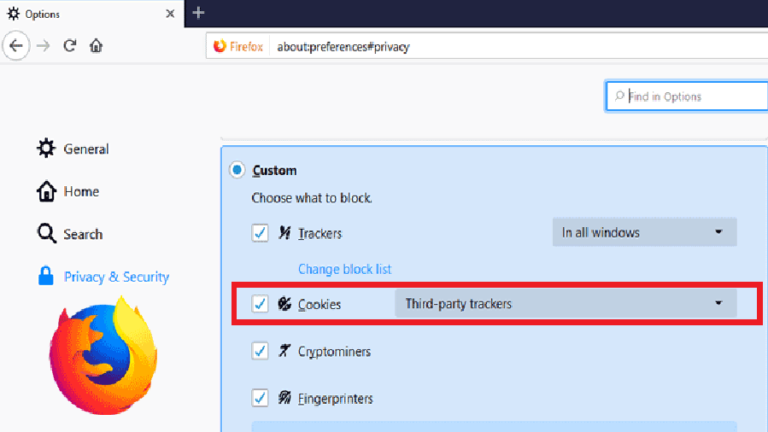
As promised, Mozilla has finally enabled « Enhanced Tracking Protection » feature on its Firefox browser by default, which from now onwards would automatically block all third-party tracking cookies that allow advertisers and websites to track you across the web. Tracking cookies, also known as third-party cookies, allows advertisers to monitor your […]
Hacking
Critical Flaws Found in Widely Used IPTV Software for Online Streaming Services
Security researchers have discovered multiple critical vulnerabilities in a popular IPTV middleware platform that is currently being used by more than a thousand regional and international online media streaming services to manage their millions of subscribers. Discovered by security researchers at CheckPoint, the vulnerabilities reside in the administrative panel of Ministra […]
Nearly 1 Million Computers Still Vulnerable to « Wormable » BlueKeep RDP Flaw
Nearly 1 million Windows systems are still unpatched and have been found vulnerable to a recently disclosed critical, wormable, remote code execution vulnerability in the Windows Remote Desktop Protocol (RDP)—two weeks after Microsoft releases the security patch. If exploited, the vulnerability could allow an attacker to easily cause havoc around the world, […]
Hackers Infect 50,000 MS-SQL and PHPMyAdmin Servers with Rootkit Malware
Cyber Security researchers at Guardicore Labs today published a detailed report on a widespread cryptojacking campaign attacking Windows MS-SQL and PHPMyAdmin servers worldwide. Dubbed Nansh0u, the malicious campaign is reportedly being carried out by an APT-style Chinese hacking group who has already infected nearly 50,000 servers and are installing a sophisticated kernel-mode rootkit […]
Hackers Stole Customers’ Credit Cards from 103 Checkers and Rally’s Restaurants
If you have swiped your payment card at the popular Checkers and Rally’s drive-through restaurant chains in past 2-3 years, you should immediately request your bank to block your card and notify it if you notice any suspicious transaction. Checkers, one of the largest drive-through restaurant chains in the United […]
Hackers are scanning for MySQL servers to deploy GandCrab ransomware
At least one Chinese hacking crew is currently scanning the internet for Windows servers that are running MySQL databases so they can infect these systems with the GandCrab ransomware. These attacks are somewhat unique, as cyber-security firms have not seen any threat actor until now that has attacked MySQL servers […]
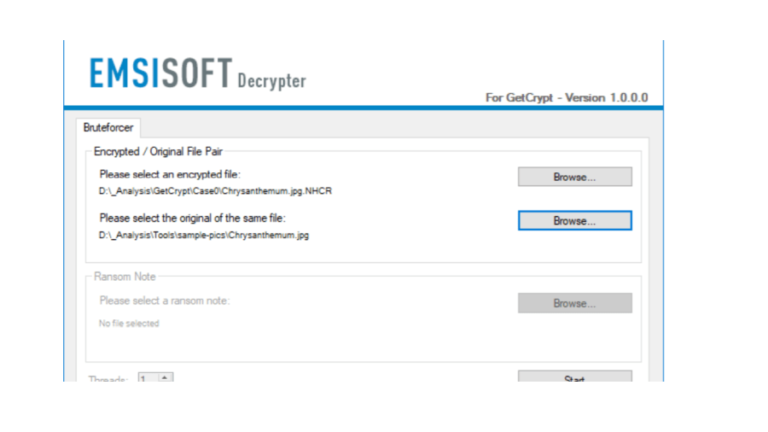
Emsisoft released a free Decrypter for the GetCrypt ransomware
For the second time in a few days, experts at Emsisoft released a free decrypter, this time to help victims of the GetCrypt ransomware Security experts at Emsisoft released a new decrypted in a few days, it could be used for free by victims of the GetCrypt ransomware to decrypt their files encrypted by the malware. […]
Playing Cat and Mouse: Three Techniques Abused to Avoid Detection
The experts at Yoroi-Cybaze Zlab described three techniques commonly implemented by threat actors to avoid detection. Introduction During our analysis we constantly run into the tricks cyber-attackers use to bypass companies security defences, sometimes advanced, others not. Many times, despite their elegance (or lack of it), these techniques are effective and actually […]
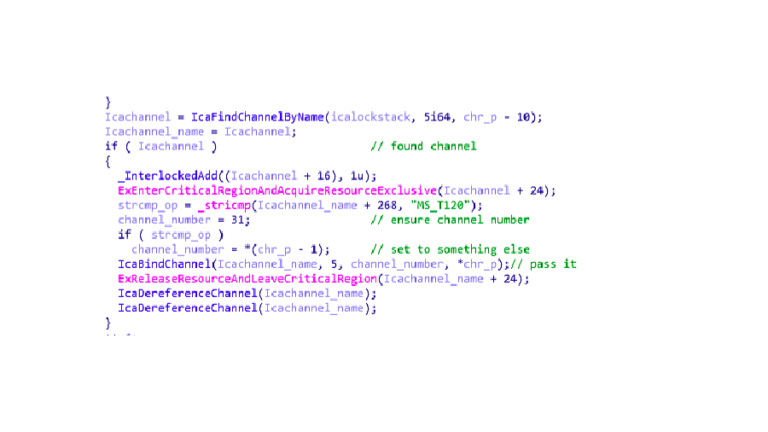
CVE-2019-0708 Technical Analysis (RDP-RCE)
CVE-2019-0708 Technical Analysis (RDP-RCE) Microsoft patch Tuesday this May (2019) comes with patch for critical RDP RCE Vulnerability, CVE-2019-0708 Remote Code Execution Vulnerability exists in Remote Desktop Services (RDP) pre-authentication and requires no user interaction Microsoft described it as “Wormable” so we could see new Wannacry hit the world ! […]
Unpatched Ethereum Clients expose the ecosystem to 51% Attack risk
Security researchers from SRLabs have published a report that analyzed the risks for Ethereum network caused by unpatched Ethereum clients. Researchers at SRLabs published a report based on ethernodes.org data, that revealed that a large number of nodes using the popular clients Parity and Geth is still unpatched. The expert discovered […]