EXECUTIVE SUMMARY Gozi ISFB is a well-known and widely distributed banking trojan, and has been in the threat landscape for the past several years. Banking trojans are a type of malware that attackers leverage in an attempt to obtain banking credentials from customers of various financial institutions. The source code […]
Hacking
Cisco Prime Collaboration Provisioning Hard-Coded Password Vulnerability
Summary A vulnerability in Cisco Prime Collaboration Provisioning (PCP) Software could allow an unauthenticated, local attacker to log in to the underlying Linux operating system. The vulnerability is due to a hard-coded account password on the system. An attacker could exploit this vulnerability by connecting to the affected system via […]
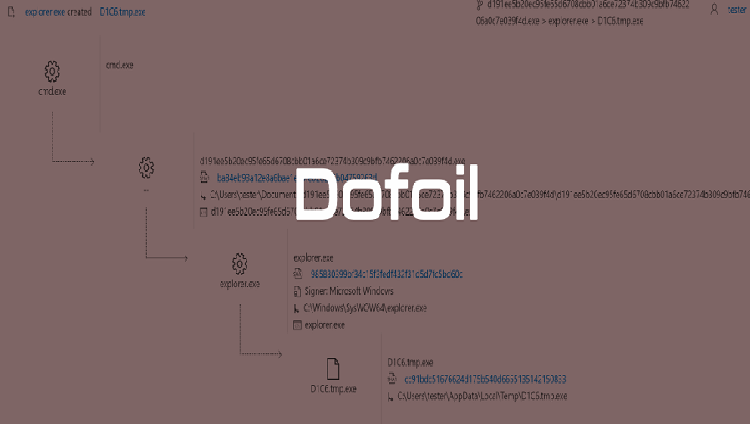
Microsoft Stops Malware Campaign That Tried to Infect 400,000 Users in 12 Hours
Microsoft revealed today that Windows Defender stopped a massive malware distribution campaign that attempted to infect over 400,000 users with a cryptocurrency miner during a 12-hour period on March 6, 2018. The Redmond-based OS maker attributes the detections to computers infected with the Dofoil malware —also known as Smoke Loader— […]
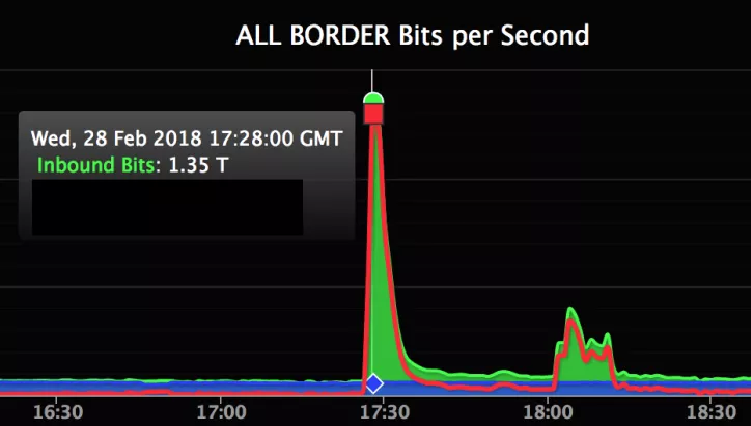
Corero Network discovered a Kill Switch for Memcached DDoS attacks
Corero network security discovers a “kill switch” for memcached DDoS attacks and also reveals memcached exploit can be used to steal or corrupt data Memcached DDoS attacks made the headlines due to the magnitude observed in recent offensives. While two PoC exploits for Memcached DDoS attacks have been released online, experts at security firm Corero […]
Technique Discovered That Can Mitigate Memcached DDoS Attacks
A mitigation mechanism is available for all victims who are under a DDoS attack carried out via Memcached servers. This mitigation technique relies on the attacked victim sending a « flush_all » command back to the attacking servers. The measure was proposed last week by Dormando, one of the Memcached server developers. […]
