A brazen phishing campaign took Iceland by surprise the last weekend, sending out malicious emails to thousands of individuals, in an attempt to fool them into installing a powerful remote access tool.
Even if the number of potential victims may seem low, local police say this is the largest cyber attack to hit the country. One must take into consideration that the population of Iceland is around 350,000, with about half of the citizens living in the capital city Reykjavik. By comparison, in 2016 London lived over 8.5 million people.
Attacker uses the homograph trick
The assault started on the evening of Saturday, October 6, with messages that impersonated the Icelandic police. The emails asked the recipients to come in for questioning and warned them that non-compliance resulted in issuing an arrest warrant.
A link leading to a spoofed version of Lögreglan – the Icelandic police, seemingly offered more information on the matter.
To make everything appear authentic, the author of the campaign resorted to the homograph trick to register a domain that looked like the original ‘logreglan.is.’
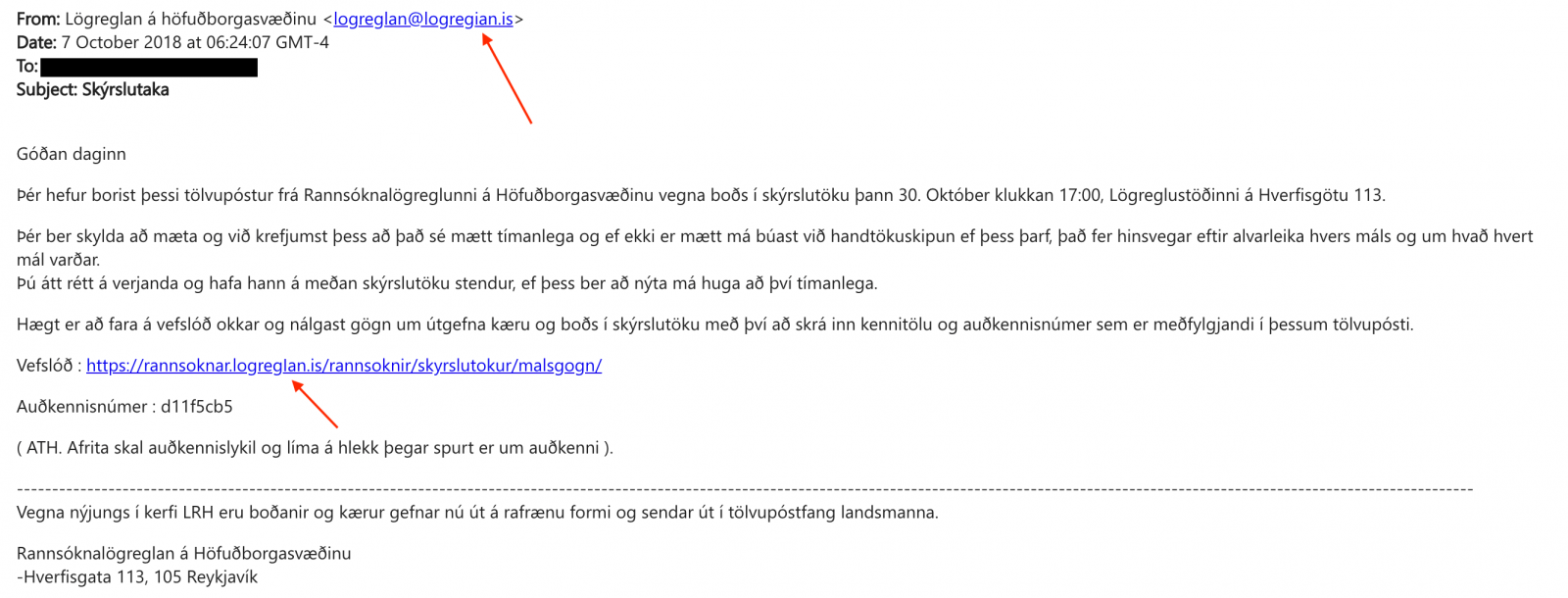
« […] the attacker registered a domain name of www.logregian.is–using a lower case ‘i’ (which on first glance, may appear like a lower case “L” or “l”), » explain researchers from Cyren working with the police during the investigation.
