky Lab, sixty percent of institutions in Saudi Arabia have experienced malware-based attacks over the past 12 months.
Malware continues to be one of the most dangerous threats for organizations worldwide, and data recently disclosed by security firms. According to Kaspersky Lab, Saudi Arabia is under a constant malware-based attack, the experts reported that sixty percent of institutions in the country were hit by malicious code attacks and malware […]
Lancement officiel de NGSign l’application de signature électronique.
Toute l’équipe NG Technologies est fière de vous annoncer le lancement officiel de NGSign App. La première solution de signature électronique complète et universelle en Tunisie est désormais accessible au grand public. Dans le cadre de ce lancement NGSign offre un essai gratuit aux nouveaux inscrits. Grâce à NGSign App […]
Multiple Vulnerabilities in PHP Could Allow for Arbitrary Code Execution
Multiple vulnerabilities have been discovered in PHP, the most severe of which could allow an attacker to execute arbitrary code. PHP is a programming language originally designed for use in web-based applications with HTML content. PHP supports a wide variety of platforms and is used by numerous web-based software applications. […]
Proof-of-concept iOS exploit released by Google’s Project Zero
A security researcher for Google’s Project Zero team has released a proof-of-concept iOS exploit that takes advantage of another Broadcom Wi-Fi issue. The vulnerability abused by Gal Beniamini, a security researcher for Google Project Zero based in Israel, was found in the same Broadcom BCM4355C0 Wi-Fi chips affected by the Broadpwn […]
Data Selfie: Révèler tout ce que Facebook sait de vous
Cet outil risque de changer votre comportement et votre relation avec Facebook et les autres médias sociaux. Nous voulons vous rendre vos données Facebook. Data Selfie est une extension du navigateur Google Chrome qui vous suit pendant que vous êtes sur Facebook pour vous montrer vos propres traces de données […]
Kazakhstan Banks hit by massive DDoS attack
According to local media, several banks in the country have faced a massive DDoS(Distributed Denial of Service) attacks over the past few days. The attack traffic came from several countries at the same time. As a result, bank websites were unavailable for a certain time. One of the affected bank […]