According to the findings of Felix Krause, a mobile app developer and founder of Fastlane, there is a flaw in iOS that is potentially dangerous for the security of users’ passwords. In his blog post, Krause explained that cybercriminals could use pop-up dialog boxes to carry out phishing attacks so that an unsuspecting user could be […]
Unpatched SQLi vulnerability in SmartVista e-commerce suite
Companies using SmartVista, the popular e-commerce/payment management product suite developed by Swiss company BPC Banking Technologies, are urged to put limit access to its management interface. That’s because Rapid7 researcher Aaron Herndon found a SQL injection vulnerability in it, and BPC has shown no indication that it’s going to fix […]
SEC spoofed, malware hosted on US gov’t server in new DNS attack
Researchers have discovered a new version of the DNS Messenger attack which masquerades as the US Securities and Exchange Commission (SEC) and hosts malware on compromised government servers. On Wednesday, security researches from Cisco Talos revealed the results of an investigation into DNS Messenger, a fileless attack which uses DNS […]
DDoS attacks: Brands have plenty to lose, even if attacked only once
DDoS attacks continue to be an effective means to distract and confuse security teams while inflicting serious damage on brands. Neustar discovered that brands experienced a 27 percent increase in the number of breaches per DDoS attack, despite suffering similar attack levels in the same time period last year. Attackers […]
Cyber Threat Intelligence – Minority Report
Threat intelligence (TI) is at the maturity level to become a decision making tool. TI refers to evidence based information including context such as mechanisms, Indicators of Compromise (IOC), Indicators of Attribution (IOA), implications and actionable advice about existing or emerging hazards to assets. TI allows the technical staff professionals […]
Réseaux sociaux : vers une meilleure protection de la vie privée ?
A l’heure où les internautes du monde entier jugent indispensable de pouvoir partager en ligne leur intimité avec tous leurs amis, réels et virtuels, et où la société Facebook a annonce qu’elle a adépassé les 2 milliards d’utilisateurs en juin 2017. Twitter aussi fait désormais partie intégrante des principaux réseaux sociaux. Il […]
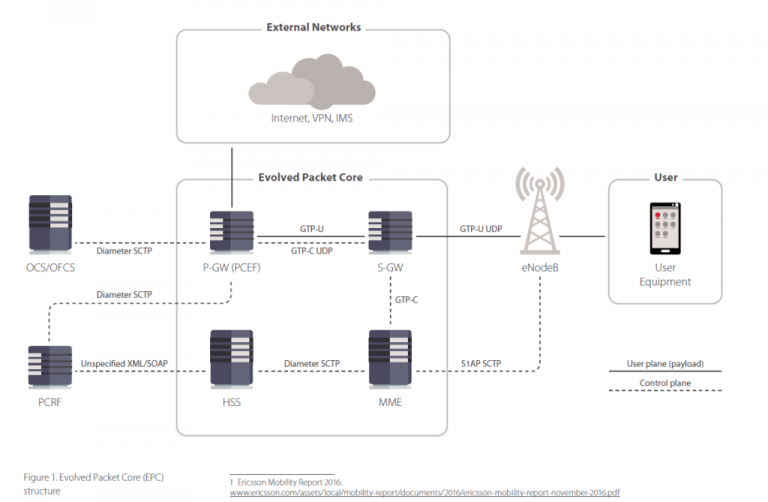
4G/5G Wireless Networks as Vulnerable as WiFi and putting SmartCities at Risk
Researchers from security firm Positive Technologies warns of 4G/5G Wireless Networks as vulnerable as WiFi and putting smart-cities at risk The Internet of Things (IoT) presents many new opportunities and some different challenges. The vast number of devices makes it very expensive to connect everything with traditional network cabling and in many […]
ASD revealed hacker stole 30GB of sensitive data on Australia’s military capabilities
The Australia’s foreign intelligence agency, the Australian Signals Directorate (ASD), admitted a hacker has stolen over 30 GB of military documents. Stolen data includes details on fighter jets, military aircraft, and naval ships. The hacker stole the huge trove of confidential data on military capabilities at an unnamed Department of […]
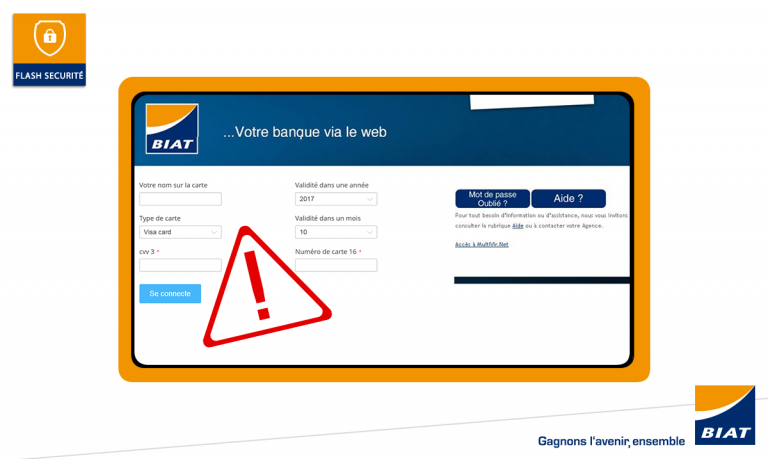
La BIAT victime d’une tentative d’attaque par Phishing
La BIAT attire l’attention de ses clients sur un site web fictif ( https://biatnet.yolasite.com/ ) qui usurpe l’identité visuelle de son vrai site de banque en ligne BIATNET . La BIAT tient à préciser qu’elle n’est pas associée à ce site et vous invite à ne pas y accéder. Ce site fictif […]