They add that the link in the message used « switched the lower case “i” for a capital “i” or “I”, so the “i” actually looks like a small “L”—making it indistinguishable from “logreglan” to almost any web user. »
Remcos RAT is once again used for malicious purposes
Speaking to BleepingComputer, Cyren senior threat analyst Magni Sigurdsson says that the threat is a completely new one for Iceland, referring to the complexity of the phishing scheme.
The tool used by the attacker is Remcos, a powerful tool available commercially as a legitimate solution for access to remote computers, used before for malicious purposes.
Sigurdsson told us that the version employed in the attack was 2.0.7 Pro, which provides full access to the station it runs on.
The developer of the remote access tool (RAT) is aware that his Remcos is sometimes used for malicious purposes and told BleepingComputer that for this reason he implemented a mechanism to prevent abuse.
« Apart from blocking the customer license (preventing him to use our software), we provide help into removing the software from the compromised system. This can be done very easily from us, » he said over email.
He added that when Remcos was used maliciously, the attacker relied on other tools, too. In this case it was a VBSscript that ran at startup to ensure the execution of Remcos.
Sophisticated phishing scheme
The link in the phishing messages takes the victim to a website that imitates almost to perfection the official website of the Icelandic police, and asks users to enter their social security number (SSN).
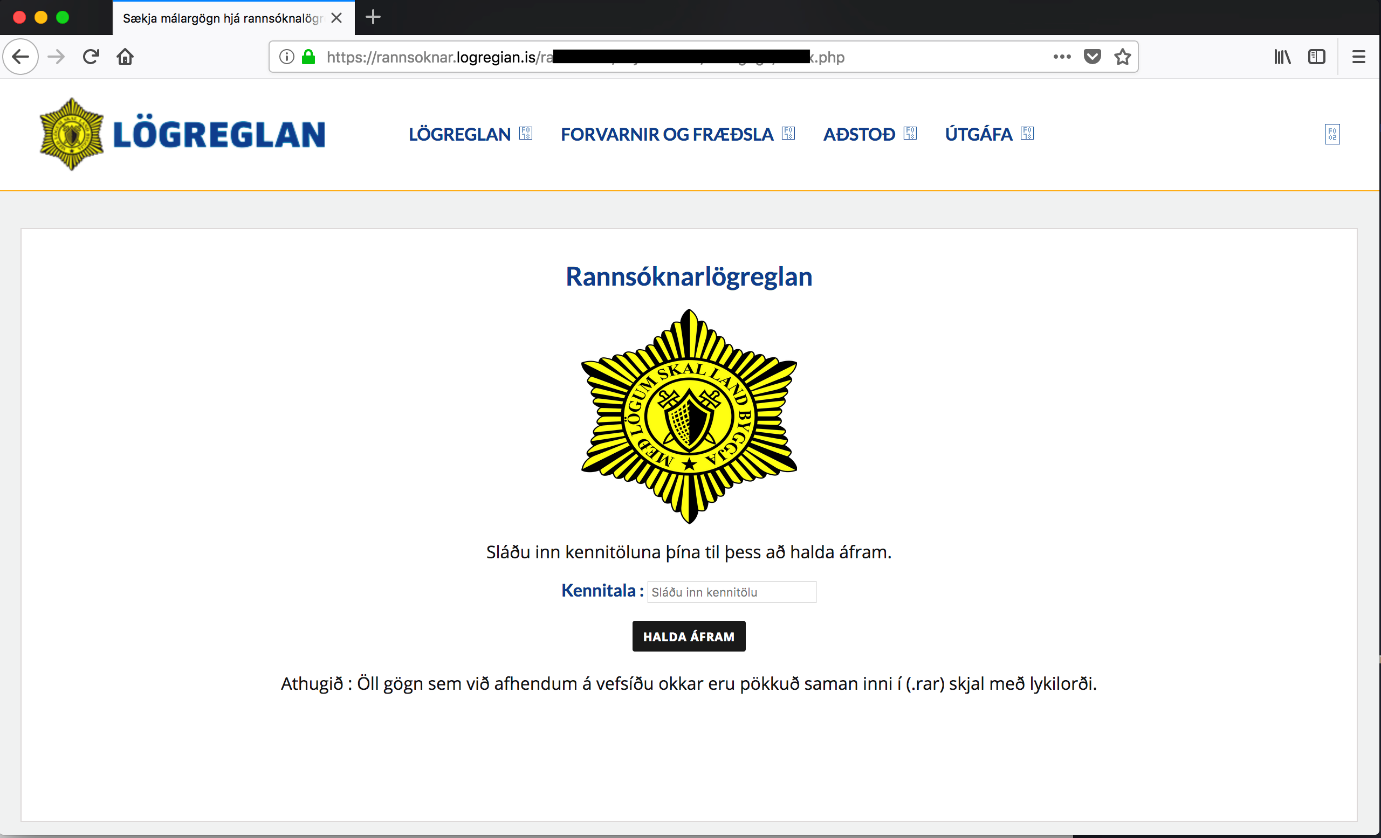
