GandCrab version 3 was released earlier this week with a few noticeable changes. The most noticeable change is the addition of a desktop background.
Unfortunately, at this time GandCrab 3 cannot be decrypted for free. For those who wish to discuss GandCrab or receive support, you can post in our dedicated GandCrab Help & Support topic.
Distributed through exploit kits and malspam
Marcelo Rivero, a Malware Intel Analyst from Malwarebytes, discovered GrandCrab v3 this past monday and Jérôme Segura, another Malwarebytes Intel Analyst, this variant was being distributed via the Magnitude exploit kit.
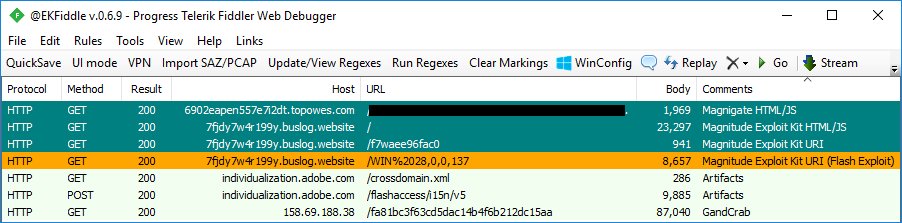
Source: EKFiddler Twitter Account
Fortinet, also spotted GandCrab v3 being distributed through malspam campaigns. These malspam emails contain subjects like « Order #65121 » and contain attachments with a VBS downloader that installs GandCrab v3.
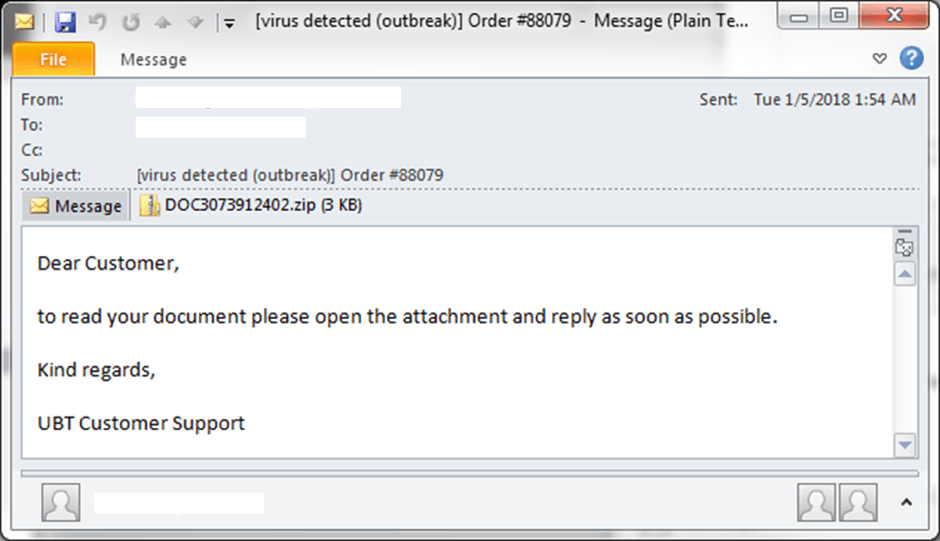
Source: Fortinet
Changes in GandCrab v3
The most noticeable change in this release of GandCrab is the increment of the version number to 3, new ransom note text, and the introduction of a pretty bad desktop background.
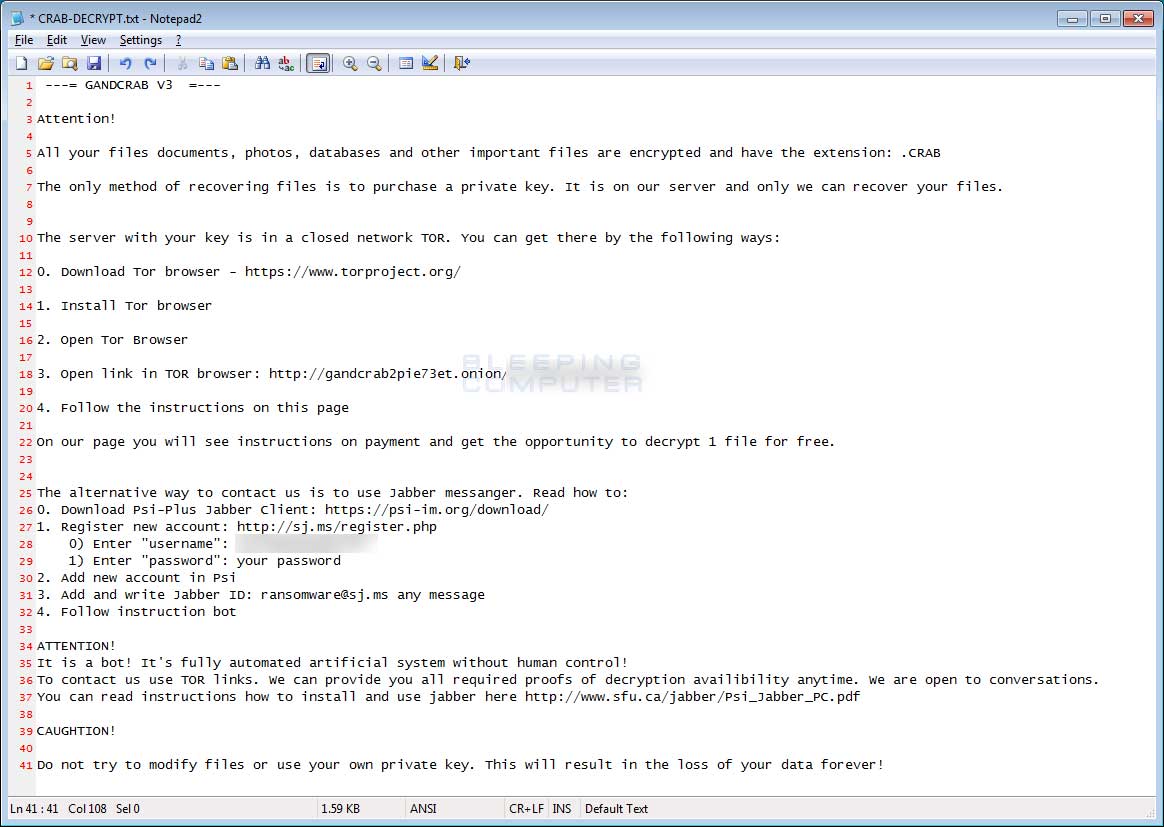
The ransom note is still named CRAB-DECRYPT.txt and encrypted files still have the .CRAB extension.
With this version, GandCrab also introduces a low resolution background that tells you to read the CRAB-DECRYPT.txt ransom note in order to learn what happened to your files. This background can be seen below.
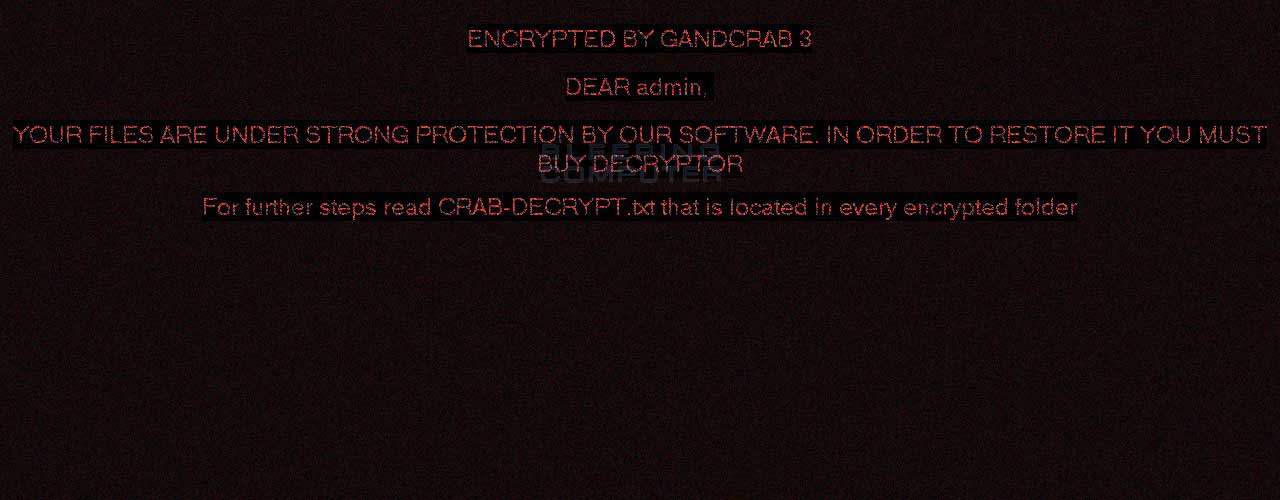
The ransom note also contains new text as can be seen below.
A RunOnce autorun key was introduced in older versions will cause GandCrab to start automatically when a user logs in. When GandCrab is installed, it will encrypt the computer, set the background, and then automatically reboot the computer. For Windows 7 users, there is a problem with this method as the autorun causes the browser to open the TOR web site and the background to display, but does not display the desktop.
Fortinet researchers feel this may be a bug in the program for those using Windows 7 that causes it to exhibit this screenlocker behavior. In some ways, this behavior could actually benefit the ransomware developers as it may cause further panic and more ransom payments.
Finally, this version introduces the domain « carder.bit » as a server that the ransomware communicates with. The GandCrab devs have a sense of humor when they name associated domains as shoutouts to security companies, websites like BC, and researchers. This one is a reference to those who perform credit card fraud.
Once again, unfortunately this version cannot be decrypted for free and if you wish to discuss GandCrab or receive support, you can post in our dedicated GandCrab Help & Support topic.
Updated 5/6/18: Updated to reflect that the RunOnce autorun was in previous versions. Thx to Ravikant Tiwari and MalwareHunterTeam.
To read the original article:https://www.bleepingcomputer.com/news/security/gandcrab-version-3-released-with-autorun-feature-and-desktop-background/
