A pair of Romanian hackers have been extradited to the U.S. after allegedly bilking unwitting victims out of more than $18 million in an elaborate voice- and SMS-phishing (i.e., vishing/smishing) scheme. Teodor Laurentiu Costea and Robert Codrut Dumitrescu were named in the 31-count federal grand jury indictment on August 16 […]
Hacking
Lenovo releases updates to fix Secure Boot flaw in servers and other issues
Lenovo has released security patches that address the High severity vulnerability CVE-2017-3775 in the Secure Boot function on some System x servers. The standard operator configurations disable signature checking, this means that some Server x BIOS/UEFI versions do not properly authenticate signed code before booting it. “Lenovo internal testing discovered some System x […]
One year later: EternalBlue exploit more popular now than during WannaCryptor outbreak
The infamous outbreak may no longer be causing mayhem worldwide but the threat that enabled it is still very much alive and posing a major threat to unpatched and unprotected systems It’s been a year since the WannaCryptor.D ransomware (aka WannaCry and WCrypt) caused one of the largest cyber-disruptions the world has […]
Phishing Attack Bypasses Two-Factor Authentication
Hacker Kevin Mitnick demonstrates a phishing attack designed to abuse multi-factor authentication and take over targets’ accounts. Businesses and consumers around the world are encouraged to adopt two-factor authentication as a means of strengthening login security. But 2FA isn’t ironclad: attackers are finding ways to circumvent the common best practice. […]
The source code of the TreasureHunter PoS Malware leaked online
Security experts at Flashpoint confirmed the availability online for the source code of the TreasureHunter PoS malware since March. The researchers found evidence that the threat has been around since at least late 2014. TreasureHunt was first discovered by researchers at the SANS Institute who noticed the malware generating mutex names to evade detection. TreasureHunt enumerates the […]
NEW FACEBOOK-SPREAD MALWARE TRIGGERS CREDENTIAL THEFT, CRYPTOMINING
A new malware campaign rapidly spreading via Facebook is infecting victims’ systems to steal their social media credentials and download cryptomining code. The malware, dubbed Nigelthorn by the Radware researchers who first discovered it, is being propagated via socially engineered links on Facebook. It has been active since at least […]
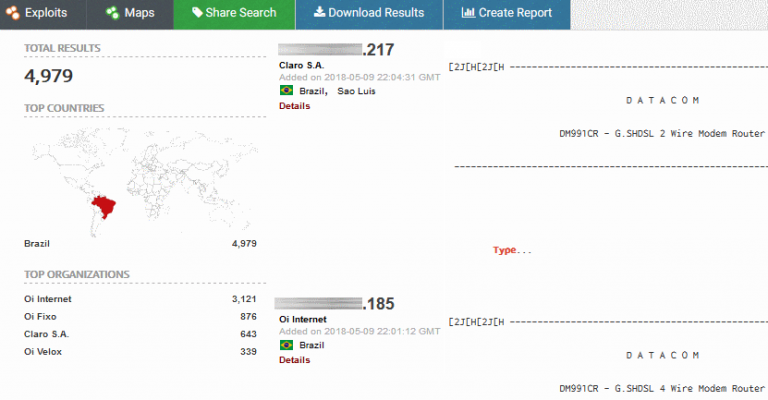
5,000 Routers With No Telnet Password. Nothing to See Here! Move Along!
A Brazilian ISP appears to have deployed routers without a Telnet password for nearly 5,000 customers, leaving the devices wide open to abuse. The devices have been discovered this week by Ankit Anubhav, Principal Researcher at NewSky Security, a cyber-security company specialized in IoT security. All exposed devices are Datacom routers the […]
5 Powerful Botnets Found Exploiting Unpatched GPON Router Flaws
Well, that did not take long. Within just 10 days of the disclosure of two critical vulnerabilities in GPON router at least 5 botnet families have been found exploiting the flaws to build an army of million devices. Security researchers from Chinese-based cybersecurity firm Qihoo 360 Netlab have spotted 5 botnet families, […]
Bitcoin Wallet App Caught Stealing Seed Keys
The team behind Electrum, a Bitcoin wallet app, has exposed a copycat product named Electrum Pro as a malicious app that steals users’ seed keys. Electrum developers made their accusations in a document published on GitHub yesterday. The document contains a step-by-step guide to decompiling a rival product named Electrum Pro that popped up online […]
Oh, Joy! Source Code of TreasureHunter PoS Malware Leaks Online
On the malware scene, there is no clearer sign of trends to come than the leaking of a malware family’s source code. Based on this assumption, we can now expect an influx of Point-of-Sale malware in the coming months after the release of the source code of the TreasureHunter PoS […]