Group Policy Support Coming to Firefox 60
Firefox 60 will feature a new component named Policy Engine that will provide GPO support on Windows, allowing system administrators to control Firefox instances deployed across an internal network. Work on this feature has been progressing according to plan, and its launch is still scheduled for Firefox 60 — Firefox […]
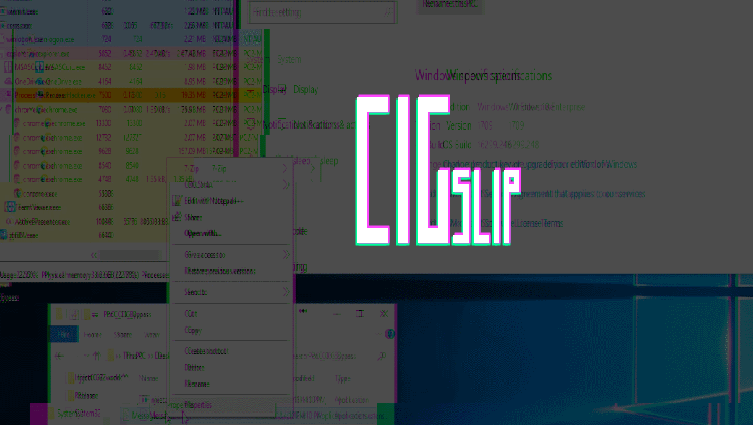
CIGslip Attack Bypasses Windows Code Integrity Guard (CIG)
Malware authors can exploit a flaw in the Windows Code Integrity Guard (CIG) security mechanism to inject malicious, unsigned code into CIG-protected applications, considered to be immune to such attacks. The technique —named CIGslip— impacts Microsoft’s Code Integrity Guard (CIG), a security system that Microsoft first introduced in 2015 with […]
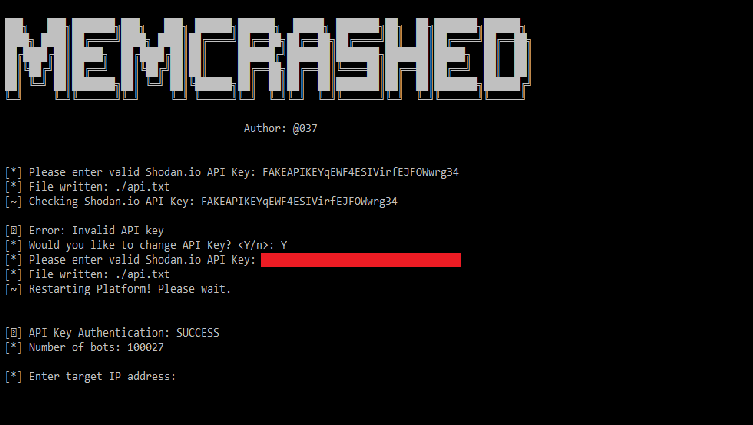
Proof-of-Concept Code for Memcached DDoS Attacks Published Online
Proof-of-concept code to run massive DDoS attacks using unsecured Memcached servers has been published online this week, along with a ready-made list of over 17,000 IP addresses belonging to vulnerable Memcached servers. Two, and not one, of such proof-of-concept (PoC) utilities, have been released, both uniques in their own way. […]
Hacker returns $17 million worth of stolen Ethereum
In July of last year, an Israeli cryptocurrency venture called Coindash was preparing for the Initial Currency Offer (ICO), but as soon as the sale began, a hacker intercepted the company’s website and stole about 43,000 worth of Ethereum. At the time, the stolen cryptocurrency equivalent to the US $ 7.4 million, but today […]
ComboJack Malware Steals Cryptocurrency by Modifying Addresses
A new cryptocurrency-stealing malware dubbed as ComboJack has been discovered by Palo Alto Networks Unit 42 and Proofpoint researchers. It has been targeting cryptocurrencies and digital wallets belonging to American and Japanese users while the malware is being distributed via email spam campaign. Fake Passport Email The malicious emails contain […]