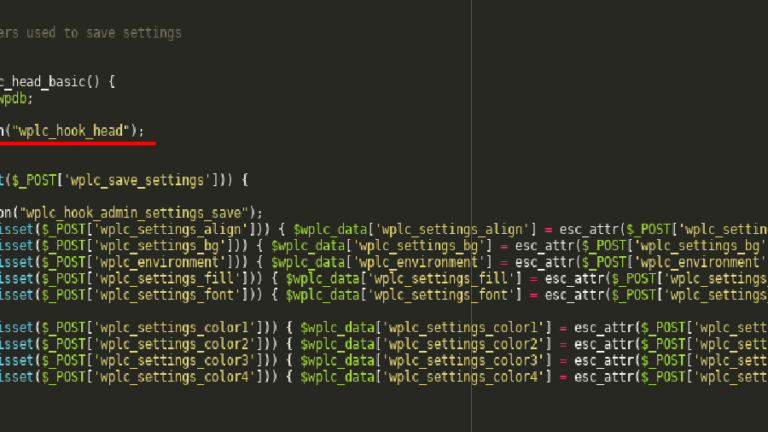
A vulnerability in the Live Chat Support plugin for WordPress could be exploited by attackers to inject malicious scripts in websites using it Researchers at Sucuri have discovered a stored/persistent cross-site scripting (XSS) vulnerability in the WP Live Chat Support plugin for WordPress. The flaw could be exploited by remote, unauthenticated attackers […]
Hacking
Threat spotlight: CrySIS, aka Dharma ransomware, causing a crisis for businesses
CrySIS, aka Dharma, is a family of ransomware that has been evolving since 2006. We have noticed that this ransomware has become increasingly active lately, increasing by a margin of 148 percent from February until April 2019. The uptick in detections may be due to CrySIS’ effective use of multiple […]
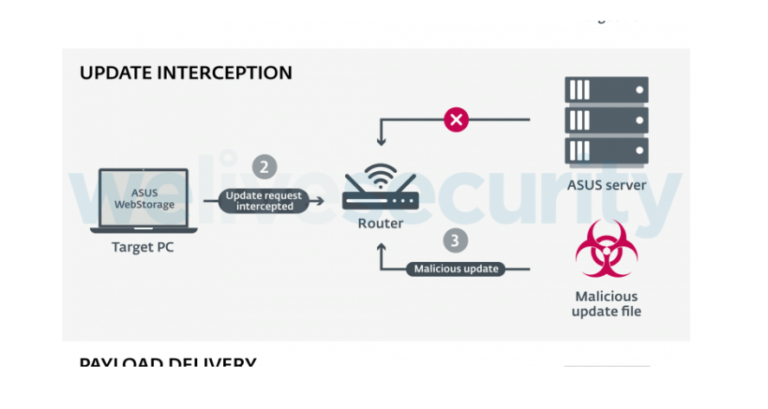
BlackTech espionage group exploited ASUS update process to deliver Plead Backdoor
The BlackTech cyber-espionage group exploited the ASUS update process for WebStorage application to deliver the Plead backdoor. The cyber espionage group tracked as BlackTech compromised the ASUS update process for WebStorage application to deliver the Plead backdoor. The BlackTech group was first observed by ESET on July 2018, when it was abusing code-signing certificates stolen from D-Link for […]
Microsoft Releases Patches For A Critical ‘Wormable Flaw’ and 78 Other Issues
It’s Patch Tuesday—the day when Microsoft releases monthly security updates for its software. Microsoft has software updates to address a total of 79 CVE-listed vulnerabilities in its Windows operating systems and other products, including a critical wormable flaw that can propagate malware from computer to computer without requiring users’ interaction. […]
Hackers Used WhatsApp 0-Day Flaw to Secretly Install Spyware On Phones
Whatsapp has recently patched a severe vulnerability that was being exploited by attackers to remotely install surveillance malware on a few « selected » smartphones by simply calling the targeted phone numbers over Whatsapp audio call. Discovered, weaponized and then sold by the Israeli company NSO Group that produces the most advanced mobile spyware […]
U.S. Charges 9 ‘SIM Swapping’ Attackers For Stealing $2.5 Million
The U.S. Department of Justice today announced charges against nine individuals, 6 of which are members of a hacking group called « The Community » and other 3 are former employees of mobile phone providers who allegedly helped them steal roughly $2.5 million worth of the cryptocurrency using a method known as « SIM Swapping. » […]
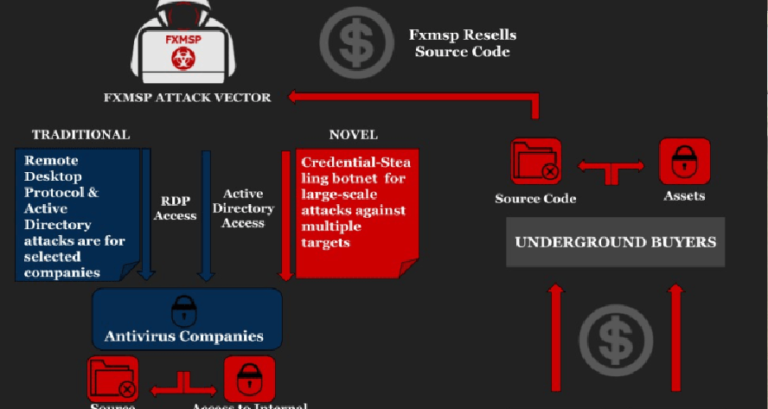
Top-Tier Russian Hacking group Fxmsp claims hack of major AntiVirus Companies
A Russian hacking group Fxmsp is offering for sale the access to the networks of at least three antivirus companies in the US and source code of their software. Fxmsp is a high-profile Russian- and English-speaking hacking group focused on breaching high-profile private corporate and government information. The group is […]
DHS and FBI published a Malware Analysis Report on North Korea-linked tool ELECTRICFISH
The U.S. Department of Homeland Security (DHS) and the FCI published a new joint report on ELECTRICFISH, a malware used by North Korea. US DHS and the Federal Bureau of Investigation (FBI) conducted a joint analysis of a traffic tunneling tool dubbed ELECTRICFISH used by North Korea-linked APT group tracked […]
High-Severity Bug Leaves Cisco TelePresence Gear Open to Attack
Cisco patches two high-severity bugs that could be exploited by remote attackers. Cisco Systems has patched two high-severity vulnerabilities that can be exploited by remote unauthenticated adversaries to launch denial of service attacks. Impacted are Cisco’s TelePresence Video Communication Server and the company’s ASA 5500-X Series Firewalls. The vulnerability with […]
Hackers Found Exploiting Oracle WebLogic RCE Flaw to Spread Ransomware
Taking advantage of newly disclosed and even patched vulnerabilities has become common among cybercriminals, which makes it one of the primary attack vectors for everyday-threats, like crypto-mining, phishing, and ransomware. As suspected, a recently-disclosed critical vulnerability in the widely used Oracle WebLogic Server has now been spotted actively being exploited […]