In Iceland, public consultation of names and SSNs is possible via bank-provided services, so individuals have to log into their local bank’s online account for this procedure.
If the user enters an incorrect SSN, the legitimate service displays an alert prompting for a correction. Phishing websites do not have the capability to verify the authenticity of the numbers, so they would typically accept anything info the user types in.
In the case of this campaign, however, the attacker was able somehow to check the validity of the numbers, adding to the deception. One theory is that they’re using a database that has been leaked in the past.
The trap is difficult to avoid
The attacker set up a complex phishing scheme that is difficult to detect by the average user.
The fake Icelandic police website asks the victims to enter an authentication code they received in the phishing email, to get access to more details about the police case against them.
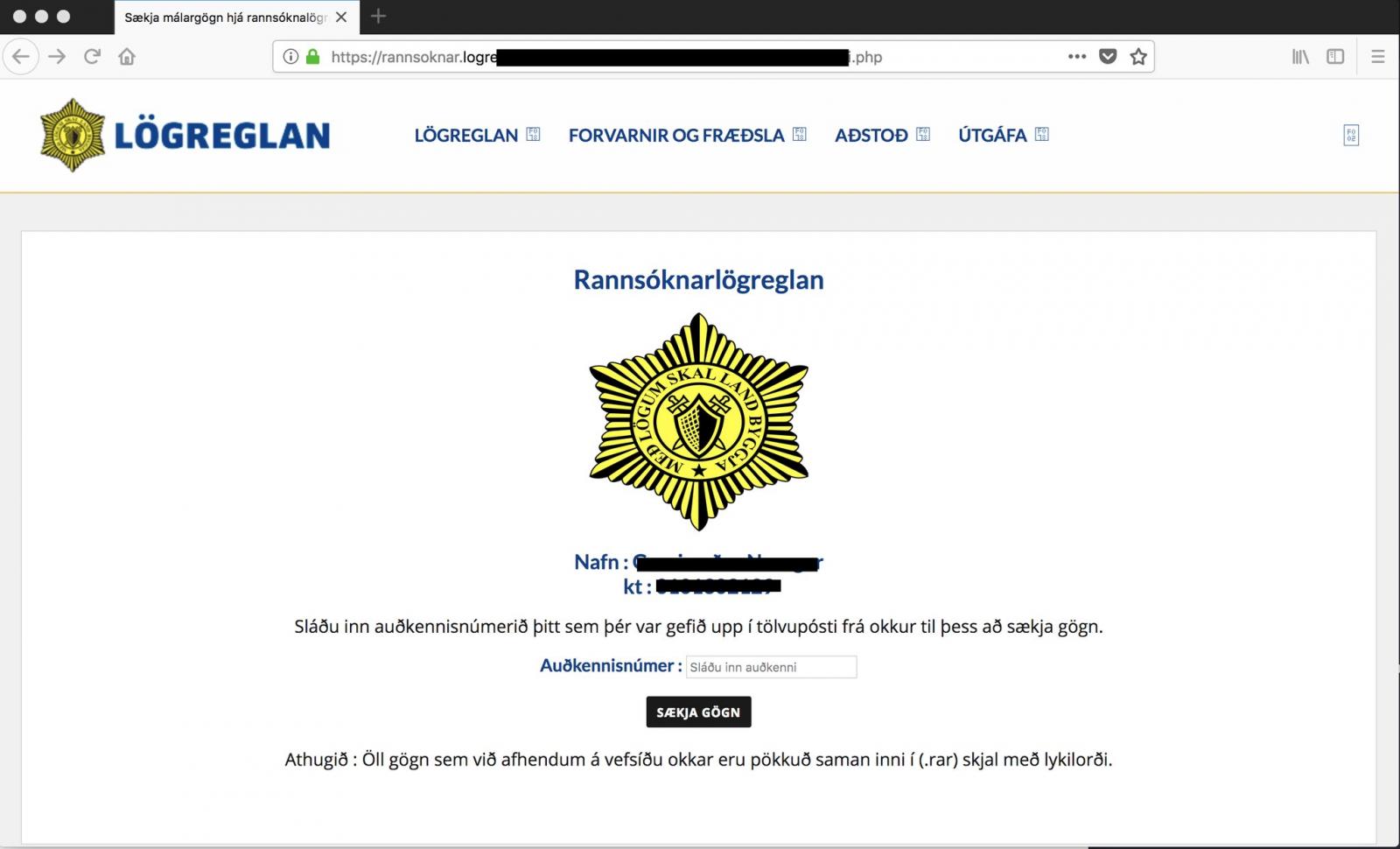
In the next step, the victim receives the alleged documents in a password-protected archive, with the key provided on the webpage, which in reality is the packed RAT designed to steal information and grant the attacker remote access to the victim computer.
Campaign tailored for Icelanders
« The extracted .rar file is a .scr file (Windows Screensaver) disguised as a word document with a long name, so the file extension is hidden. The file name is ‘Boðun í skýrslutöku LRH 30 Óktóber.scr’ which translates roughly to ‘Called in for questioning by the police on October 30th’, » Cyren notes.
The analysis of the RAT shows that the command and control (C2) servers set up to receive stolen data are in Germany and Holland.
The attacker was using Remcos to steal banking info, as it checks if the victim has access to the largest banks in Iceland, the researchers found.
The attacker remains unknown at this moment, but the police believe that the campaign is the work of someone familiar with the Icelandic administrative system. The text in the email and on the fake website support this theory.
The defensive reaction against the campaign was swift, the domain to the landing page being taken down the day after the attack was detected.
Thousands of malicious emails were sent during the attack, but the police did not release any information about the number of victims.
Those fooled by the phishing scheme had to change all their passwords, researchers say, and to format their computers.
UPDATE [October 12, 11:10am EST] We learned that the phishing attack relied only on Remcos remote access tool to steal information, target banks in Iceland, and to provide the attacker remote access to the infected computers. The article and its headline have been updated to reflect accurate information. We have also included commentary from Remcos developer.
In a tweet today, the security researcher behind the MalwareHunterTeam account said that the attacker used Remcos 2.0.7, confirmed by security researcher James who analyzed the attack tool, and later to us by Cyren.
To read the original article https://www.bleepingcomputer.com/news/security/largest-cyber-attack-against-iceland-driven-by-complex-phishing-scheme/
