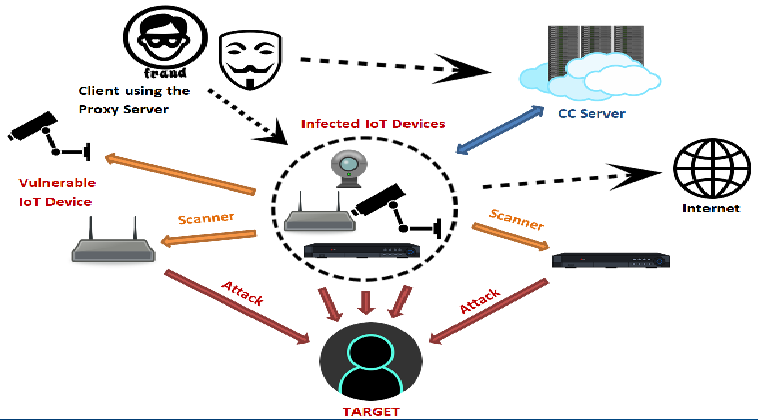
In preparation for our talk entitled “IoT: Battle of Bots” at the RootedCon Security conference that will be held in Madrid, Spain this March 2018, the FortiGuard Labs team encountered yet another new Mirai variant. Since the release of the source code of the Mirai botnet, FortiGuard Labs has seen a number […]
Here We Go Again: Intel Releases Updated Spectre Patches
Here We Go Again: Intel Releases Updated Spectre Patches In a press release published on Tuesday, Intel announced it resumed the deployment of CPU microcode firmware updates. These updates are meant to mitigate the Spectre Variant 2 vulnerability —CVE-2017-5715. The Meltdown (CVE-2017-5754) and Spectre variant 1 (CVE-2017-5753) vulnerabilities —which became […]
Microsoft Fixes Windows 10 Vulnerability But Doesn’t
A Google security engineer says Microsoft has failed to properly patch a security flaw affecting Windows 10 and Windows Server 2016 distributions. The flaw affects the Windows Storage Services, a core OS service that manages file transfers and storage operations. More precisely, the vulnerability affects the « SvcMoveFileInheritSecurity » function that Windows […]
The Annabelle Ransomware Is a Horrific Mess
While most ransomware is created to actually generate revenue, some developers create them to show off their « skills ». Such is the case with a new ransomware based off of the horror movie franchise Annabelle. Discovered by security researcher Bart, Annabelle Ransomware includes everything but the kitchen sink when it comes to screwing up […]
Google Researcher Finds Critical Flaws in uTorrent Apps
Google researcher Tavis Ormandy discovered several critical vulnerabilities in the classic and web-based versions of BitTorrent’s uTorrent application. Patches have been released, but it appears that not all flaws have been fixed properly. Ormandy found that the uTorrent Classic and the uTorrent Web apps create an HTTP RPC server on […]
Hacker Detection Firm Vectra Networks Raises $36 Million
Vectra Networks, a cybersecurity firm that helps customers detect “in-progress” cyberattacks, today announced that it has closed a $36 million Series D funding round, bringing the total amount raised to date by the company to $123 million. The company said the investment would be used to expand sales and marketing, […]
AndroRAT: New Android malware strain can hijack older phones
An Android trojan that started out as an open-source project has been updated to allow hackers to gain access to virtually all data on infected devices. Silent installation, shell command execution and the collection of credentials, Wi-Fi passwords and screenshots are just some of the capabilities of AndroRAT, which exploits CVE-2015-1805, […]
Les scripts de cryptojacking pourraient profiter d’une nouvelle fonctionnalité de Word
Le cryptojacking consiste à utiliser secrètement les ressources de votre dispositif pour miner de la cryptomonnaie. L’idée du cryptojacking est née en mi-septembre lorsque CoinHive a proposé un script pour le minage de cryptomonnaies (monero en l’occurrence). Parmi les sites Web qui l’ont adopté, figure The Pirate Bay, le site […]
Le programme d’installation de Skype vulnérable aux attaques par injection DLL ?
Selon plusieurs sources, le programme d’installation de Skype serait vulnérable aux attaques par injection DLL. Même la toute dernière version 8 serait concernée. Le programme d’installation de Skype se comporte-t-il comme un cheval de Troie en permettant des attaques par injection DLL ? C’est en tout cas ce que semble […]
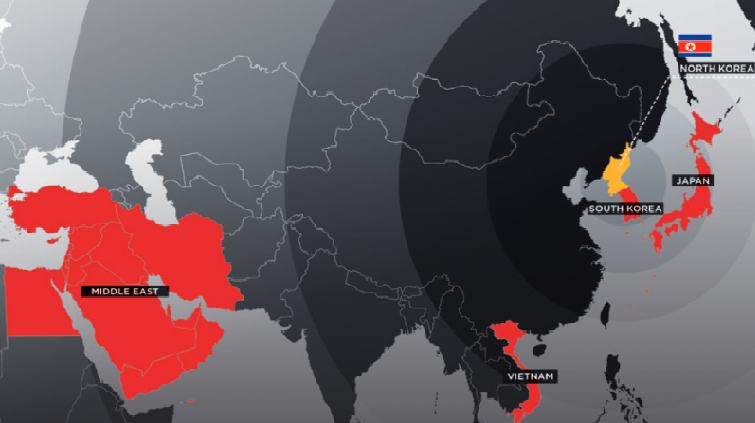
North Korean Hacking Group APT37 Expands Targets
A lesser known hacker group believed to be working on behalf of the North Korean government has been expanding the scope and sophistication of its campaigns, according to a report published on Tuesday by FireEye. The threat actor is tracked by FireEye as APT37 and Reaper, and by other security […]